ACL Enumeration Using Powerview & Bloodhound
(Insights From HTB Academy)
What is ACL Enumeration?
ACL (Access Control List): A list of permissions attached to an object (like a user, group, or computer) in Active Directory.
Enumeration: The process of listing out these permissions to find potential weaknesses or misconfigurations that can be exploited.
Why is ACL Enumeration Important?
It helps attackers (or defenders) identify who has access to what in a network.
Misconfigured ACLs can allow attackers to escalate privileges, move laterally, or gain control over critical systems.
Tools
- PowerView: A PowerShell tool for querying Active Directory. https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1
- BloodHound: A graphical tool that maps out relationships and permissions in AD, making it easier to find attack paths
Key Steps in ACL Enumeration
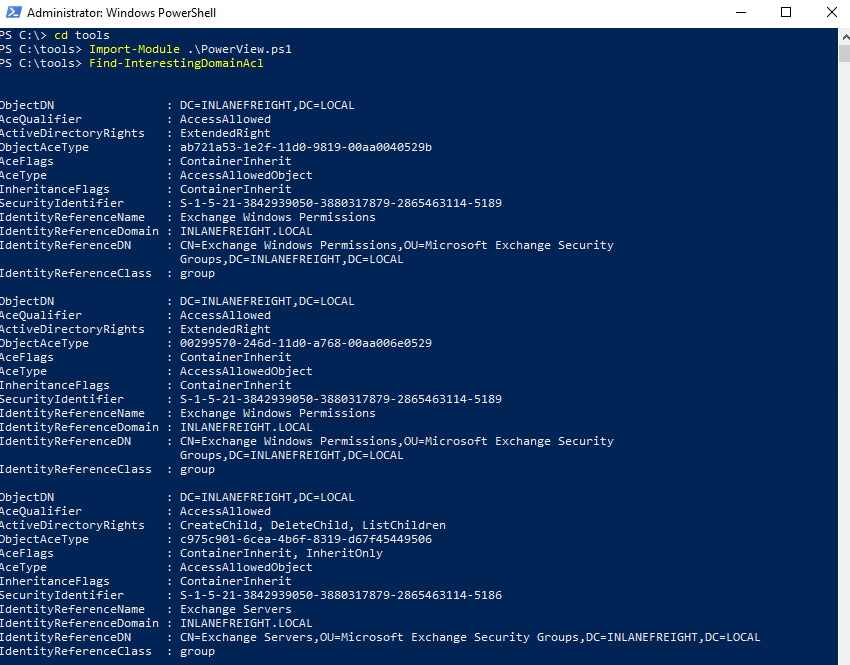
1.Find Interesting ACLs:
Use PowerView's Find-InterestingDomainAcl to list all ACLs in the domain.
This can return a lot of data, so it’s better to focus on specific users or groups.
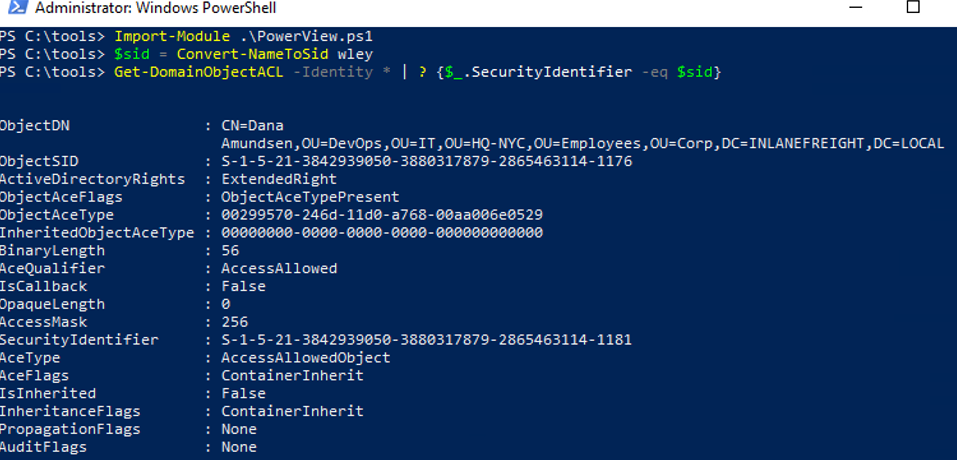
2.Targeted Enumeration:
Start with a user you control (e.g., wley).
Convert the username to a Security Identifier (SID) using Convert-NameToSid.
Use Get-DomainObjectACL to find objects the user has rights over.
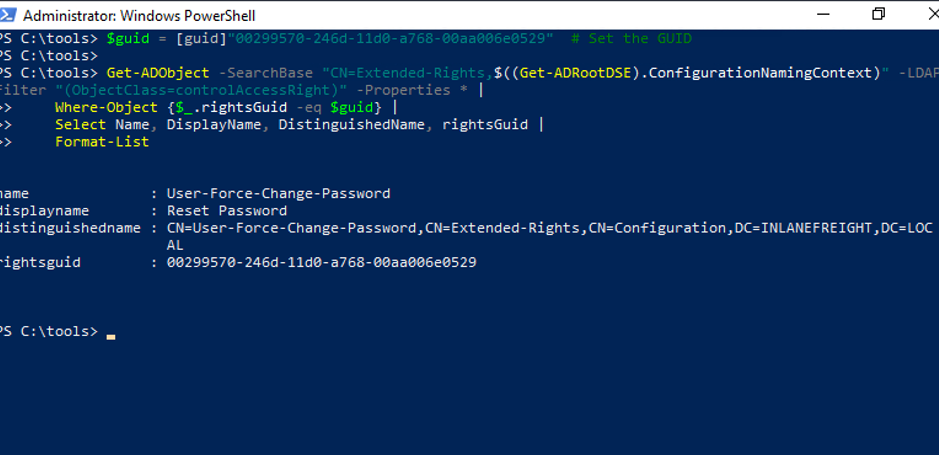
3.Resolve GUIDs:
ACLs often use GUIDs (e.g., 00299570-246d-11d0-a768-00aa006e0529) to represent permissions.
To convert GUIDs into human-readable names (e.g., User-Force-Change-Password) follow step below.
4.Exploit Misconfigured Permissions:
If a user has the User-Force-Change-Password right over another user, they can reset that user's password and take control of their account.
If a user has GenericWrite over a group, they can add themselves to that group and inherit its permissions.
We can also try to enumerate ACLs visually using BloodHound.
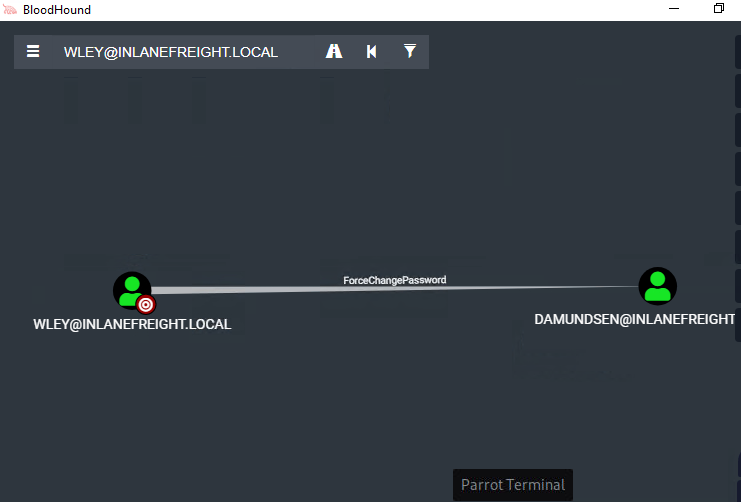
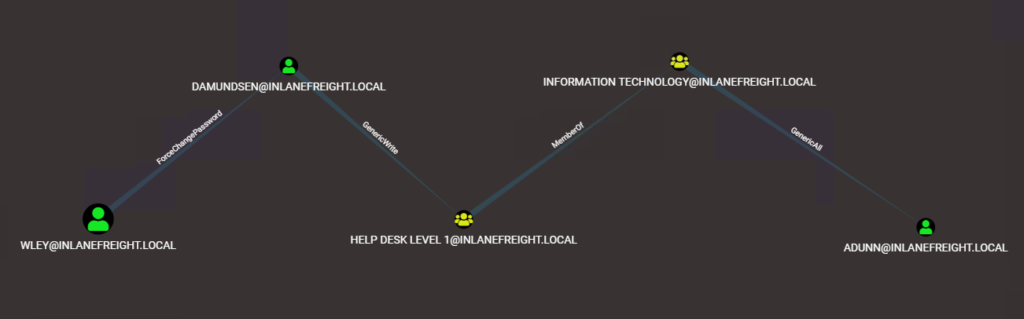
5.Follow the Attack Chain by using BloodHound to visualize the attack path.
- User wley can reset the password for damundsen.
- damundsen has GenericWrite over the Help Desk Level 1 group.
- The Help Desk Level 1 group is nested in the Information Technology group.
- The Information Technology group has GenericAll over user adunn.
- adunn has DCSync rights, which can be used to extract password hashes for the entire domain.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below.


