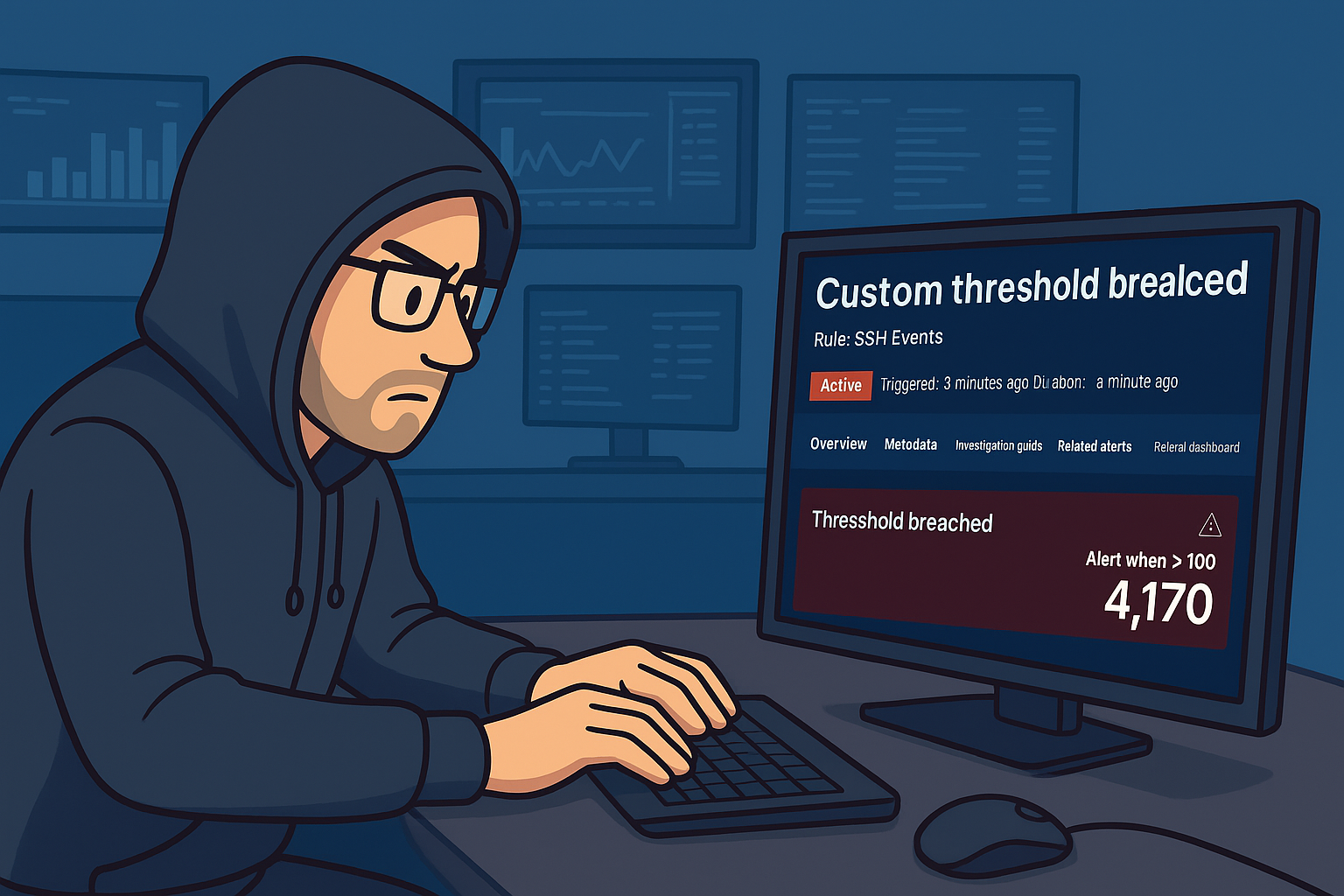
Basic SIEM Home Lab Using Elastic Cloud
Create an Elastic Account.Visit https://www.elastic.co and sign up for a free account using your email.2. Open the Elastic Cloud console...

Basics of Pivoting
In this post, we’ll walk through how to pivot from a compromised Metasploitable VM into a private network and use...

Attacking Domain Trusts
(Insights From HTB Academy)Think of a "domain" like a company's computer network. "Domain trusts" are like agreements that let users...

Exploring NoPac (CVE-2021-42278 & CVE-2021-42287)
Recently explored some vulnerabilities related to Active Directory environments, including NoPac , PrintNightmare, and PetitPotam . NoPac (CVE-2021-42278 & CVE-2021-42287) a...

DCSync
(Insights From HTB Academy)What is DCSync?DCSync is a technique used to steal the Active Directory (AD) password database by mimicking...

Abusing ACLs
(Insights From HTB Academy)Background : We already have control over a user (wley) whose NTLMv2 hash was retrieved using Responder. The...
ACL Enumeration Using Powerview & Bloodhound
(Insights From HTB Academy)What is ACL Enumeration?ACL (Access Control List): A list of permissions attached to an object (like a...

BloodHound: Tool for Analyzing and Securing Active Directory
(Insights from HTB Academy)From the previous module we learned credential enumeration techniques on Active Directory typically involve using a variety...

Enumerating , Retrieving Password Policies & Password Spraying
(Insights from HTB Academy)Objective : The section you provided outlines several techniques for enumerating and retrieving password policies in Active...

Active Directory Enumeration & Attacks
(Insights from HTB Academy)Part 1: LLMNR/NBT-NS PoisoningSecuring Active Directory (AD) is crucial for safeguarding a network's identity management system, which...