
Building a Dedicated Console Access Server for Cisco Lab
Managing a Cisco lab with multiple routers and switches is much easier with a centralized console access server. In this...
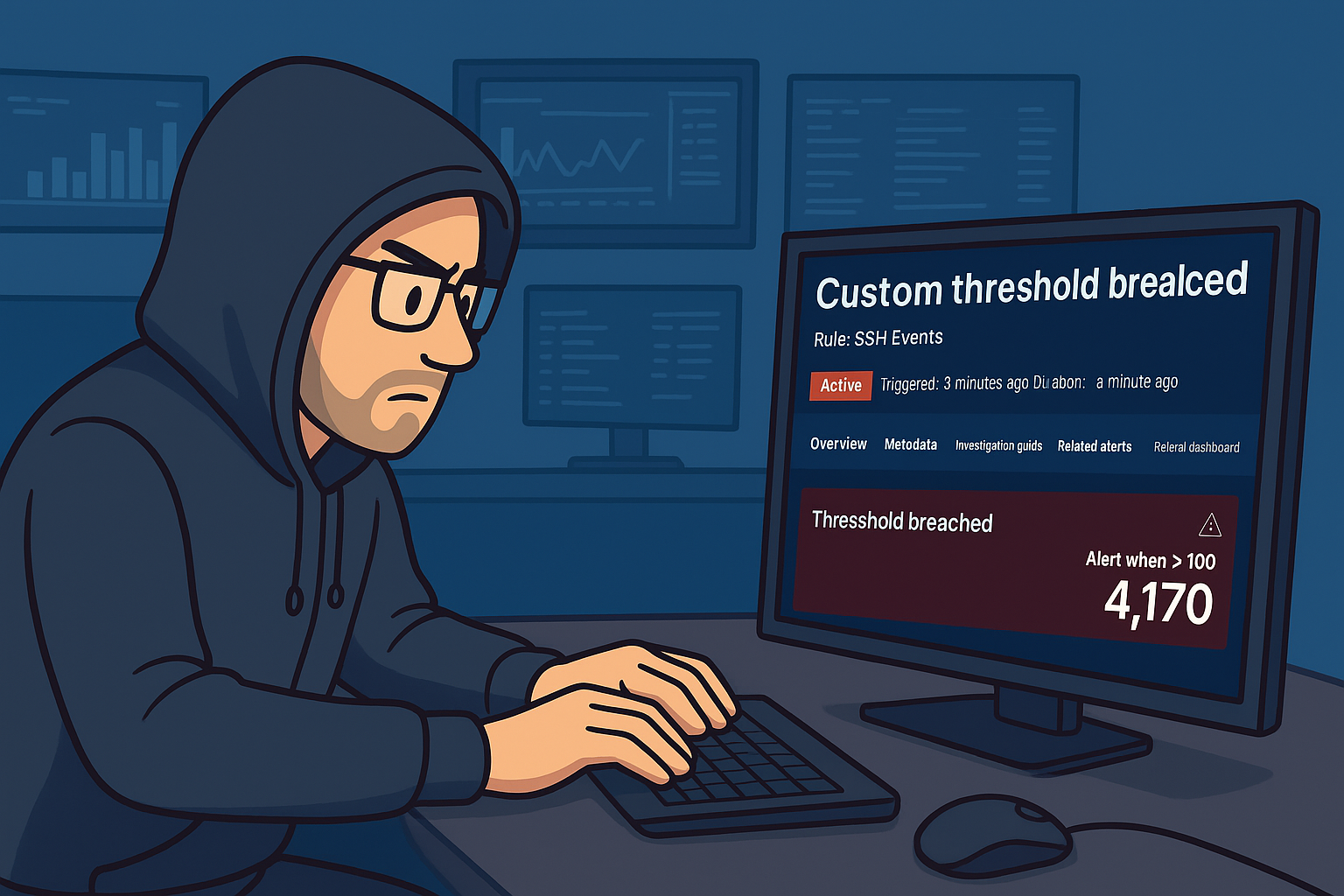
Basic SIEM Home Lab Using Elastic Cloud
Create an Elastic Account.Visit https://www.elastic.co and sign up for a free account using your email.2. Open the Elastic Cloud console...

Basics of Pivoting
In this post, we’ll walk through how to pivot from a compromised Metasploitable VM into a private network and use...

Security Lab Using EVE-NG (Part 1)
1. Install VMware Workstation PlayerDownload and install the latest version of VMware Workstation Player from the official website then create...

Introduction to Digital Forensics
Part 1 - IntroductionInterpol defines digital forensics as a branch of forensic science focused on identifying, acquiring, processing, analyzing, and...

Introduction to Threat Hunting
First, let us establish the concept and meaning of IOC . An Indicator of Compromise(IOC) is a data point used...

Introduction to OSINT
Open-source intelligence (OSINT) is more than just Googling information. While a quick search may provide basic answers, it often lacks...

Network Analysis
Wireshark is an open-source network packet analyzer that allows you to see all the network traffic being transmitted (sent/received) over...

Building Your Own Pentest Box: Part 3 – Ethical Hacking (Exploitation with Metasploit )
Important Disclaimer: Using these modules for anything other than testing on a system you have permission to exploit is illegal...

Building Your Own Pentest Box: Part 2 – Setting Up Kali Linux
2. Once completed, log in to the VM using the credentials below: Username: vagrant Password: vagrant 3. Check network settings...