Introduction to OSINT

Open-source intelligence (OSINT) is more than just Googling information. While a quick search may provide basic answers, it often lacks depth and completeness. Effective OSINT requires setting clear objectives, using diverse and verified sources, and applying advanced search techniques while meticulously documenting and cross-checking data for accuracy.
Let’s explore the "Introduction to OSINT" by Security Blue Team, along with additional resources gained from in-depth research. Remember to respect legal and ethical boundaries, stay updated with new tools, and apply critical thinking to evaluate the context and reliability of the information you gather.
Part 1: Intelligence
In this section, we explore the Intelligence Lifecycle and how raw data is transformed into actionable intelligence and examine how open-source intelligence (OSINT) operates.
Collection: The first step involves gathering publicly available information from various online sources, including social media, news articles, and government reports. This can be done manually or through automated tools.
Processing: Next, filter and categorize the collected data to eliminate duplicates, irrelevant content, and inaccuracies. Organize the information based on its relevance and importance.
Analysis: Analyze the data to identify trends, patterns, and relationships. Utilize tools such as data visualization, data mining techniques, and natural language processing (NLP) to extract meaningful insights.
- Dissemination: The final step is to share the insights with decision-makers. This can be achieved through detailed reports or organizational briefings.
Part 2: Securing Yourself Online
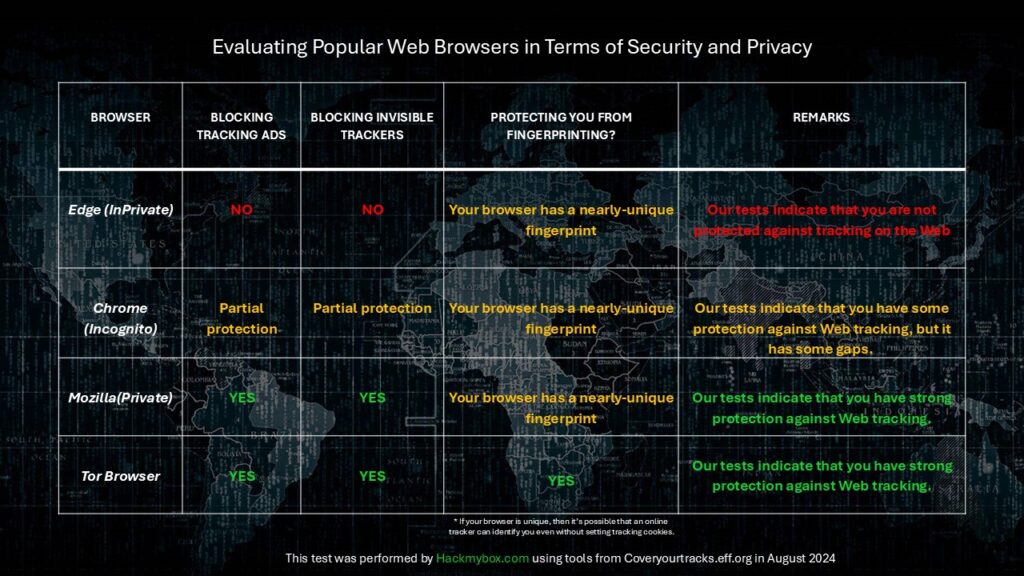
This section explores how we are tracked online and provides strategies for reducing our digital footprint. Examples of tracking mechanisms include fingerprinting, IP addresses, cookies, and browsers, all of which are used to monitor, identify, and collect information about users' online activities and behaviors.
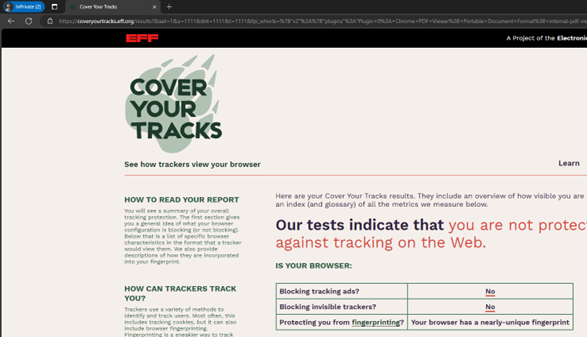
The course covered tools for evaluating browsers and assessing their level of anonymity. We tested several browsers using https://coveryourtracks.eff.org. Click on the image below to view the details.
Edge (InPrivate)
Chrome(InCognito)
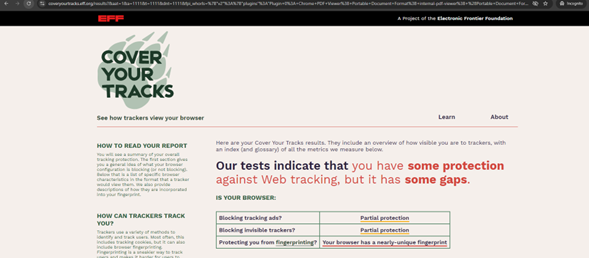
Mozilla (Private Mode)
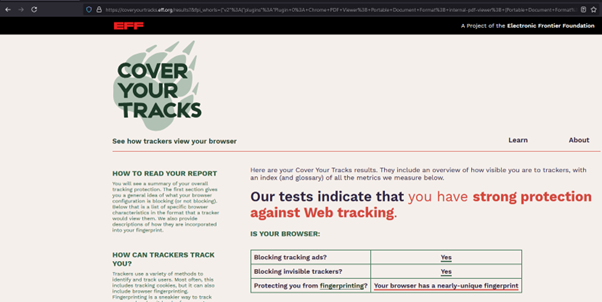
Tor Browser
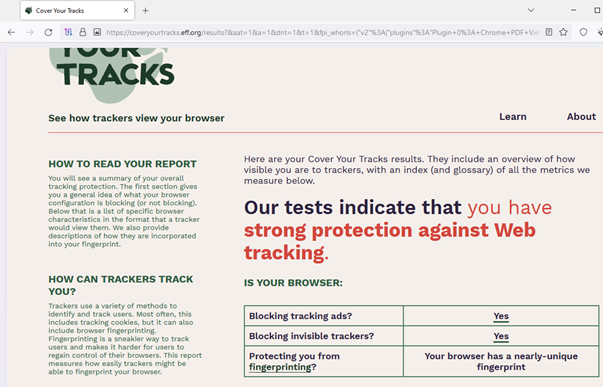
Part 3: Tools and Services
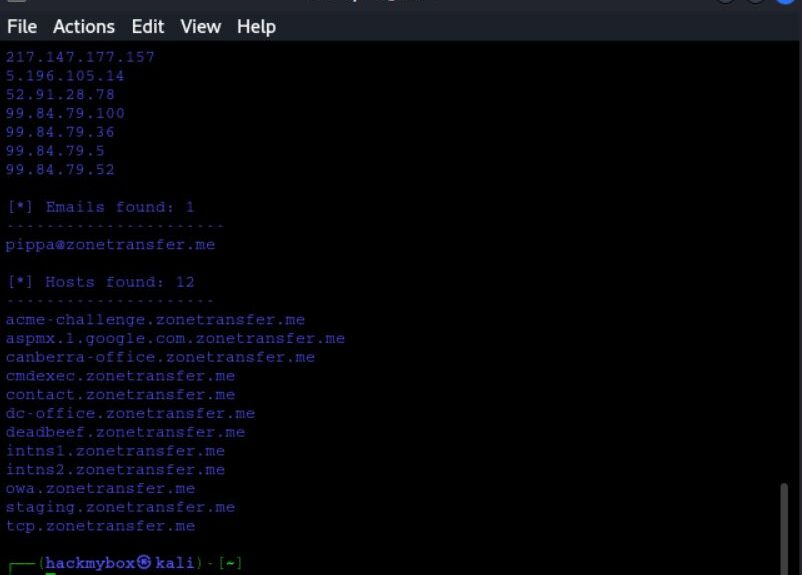
- The Harvester: This is an open-source tool used in information gathering or reconnaissance. It collects data from various public sources like search engines, social media platforms, and public databases to gather information such as emails, subdomain names, IPs and URLs , open ports/ banners & employee names using multiple public data sources.
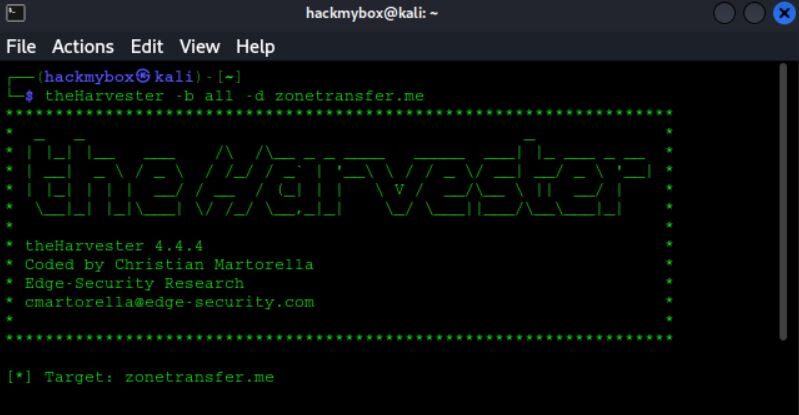
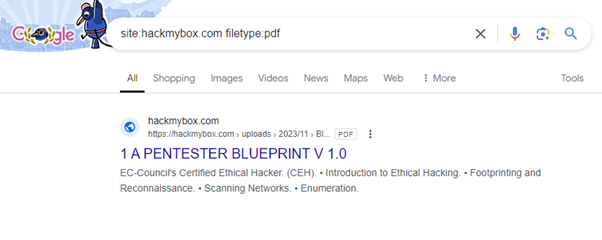
2. Google Dorks: These are advanced search queries used in Google to find specific information that might not be easily accessible through regular searches. By using special operators and syntax, users can uncover sensitive data, vulnerabilities, and other valuable information.

3.Maltego is a powerful open-source intelligence (OSINT) used for gathering and visualizing information from various sources. It helps users uncover relationships between people, groups, websites, and other entities by creating detailed graphical representations of the data. This tool is commonly used in cybersecurity, investigations, and intelligence to map out and analyze complex networks of information.
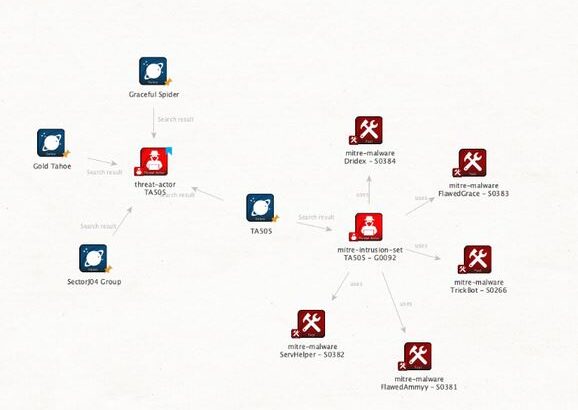
Additional resources : Maltego: The Ultimate OSINT & Cyber Investigation Tool (youtube.com) by Gary Ruddell
4.OSINT Framework: The OSINT (Open Source Intelligence) Framework is a collection of tools, resources, and techniques used to gather publicly available information for investigative purposes. It provides a structured approach to finding and analyzing open-source data across various domains, including social media, websites, and databases.
See the link below for a summary chart of useful tools for OSINT from Social Links.
5.Reverse Image Searching (TinEye, Google): These tools allow users to upload an image or provide an image URL to find out where that image appears on the web. They are useful for tracking the origin of an image, finding higher resolution versions, or verifying the authenticity of an image.