Building Your Own Pentest Box: Part 1 – Setting Up Metasploitable 3

Background: Metasploitable3 is a virtual machine (VM) purposefully designed with numerous security vulnerabilities. It serves as a target for testing exploits using Metasploit.
My hardware details: I’m using a Dell T320 with 48GB of memory, running an Intel(R) Xeon(R) CPU E5-2403 v2 processor, and Windows 10 Pro Version 10.0.19045 Build 19045. However, this setup can be installed on any laptop or desktop with a VT-x/AMD-V supported processor and preferably at least 8 to 16GB of memory.
Software requirements:
- Packer
- Vagrant
- Vagrant Reload Plugin
- VirtualBox
1. Download and install VirtualBox (version 7.0.18) from the link below. Proceed with the default settings until the installation completes.
https://www.virtualbox.org/wiki/Downloads

2.Clone this repository and navigate to the main directory, or alternatively, download the ZIP file and save it to your desktop.
https://github.com/rapid7/metasploitable3

3. Download Packer (version 1.9.4) from the link provided below. Create a folder named ‘Packer’ under Program Files and paste the downloaded files into it.
https://developer.hashicorp.com/packer/install
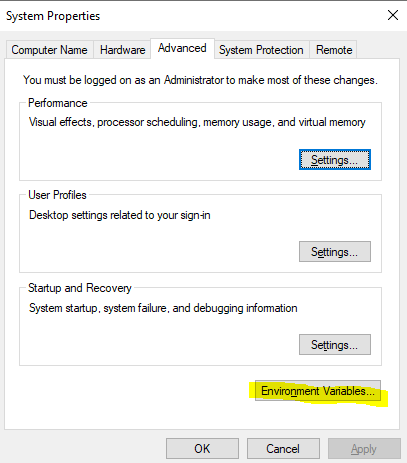
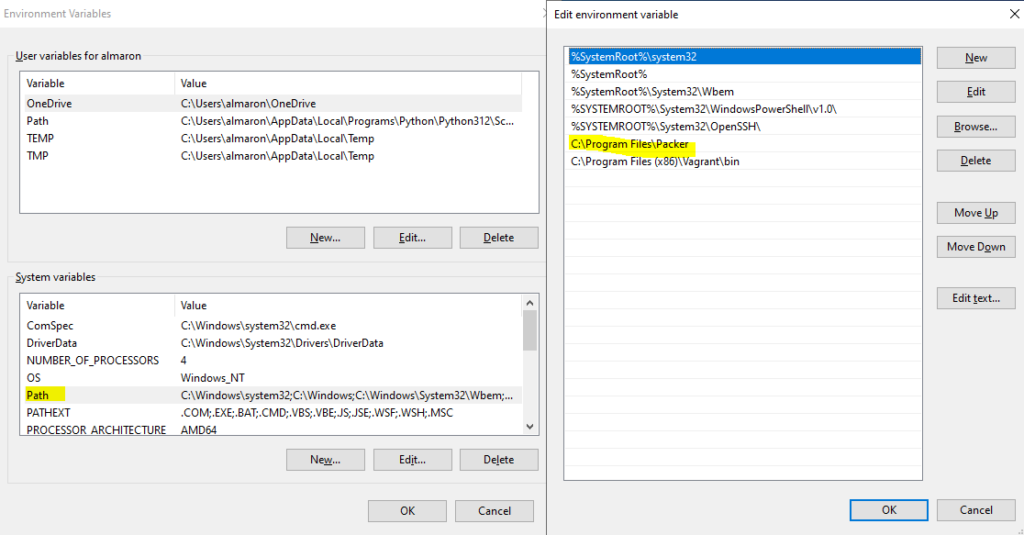
4. Configure environment variables: Go to Control Panel > System > Advanced System Settings > Environment Variables. Edit the ‘Path’ variable, then add the entry ‘C:\Program Files\Packer’.
5. Download and install Vagrant 2.4.1 from the link provided below. Proceed with the straightforward installation process by accepting the defaults until it finishes.
Install | Vagrant | HashiCorp Developer
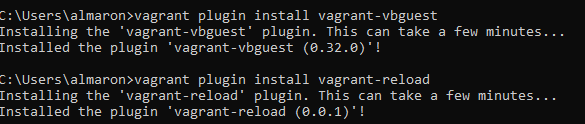
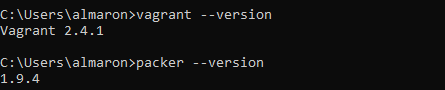
7. Open the command prompt (cmd) and install the Vagrant plugins. Test by checking the installed version.
vagrant plugin install vagrant-vbguest
vagrant plugin install vagrant-reload
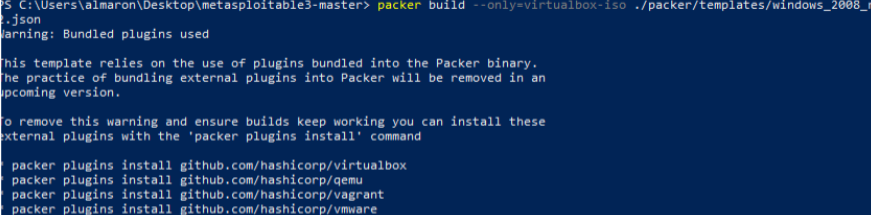
8. In PowerShell, execute the following Packer command to build the base VM image. Once the process is complete, you will see logs displayed as shown below:
Set-ExecutionPolicy Bypass
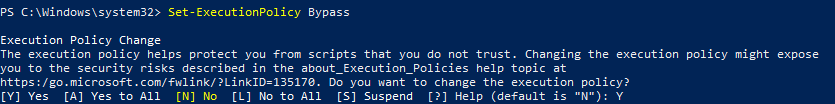
packer build –only=virtualbox-iso ./packer/templates/windows_2008_r2.json
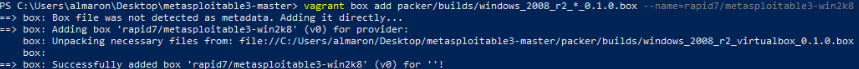
9. After creating the base Vagrant box, you need to add it to your Vagrant environment. This can be accomplished with the following command:
vagrant box add packer/builds/windows_2008_r2_*_0.1.0.box –name=rapid7/metasploitable3-win2k8.
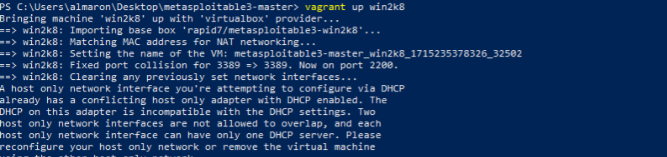
10. To start the VM, run the command vagrant up win2k8
11. Once this process is complete, you can open the VM in VirtualBox and log in. The default credentials are:
Username: vagrant
Password: vagrant
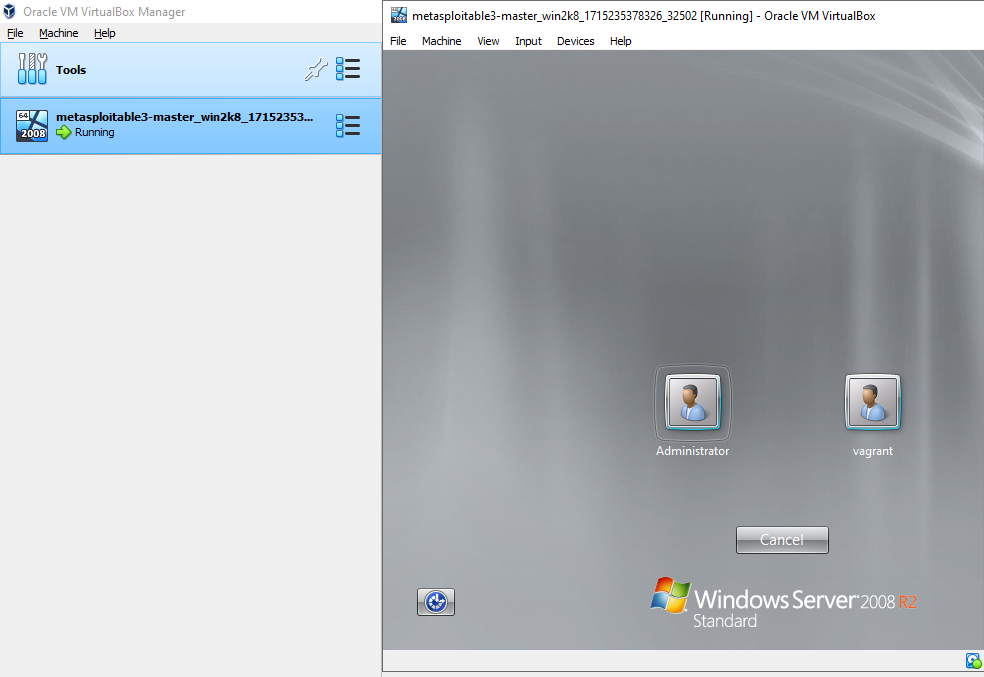
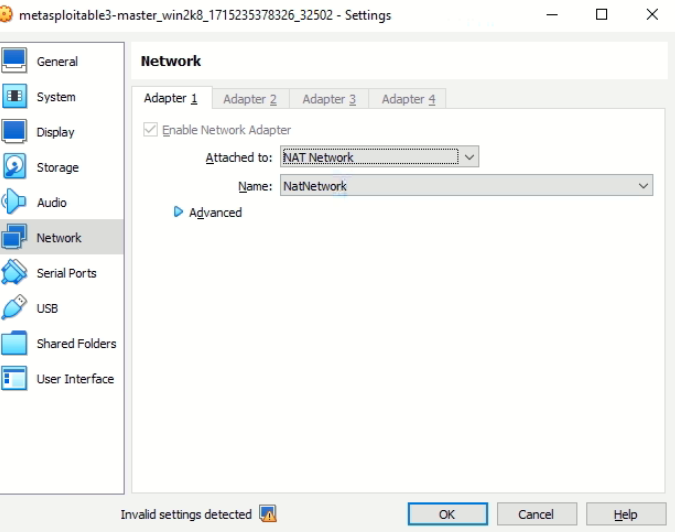
12. Lastly, check the VirtualBox VM settings. The recommended network setting for security purposes is NAT Network.
Go to File -> Tools -> Network Manager -> Create
Next time, we’ll be setting up Kali Linux on a VirtualBox and exploring how to utilize tools for penetration testing.
Thank you, everyone, and God bless!