BloodHound: Tool for Analyzing and Securing Active Directory

(Insights from HTB Academy)
From the previous module we learned credential enumeration techniques on Active Directory typically involve using a variety of methods to identify valid usernames and passwords on a network. These methods can include:
• Password spraying: This technique involves trying a list of common passwords against a large number of usernames.
• Hash cracking: This technique involves stealing hashed passwords from a network and then using a computer program to try to crack the hashes into plain text passwords.
• Social engineering: This technique involves tricking users into revealing their passwords or other sensitive information.
TOOLS
BloodHound: A free and open-source tool that can be used to visualize Active Directory relationships. BloodHound can be used to identify potential attack paths and to identify users who have high-level privileges.
SharpHound: A C# library that can be used to collect data from Active Directory. SharpHound can be used to collect the same data as PowerView, but it can also be used to collect additional data, such as the password hashes of users.
Components of the Command:
SharpHound.exe is part of the BloodHound toolset, which is used for Active Directory (AD) enumeration and mapping attack paths.
It helps identify misconfigurations and permissions in Active Directory environments that can lead to privilege escalation or lateral movement.
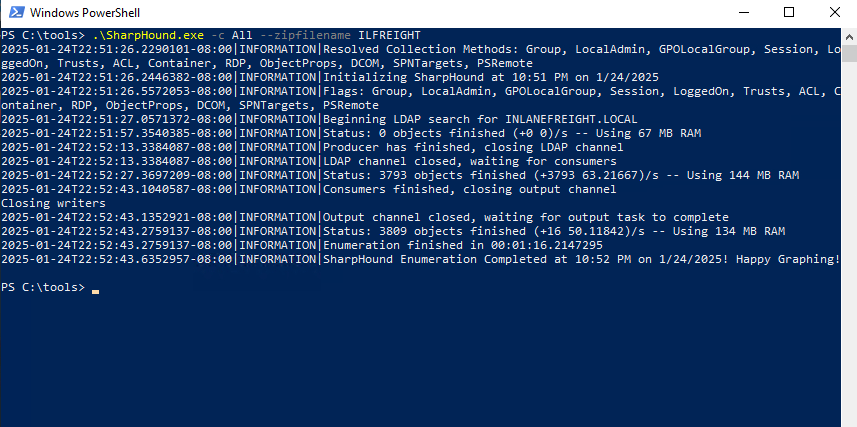
Step 1:
\SharpHound.exe -c All --zipfilename ILFREIGHT
The .\ indicates that the executable file SharpHound.exe is located in the current directory (. refers to the current directory).
-c All:
The -c flag specifies the collection method or category of data to collect.
All means that SharpHound will collect all available data during the scan, which can include:
- Group memberships
- Admins on domain controllers
- Trusts
- Sessions
- Other useful information for mapping attack paths within Active Directory
This is a comprehensive scan that tries to collect all relevant data.
--zipfilename ILFREIGHT:
This option specifies the name of the output zip file. In this case, the output will be saved as a .zip file named ILFREIGHT.
The resulting zip file will contain the collected information (e.g., group memberships, trusts, and relationships) in a format that can be used later for analysis
Step 2:
Run BloodHound then upload the data collected using SharpHound from step 1.
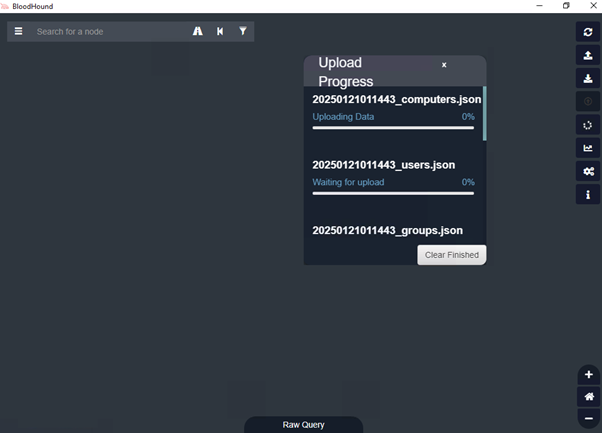
Once the upload is complete, click on the Analysis tab. Here, you can see the pre-built queries. In this example will select Kerberostable accounts.
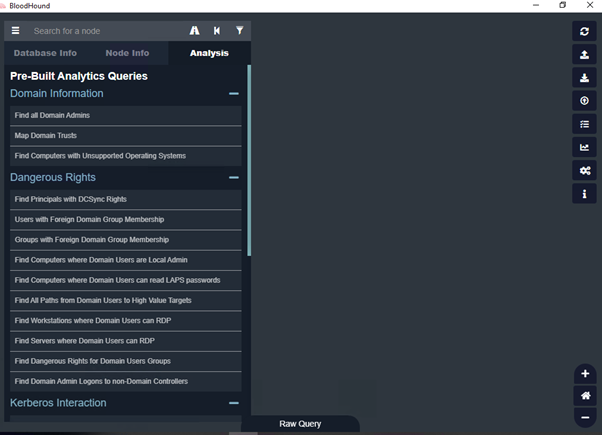
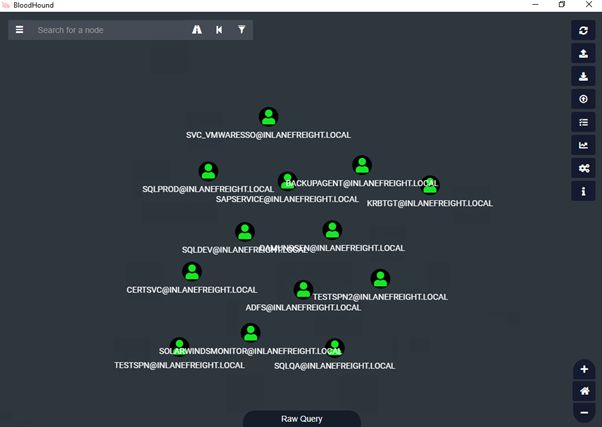
Feel free to try all queries , another example is "Find all Domain Admins" under Domain information.
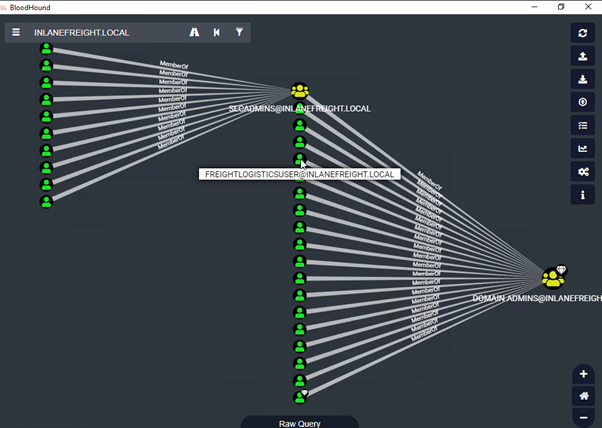
In conclusion, Active Directory (AD) is crucial for managing IT environments, but it can present security risks like privilege creep and unsafe configurations that may be exploited by attackers.
BloodHound helps by analyzing AD environments to identify potential vulnerabilities, allowing Red Teamers to find paths to higher privileges and lateral movement while Blue Teamers can use it to audit and secure AD configurations.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below


