Microsoft Defender For Endpoint Part 2

Vulnerability Discovery and Remediation with Microsoft Defender & Intune
Overview: Last time, we installed Microsoft Defender, identified vulnerabilities, and viewed recommended actions. This post will show you how to remediate potential risks using Intune.
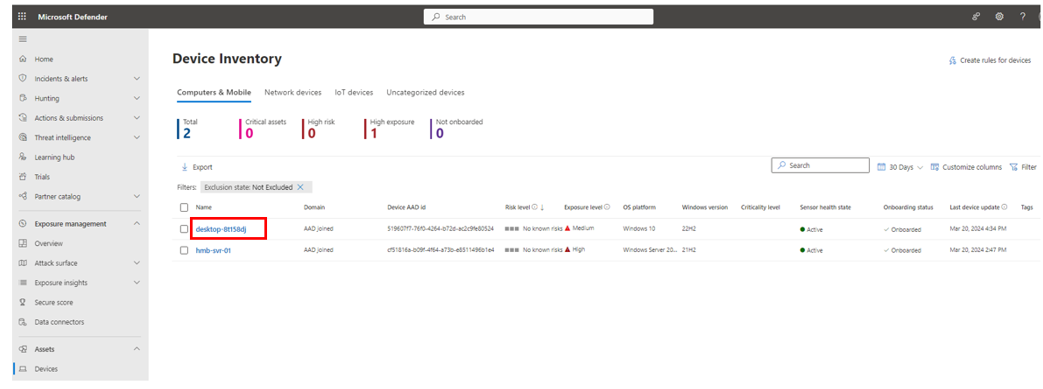
1. In Microsoft Defender, navigate to Devices -> Device Inventory. Click on the target device.
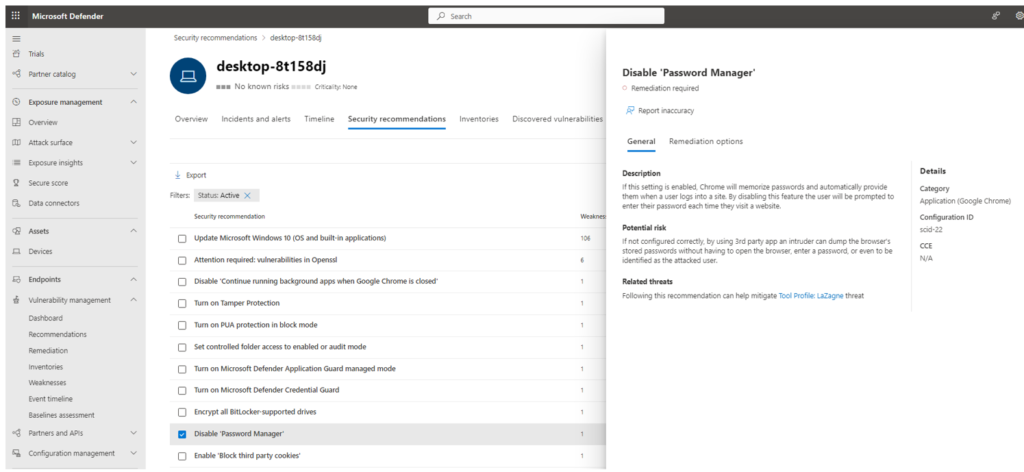
2. From the device’s Security Recommendations, select “Disable Password Manager.” On the right pane, it will show the description, potential risks, and related threats.
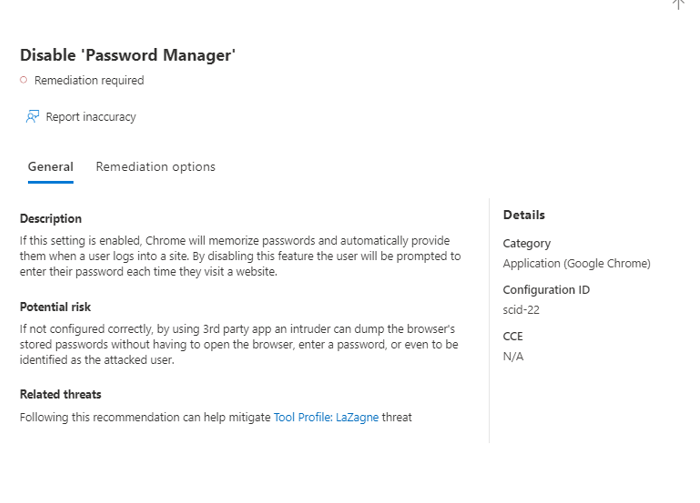
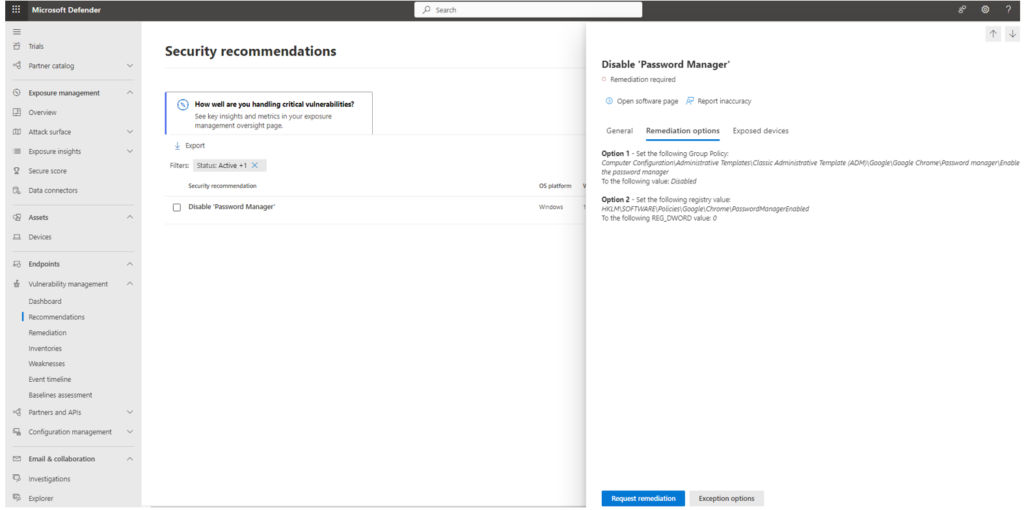
3. Click on “Remediation options” and then click on “Request remediation” to track the activity.
(Request remediation is useful for large IT groups, especially if you have separate teams managing vulnerabilities)
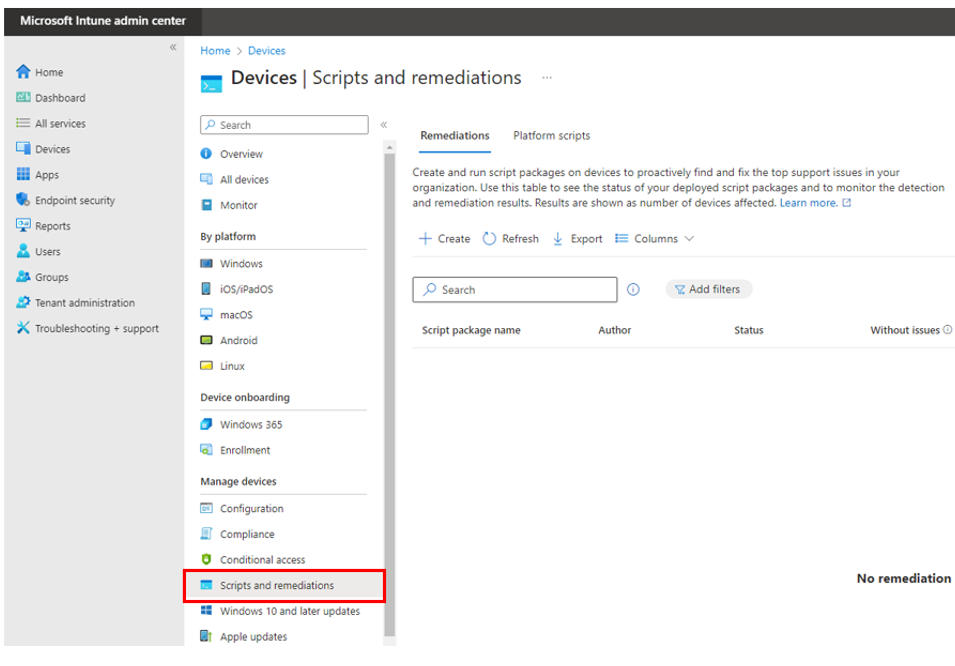
4. In the Microsoft Intune Admin Center, navigate to “Scripts and Remediations then click “Create”
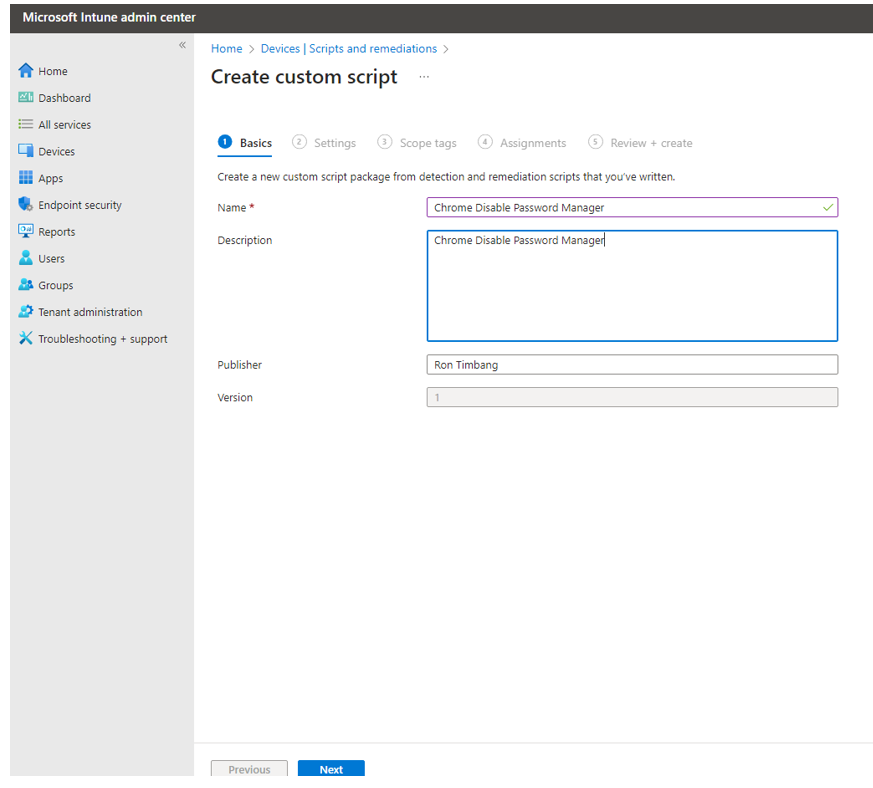
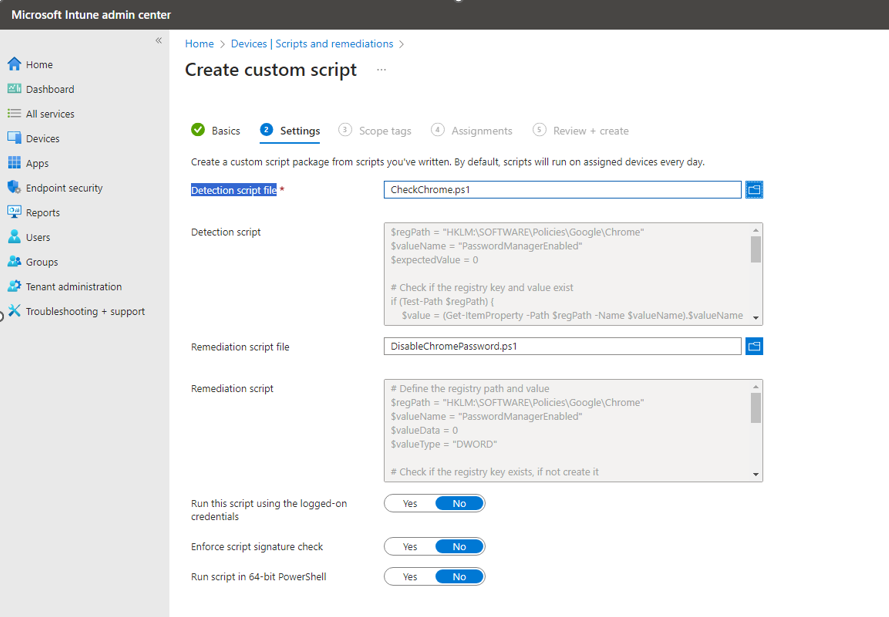
5. Enter the Basic information as seen below.
6. For the detection script file named CheckChrome.ps1, it checks if the device is compliant. Return 0 if the device is compliant; otherwise, return 1, triggering the Remediation script for implementation.
For more information see Microsoft article: https://learn.microsoft.com/en-us/mem/intune/fundamentals/remediations
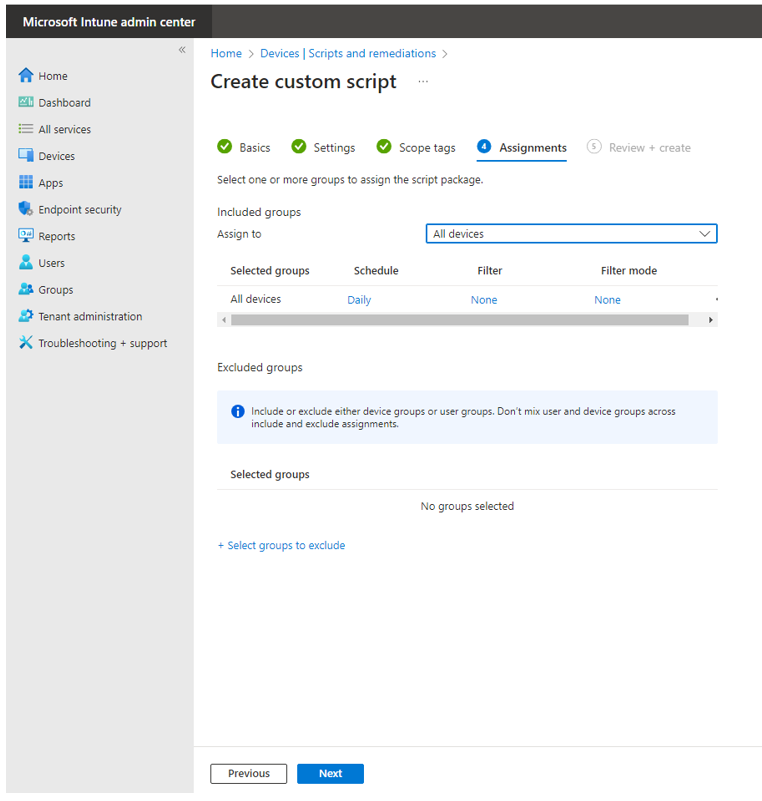
7. For testing purposes only, assign it to all devices.
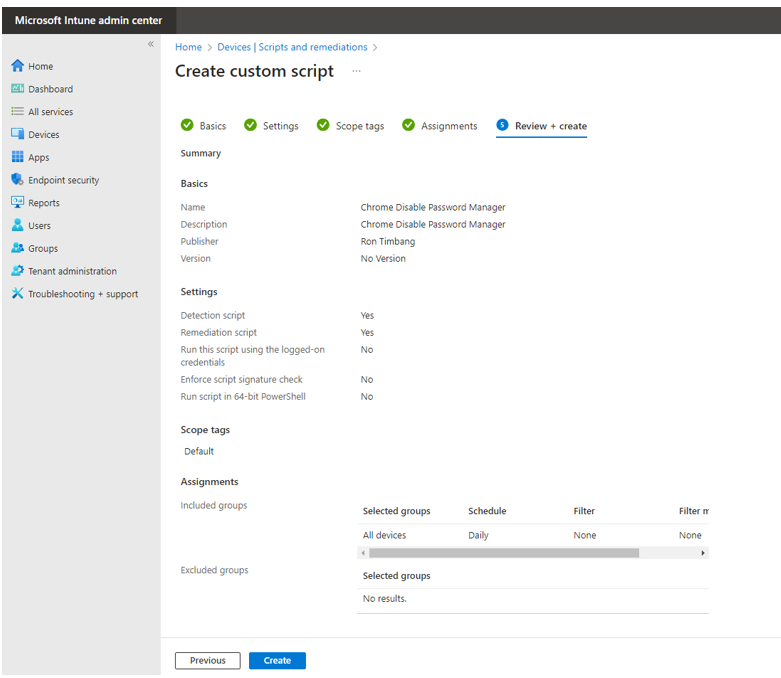
8. Click create
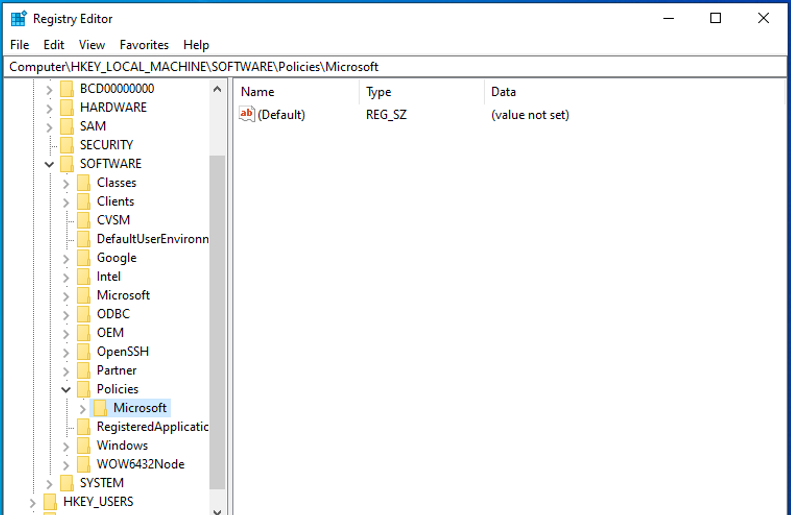
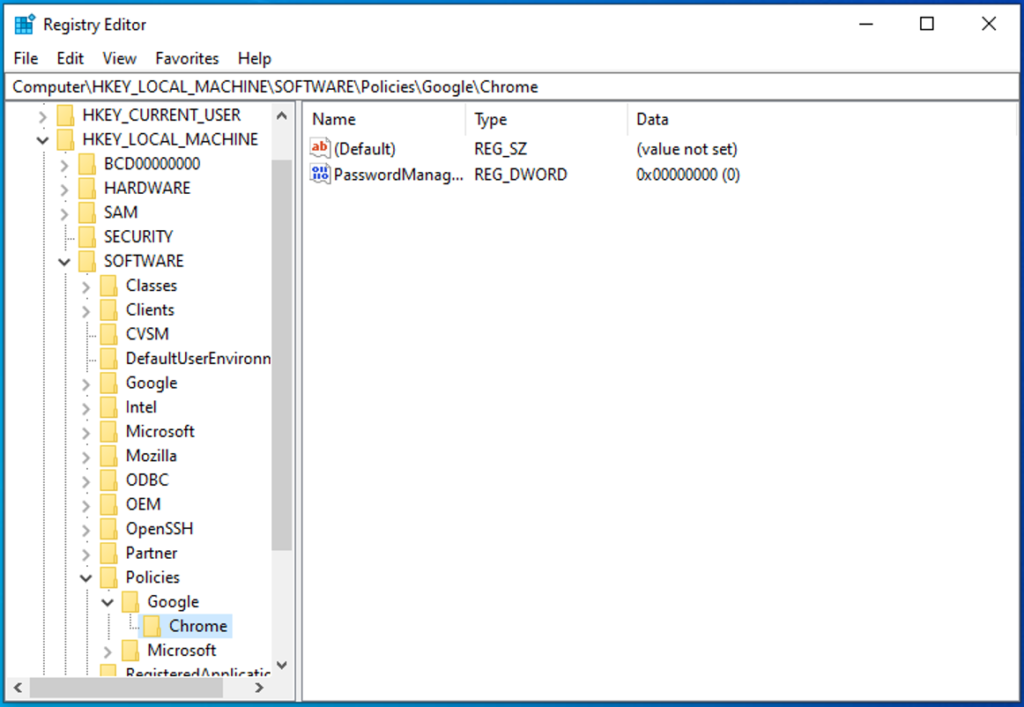
9. See below registry before running the remediation script.
9. Finally go to Device and “Run Remediation”.
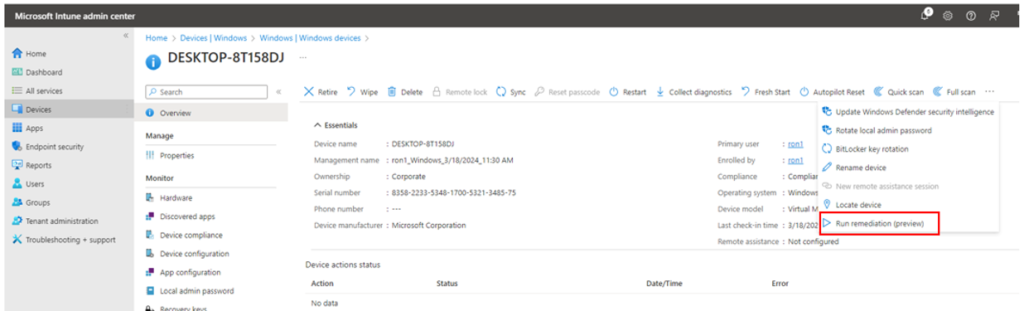
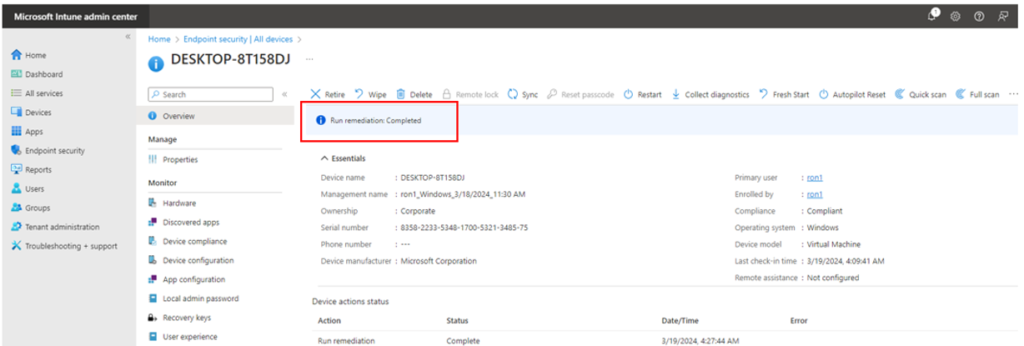
9. Notice ‘Run remediation completed’ if successful.
10. Check registry changes after running remediation.
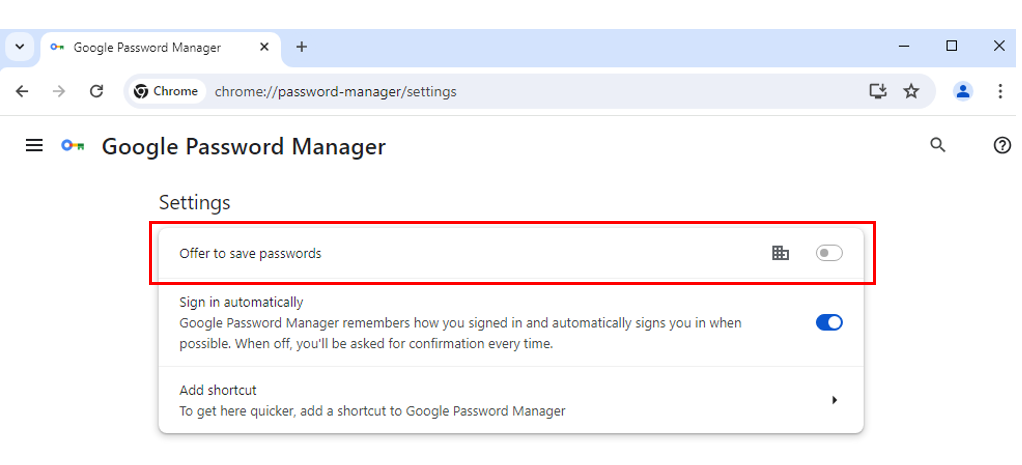
11. Open Chrome; the option to save passwords is now disabled.