Learn by Doing: Build CyberSkills with Hackmybox

Our mission is to inspire and empower tech enthusiasts to explore cybersecurity by creating hands-on labs.
Testimonials
Since I started working in IT a decade ago, there are just a handful of people I have high praise due their knowledge in the field or their work ethic. Ron is one of them - a real badass in Network and System - and apparently, killing it in Cybersecurity field. Dang.
Cyrus G - IT Analyst | OSCP Cyrustheitguy.com 🇦🇪
All the best this journey to pass your knowledge on cybersecurity to the world Great stuff.👍
Hadirman Shah - IT Desktop Support Specialist | Bakerbotts 🇸🇬
I had the privilege of working with Ron at two of my previous companies and I can confidently say that his passion for technology is truly inspiring.Whether it was troubleshooting complex issues or mentoring new team members. Ron was always there ready to help in every possible way, a mentor and a friend.
Alan Lastima - IT Team Lead Global Support | Rimkus Consulting Group 🇬🇧
Impressed by your Hackmybox site.
Shams Mohammad | PCIP, GCIH, GSEC, GFACT, CFCE
Thank you for the website, keep on researching and publishing!
Reynaldo Jr. Marquez - IT Security Specialist | Confidential | ECIH, CEH Practical | CCNA ,CCDA 🇵🇭
You have some really amazing stuff, proud of what you have achieved and look forward to more of your blogs!
Joel Guevara - Senior Cloud Architect | Bakerbotts 🇺🇸
Who We Are

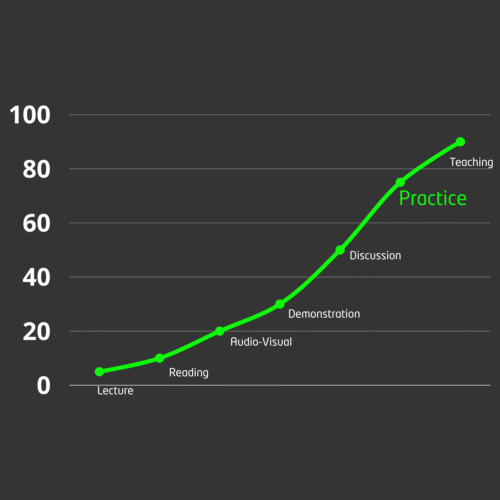
We believe the best way to learn is by doing, which is why we offer hands-on labs and real-world scenarios to sharpen skills and maximize potential.
To keep providing high-quality learning experiences, we need your support. Donations help cover domain, hosting, and resource costs. Donations are securely processed through Buy Me a Coffee, ensuring safe and effective support.
Join us in creating a brighter, safer digital future.
© 2025 HackMyBox. All rights reserved.
Soli Deo Gloria
