Footprinting -DNS

(Insights from HTB Academy)
DNS Functionality: Key thing is to understand how DNS works . DNS translates computer names into IP addresses. It converts human-readable domain names into machine-readable IP addresses, which is crucial for the functioning of the internet. For example, your web browser queries DNS to load internet resources effectively.
Linux vs. Microsoft DNS: It's been a while since I configured DNS on Linux, as I usually deploy DNS using Microsoft Server. While both serve the same primary function—resolving names to IP addresses—their configurations and management interfaces differ significantly. Microsoft DNS is often managed through the GUI of Windows Server, whereas Linux DNS configurations are typically handled through configuration files like named.conf for BIND. I need some time to explore and test these tools with Microsoft DNS servers.
Tools:
- Dig: Good for querying DNS records and performing lookups.
- Dig-AXFR: Correctly identified as a method for zone transfers, allowing you to retrieve the complete zone file from a DNS server.
- Nslookup: A classic tool for querying DNS
- Dnsenum: Used for DNS enumeration, which is critical for gathering information about a domain.
Task:
In the module, we are tasked with querying the target DNS using its IP address and enumerating details for the 'inlanefreight.htb' domain.
Using the dig tool, we can find the required details. The key is to keep querying all subdomains.
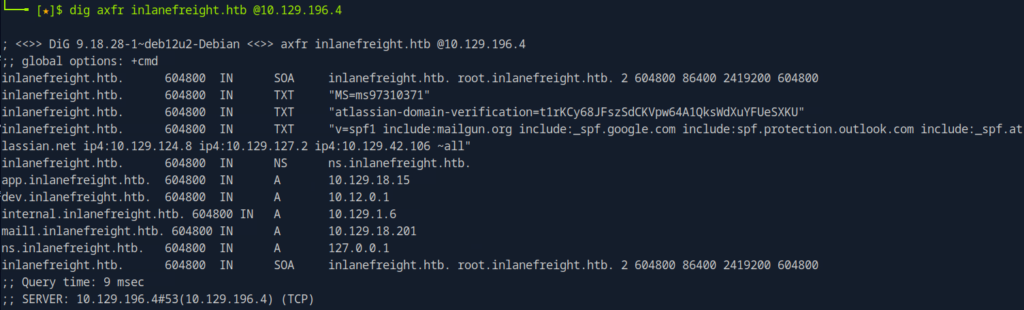
Syntax :
dig axfr inlanefreight.htb @10.129.196.4
- DiG: This is the command-line tool used for querying DNS records.
- axfr: This indicates a request for a zone transfer, which retrieves all DNS records for the specified domain.
- inlanefreight.htb: The target domain for which the DNS records are being queried.
- @10.129.251.51: This specifies the DNS server to query.
Interpreting Results :
- SOA Record: Indicates the authoritative server for the domain and includes administrative contact information.
- TXT Records: Contain various verification and policy information, including Microsoft and Atlassian verification tokens, and an SPF record for email security.
- NS Record: Specifies the name server (ns.inlanefreight.htb) responsible for the domain.
- A Records: Map several subdomains (e.g., app, dev, internal, mail1, ns) to their corresponding IP addresses.
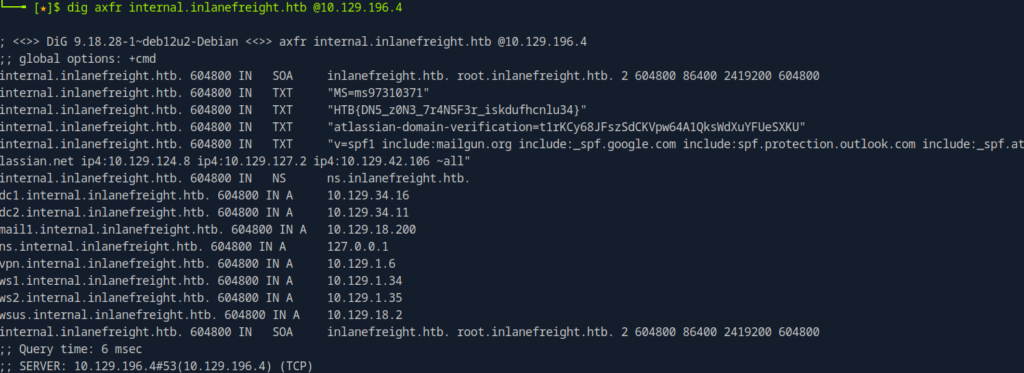
Dig subdomains :
dig axfr internal.inlanefreight.htb @10.129.196.4
Dnsenum - is a multithreaded perl script to enumerate DNS information of a domain.
source: https://www.kali.org/tools/dnsenum/
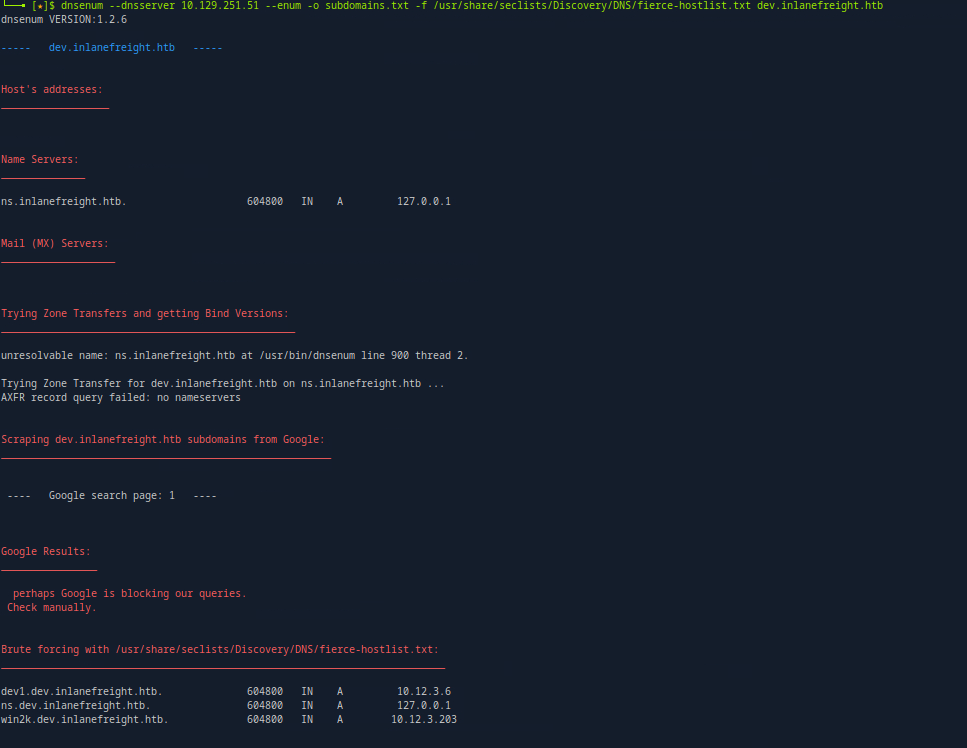
Syntax:
dnsenum --dnsserver 10.129.251.51 --enum -0 subdomains.txt -f /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt dev.inlanefreight.htb
The command will query the DNS server to find and list subdomains then saving the results to a file. Details below:
- dnsenum: This is the command for the DNS enumeration tool, which is used to gather information about DNS records.
- --dnsserver 10.129.251.51: This option specifies the DNS server to query for information. In this case, it’s set to 10.129.251.51.
- --enum: This flag tells dnsenum to perform enumeration of DNS records, such as subdomains.
- -o subdomains.txt: This option specifies the output file where the results (found subdomains and their records) will be saved. Here, it’s named subdomains.txt.
- -f /usr/share/seclists/Discovery/DNS/fierce-hostlist.txt: This option points to the wordlist that dnsenum will use to search for subdomains. The specified wordlist is fierce-hostlist.txt, which contains common subdomain names.
- dev.inlanefreight.htb: This is the target domain that the tool will be enumerating. The command will look for subdomains associated with dev.inlanefreight.htb.
In summary, we see how DNS functions and how tools like Dig and Dnsenum are essential for effective footprinting and enumeration of domain information.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below

