Introduction to Threat Hunting

First, let us establish the concept and meaning of IOC . An Indicator of Compromise(IOC) is a data point used in cybersecurity to identify signs of malicious activity. Examples include file hashes, IP addresses, domain names, registry keys, URLs, and email addresses associated with threats. IOCs help detect, analyze, and respond to security incidents by providing evidence of potential breaches or malicious behavior.
In this lab by Security Blue, we will focus on file hashes in our threat hunting. File hashes are unique identifiers for files, such as MD5, SHA1, or SHA256, that can help identify known malicious files.
1.The first step is to download and install the necessary tools from the link below:
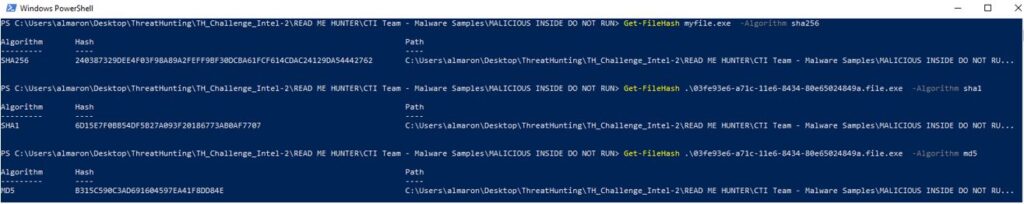
2. The next step is to obtain the hash values from the provided files.
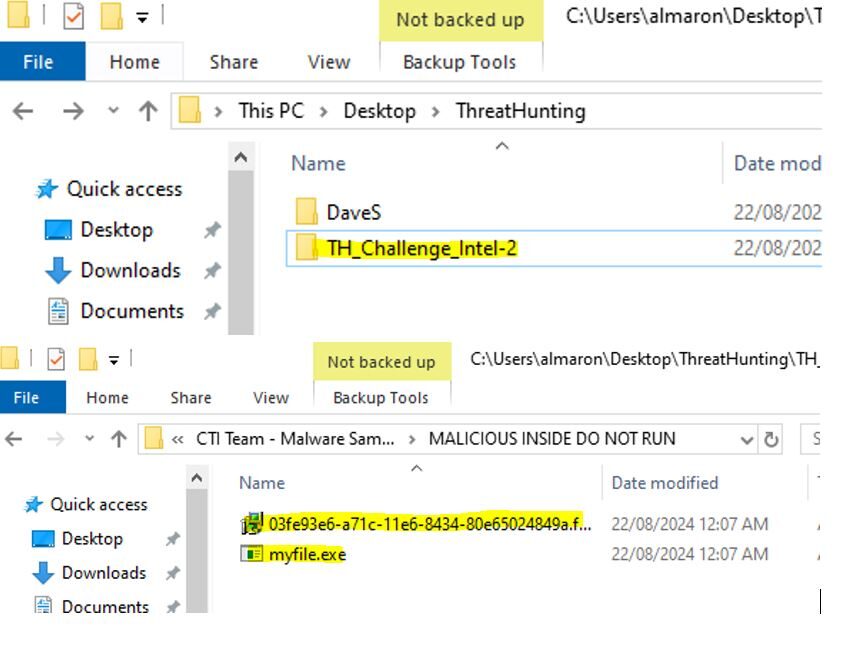
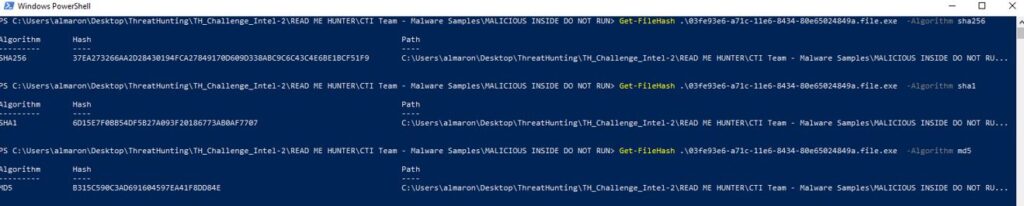
3. There are several ways to obtain the required hash values. For simplicity, we will use PowerShell.
Get-FileHash -Path "myfile.exe" -Algorithm SHA256
Get-FileHash: The PowerShell cmdlet used to compute the hash value of a file.-Path "myfile.exe": Specifies the path to the file for which you want to calculate the hash. Make sure to use the correct path to your file.-Algorithm SHA256: Specifies the hashing algorithm to use. In this case, SHA256. You can replaceSHA256with other supported algorithms likeMD5,SHA1, etc.
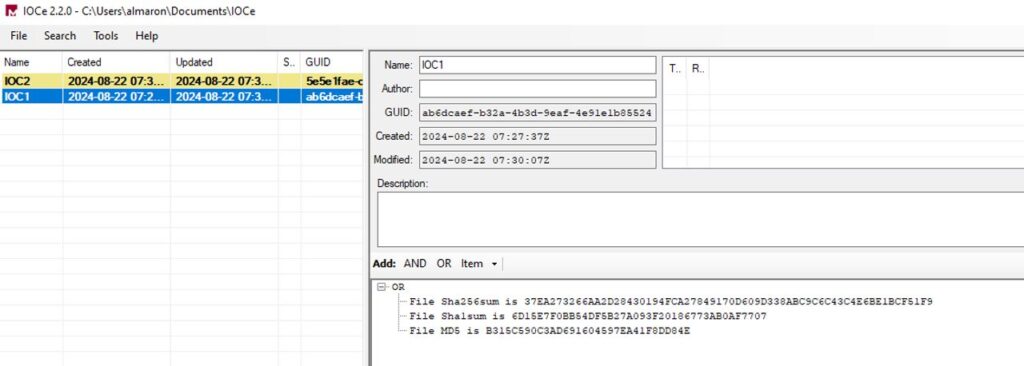
IOC 1 (Click on the image below to zoom in)
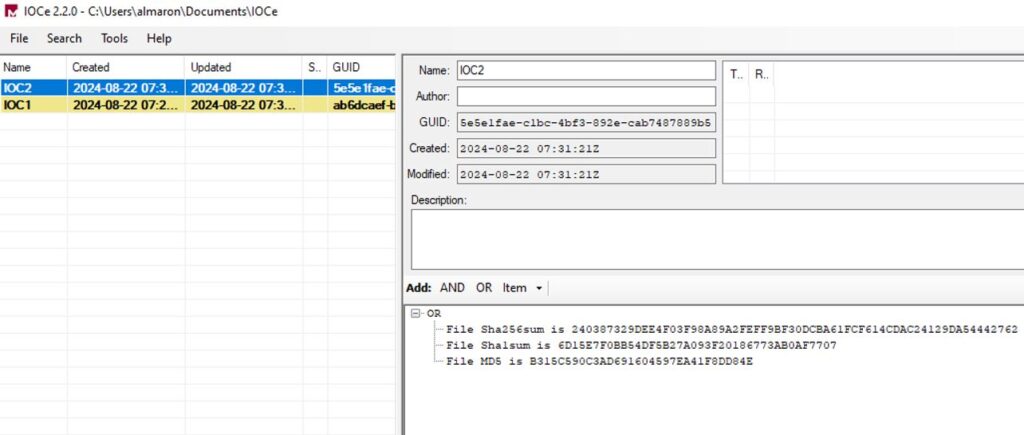
IOC 2 (Click on the image below to zoom in)
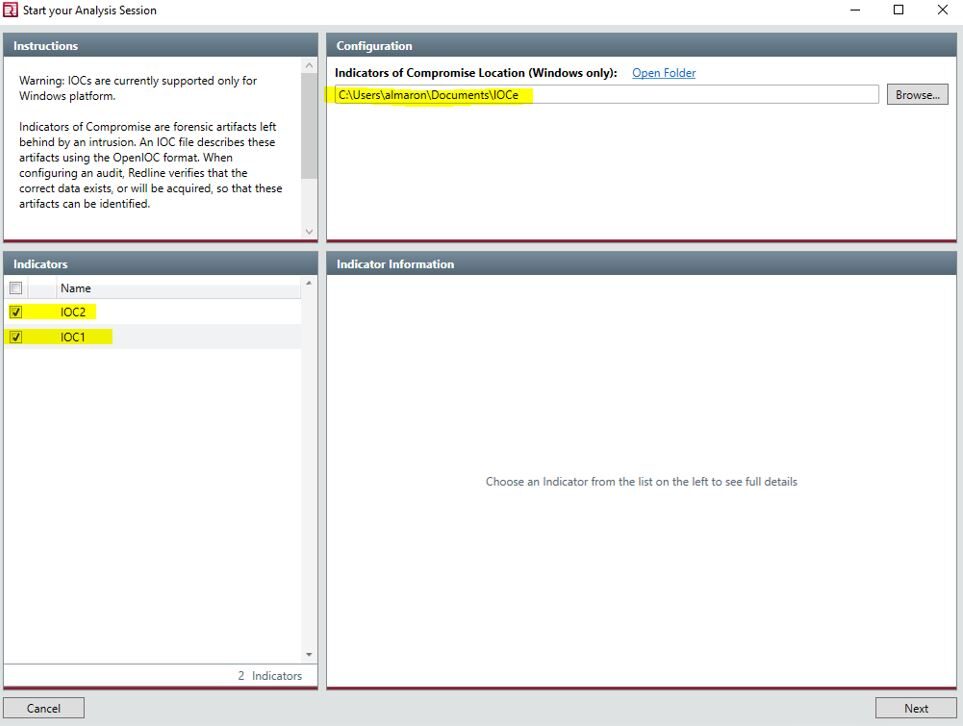
4. From the obtained hashes, open the IOC Editor and create indicators for IOC 1 and IOC 2.
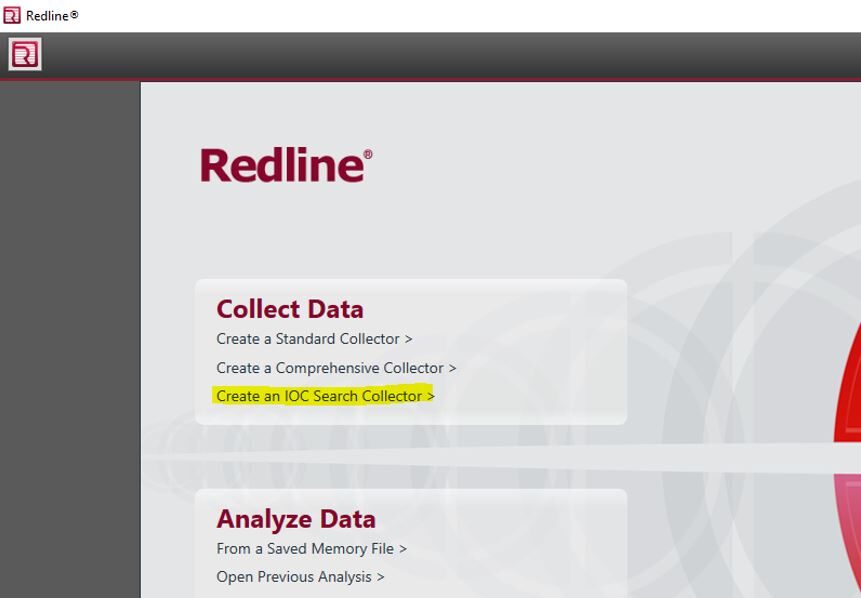
5. Open Mandiant RedLine & click “Create an IOC Search Collector”
6. Browse to the folder where the IOCs are saved, select both IOCs, and then click "Next."
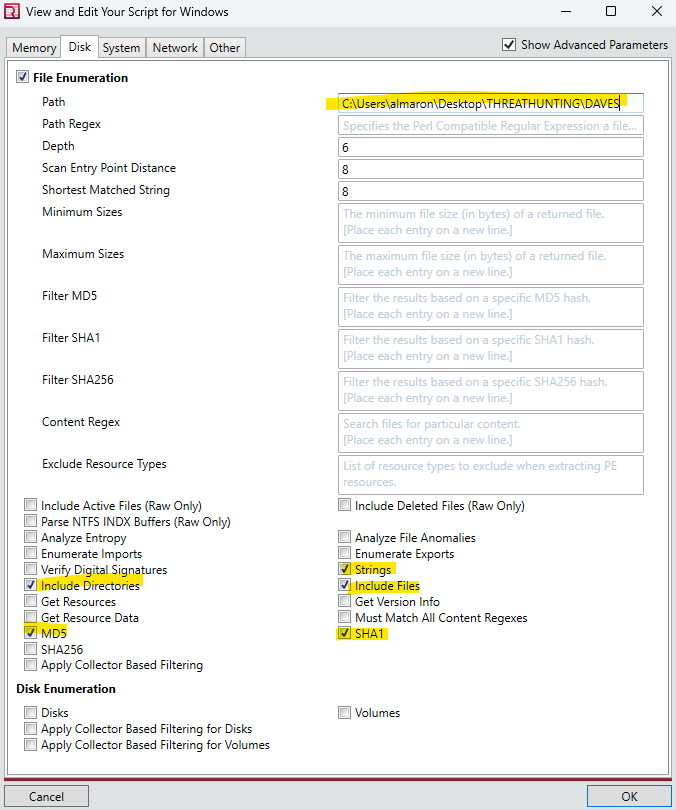
7. Click on "Edit your script". Check File Enumeration and enable the options highlighted below. Specify the Path or location on your system where you want Redline to search for potential compromises.
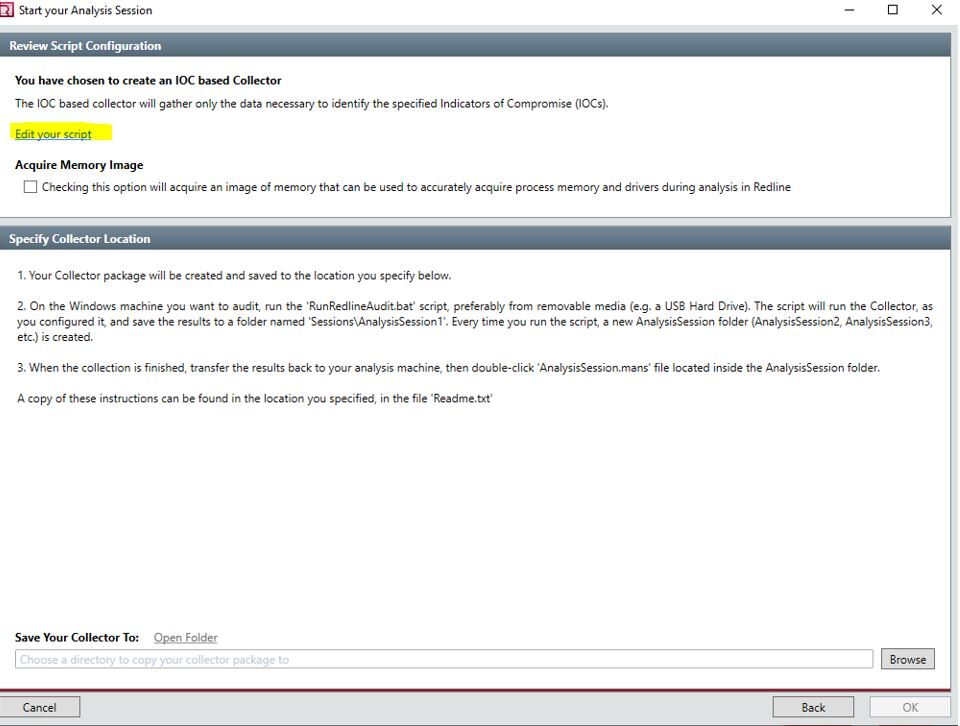
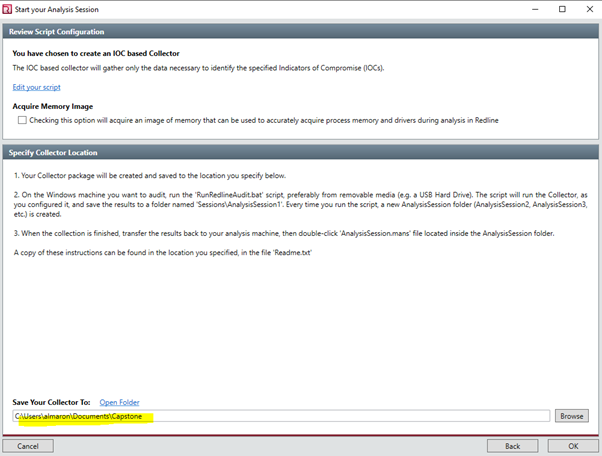
8. Your Collector package is created and saved to the location you specified.
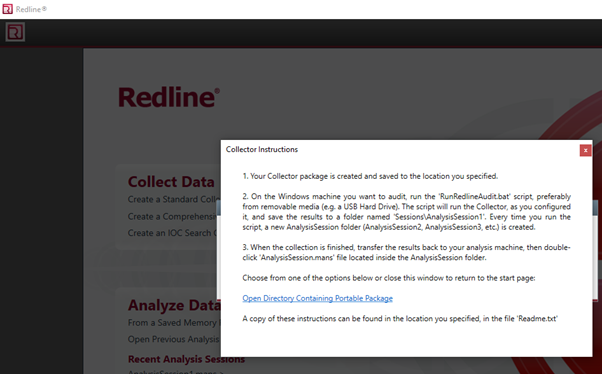
9. Open CMD and navigate to the directory where you saved the collector files. Run the batch file .\RunRdlineAudit.bat
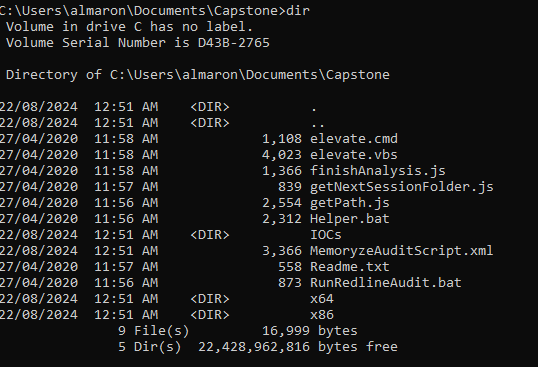

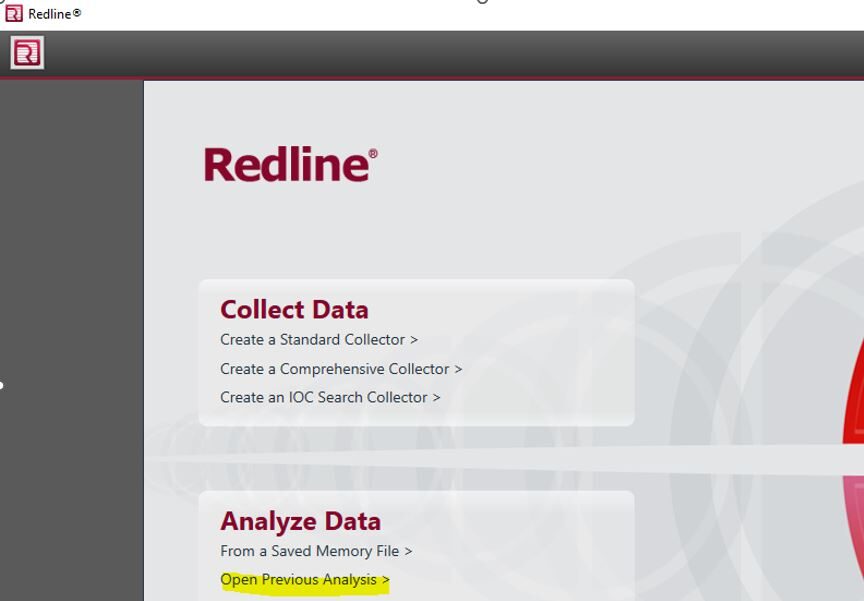
10. Once the batch file has finished running, you will be returned to the command prompt (as seen above). Reopen Redline, select Open Previous Analysis, choose the AnalysisSession1.mans file, and then review the results.
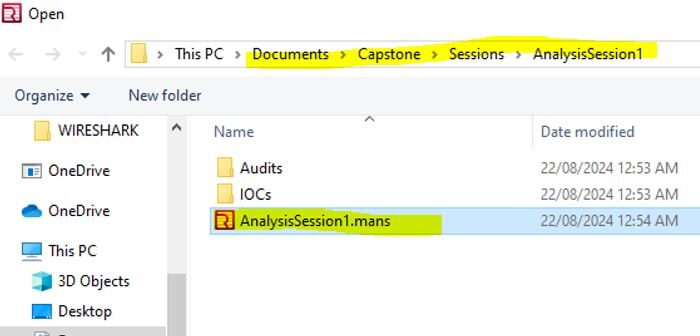
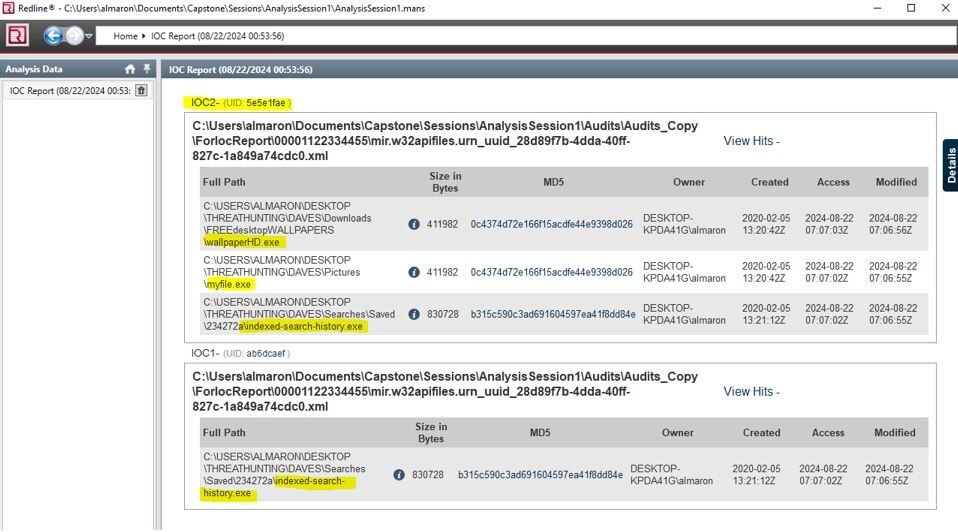
11. Finally, review the report, which will detail all identified threats based on your IOC file. It includes file paths, sizes, MD5 hashes, user information, and relevant file dates.
The complete Redline user guide can be downloaded for free from the link below: