Footprinting Microsoft SQL

(Insights from HTB Academy)
Microsoft SQL (MSSQL) is Microsoft's SQL-based relational database system, widely used on Windows, especially with .NET applications.
Security and Footprinting: Vulnerabilities arise from weak credentials, lack of encryption, and self-signed certificates. For security assessments, tools like Nmap and Metasploit (mssql_ping) provide valuable information about server configurations. Impacket’s mssqlclient.py enables direct interaction with the database using credentials.
This overview highlights key MSSQL features, vulnerabilities, and tools for understanding and securing MSSQL environments.
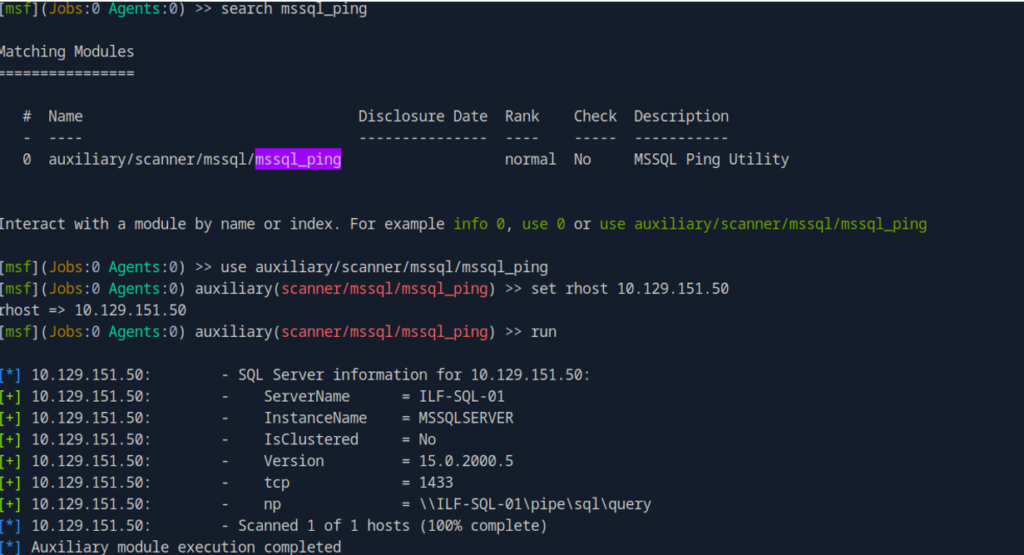
1. On the Metasploit console, search for the mssql_ping module and load it.
msf6 > use auxiliary/scanner/mssql/mssql_ping
2. Set the RHOST to defines the target IP address.
msf6 auxiliary(scanner/mssql/mssql_ping) > set RHOSTS 10.129.151.50
3. Run the module to check if the MSSQL service is available:
msf6 auxiliary(scanner/mssql/mssql_ping) > run
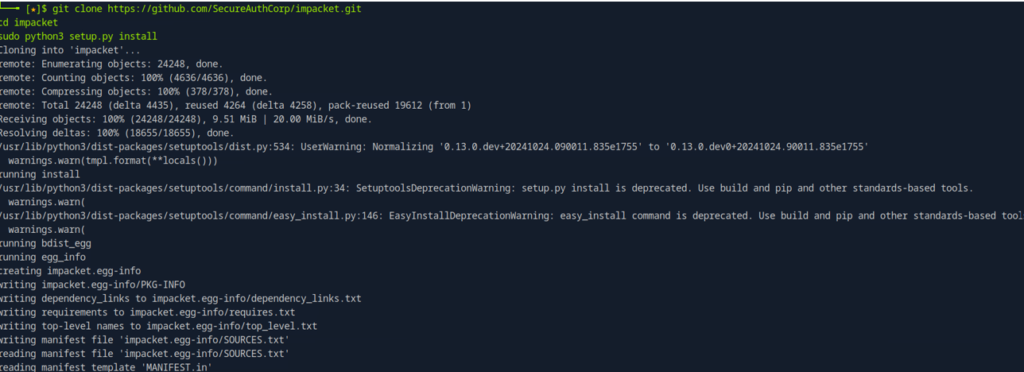
4. Install Impacket (if not already installed):
git clone https://github.com/SecureAuthCorp/impacket.git
cd impacket
sudo python3 setup.py install
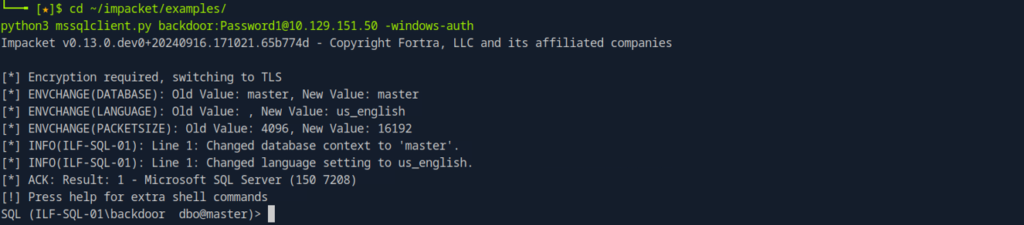
5. Run mssqlclient.py with Windows Authentication.
python3 /path/to/impacket/examples/mssqlclient.py backdoor:Password1@10.129.151.50 -windows-auth
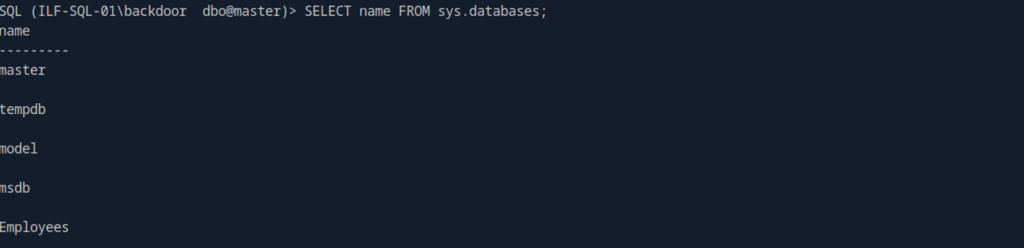
6. Retrieve the names of all databases on the SQL Server
SQL> SELECT name FROM sys.databases;
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below

