Network Analysis

Wireshark is an open-source network packet analyzer that allows you to see all the network traffic being transmitted (sent/received) over a network. This tool is used to identify network problems, troubleshoot slow network issues, and analyze the data being transmitted over the network.
The course includes two practical labs on analyzing PCAP files (packet captures). You’ll apply the basics of Wireshark, use filters and statistics, and analyze network traffic to understand how attackers might gain access to the network.
Part 1: Wireshark User Interface
Part 2 : PCAP 1 Challenge
Part 3: PCAP 2 Challenge
Part 4: Additional Wireshark Filters
Part 5: Recommended Free Wireshark Resources!
Part 1: Wireshark User Interface
Before we dive into the course review, let’s first explore Wireshark user interface.
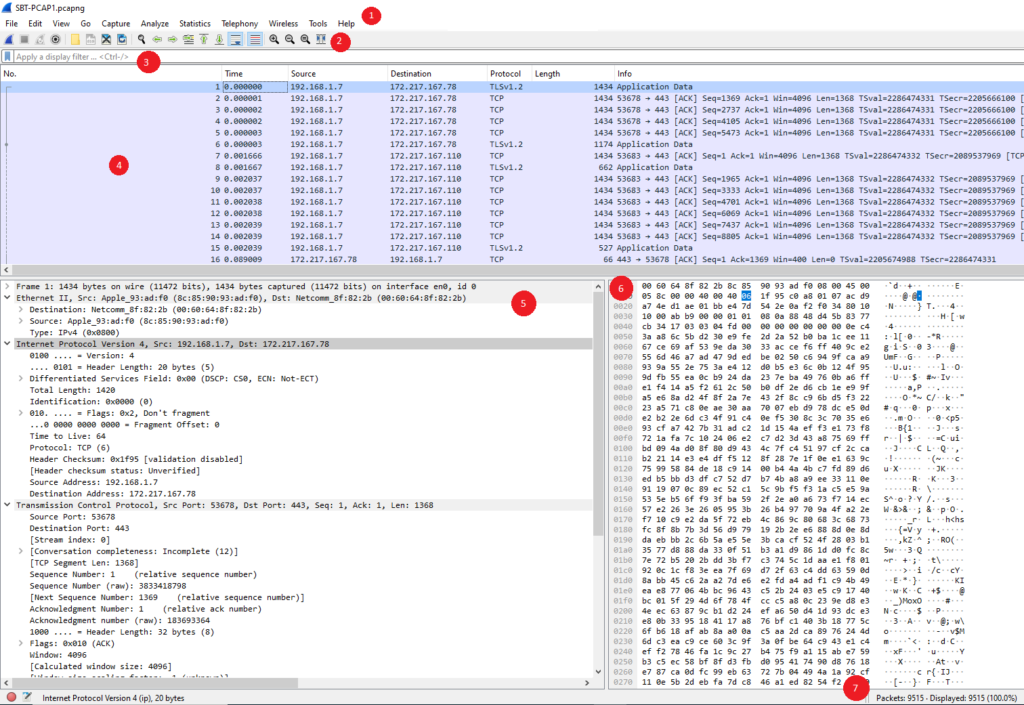
1. Main menu – It’s divided into several sections, each containing a set of related options common below.
- File Menu – contains items to open , save, print, or export capture files .
- View Menu – display of the captured data, including colorization of packets, zooming the font, showing a packet in a separate window, expanding and collapsing trees in packet details
- Go Menu – items to go to a specific packet
- Capture – allows you to start and stop captures and to edit capture filters.
- Statistics – contains items to display various statistic windows, including a summary of the packets that have been captured, display protocol hierarchy statistics and much more.
2. Main toolbar – allows easy access to frequently used menu. Common functions such as to start , stop , save as or open capture file (pcap).
3. Filter toolbar – lets you quickly edit and apply display filters to quickly and easily focus on specific packets within a large capture.
4. Packet list pane – Each line in the packet list corresponds to one packet in the capture file. If you select a line in this pane, more details will be displayed in the “Packet Details” and “Packet Bytes” panes.
5. Packet details pane – displays detailed information about a selected packet.
6. Packet bytes pane – displays the raw data of a selected packet in a hexadecimal format
7. Status bar – displays various types of information such as number of packets captured
References : Wireshark.org
Part 2 : PCAP 1 Challenge
🔑Key to answering these questions is using the correct filter. Being familiar with filters is essential for locating or tracing the needed information.
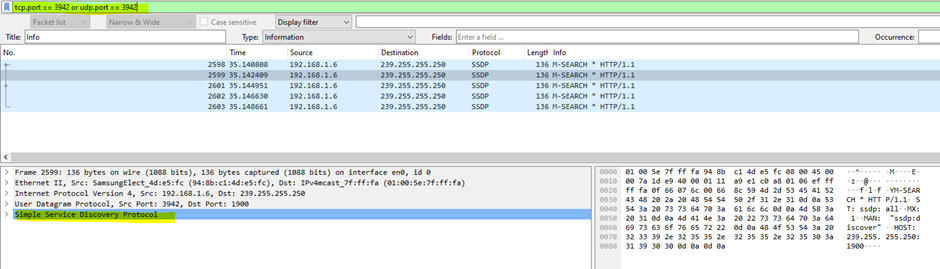
1.Which protocol was used over port 3942?
Ports are numerical identifiers used in network communications. Each port is associated with a specific service or application running on a device. To determine which protocol was used over port 3942 using Wireshark, you can use a display filter. At the packet details pane we can see details of the protocol.
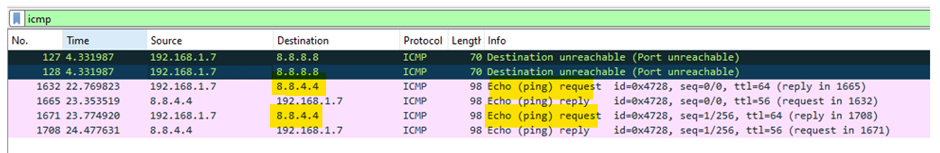
2.What is the IP address of the host that was pinged twice?
The Internet Control Message Protocol (ICMP) sends error messages and network information between devices in an IP network. One type of ICMP is the Echo request/reply (ping), which tests if a network host is reachable and measures roundtrip time.
To view only ICMP traffic, type “ICMP” in the display filter box and press Enter. This will show only ICMP packets.
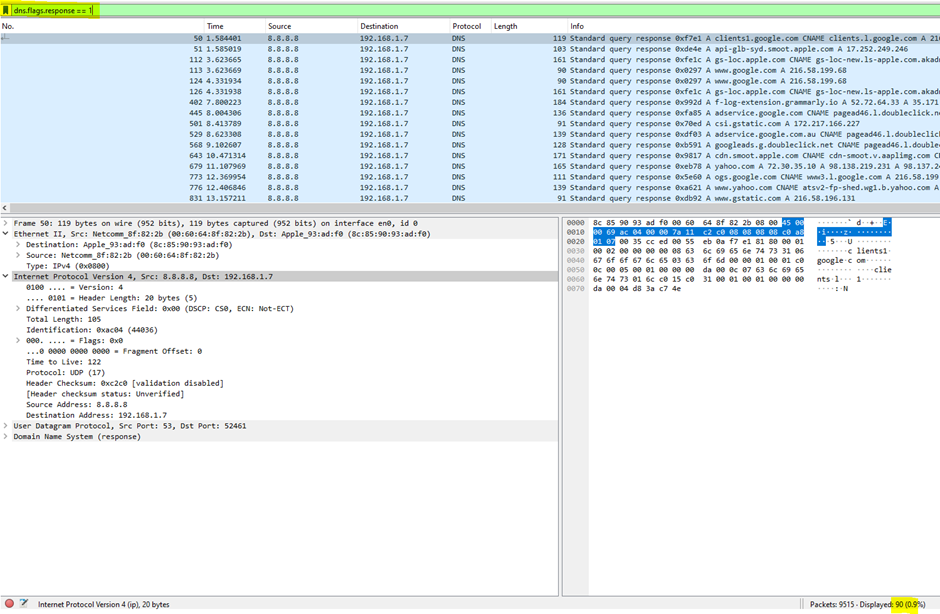
3. How many DNS query response packets were captured?
This refers to the Domain Name System protocol. We can see the total at the status bar.
DNS Query: When a client sends a DNS query to resolve a domain name, the response flag is 0.
DNS Response: When the DNS server replies to the query with the requested information (or an error), the response flag is set to 1.
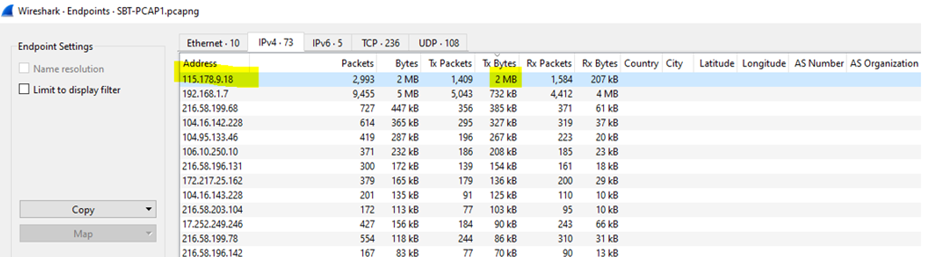
4.What is the IP address of the host which sent the most number of bytes?
Endpoint statistics can be used to identify the most active hosts on the network. To do this, go to the “Statistics” then select “Endpoints”. This will display a summary of the most active hosts, including their IP addresses, packet count, and byte count.
Part 3: PCAP 2 Challenge
🔓This activity is more interesting as we trace, analyze, and assemble packets to capture passwords sent over the wire. Protocols like HTTP and FTP are insecure because they transmit data and authentication credentials in plain text without encryption.
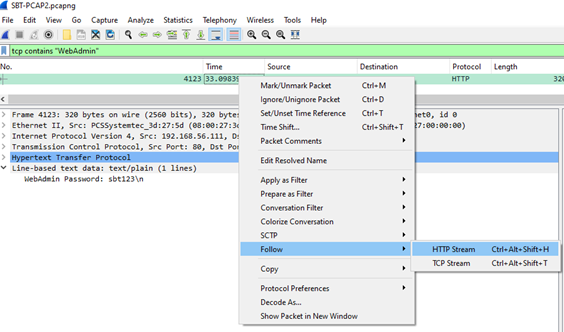
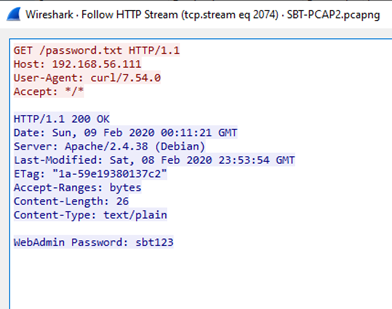
1.What is the WebAdmin password?
It’s a filter that displays all TCP packets that contain a certain term , in this example we are looking for WebAdmin.
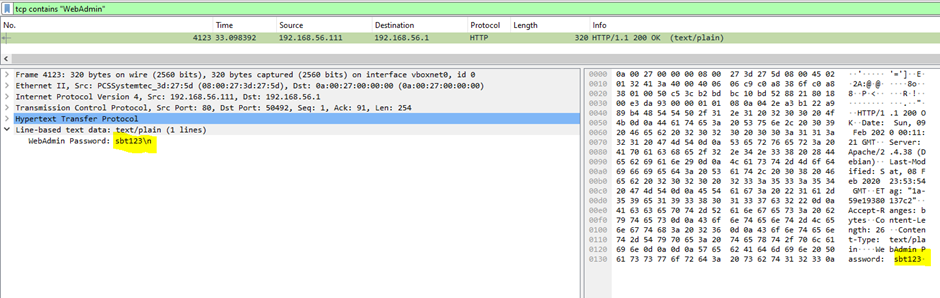
The “Follow HTTP / TCP Stream” feature lets you view and analyze the entire conversation between two endpoints over a TCP connection in a clear, readable format.
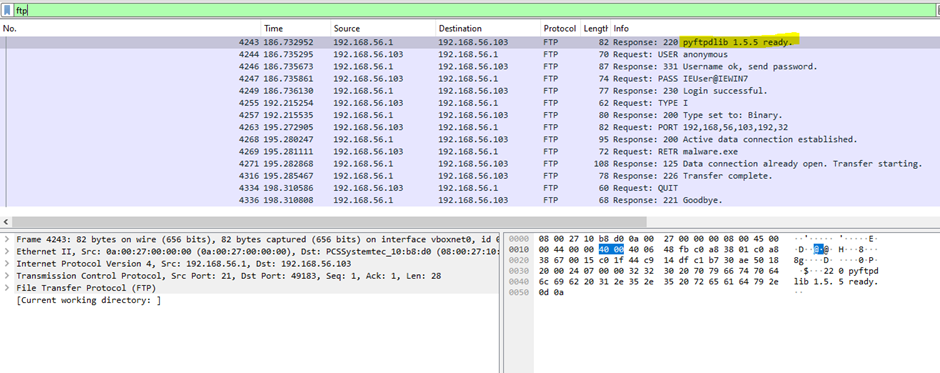
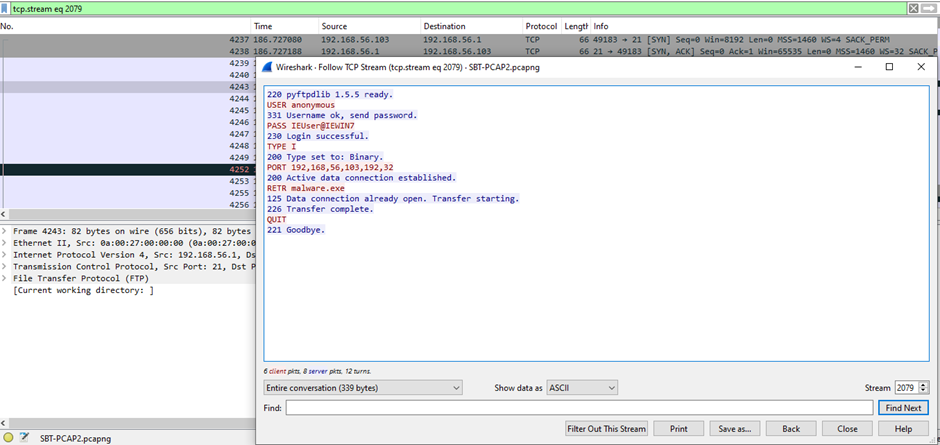
2.What is the version number of the attacker’s FTP server?
Search for “ftp” on the filter toolbar to view the FTP conversation.To make it more readable, use the “Follow TCP Stream” feature.
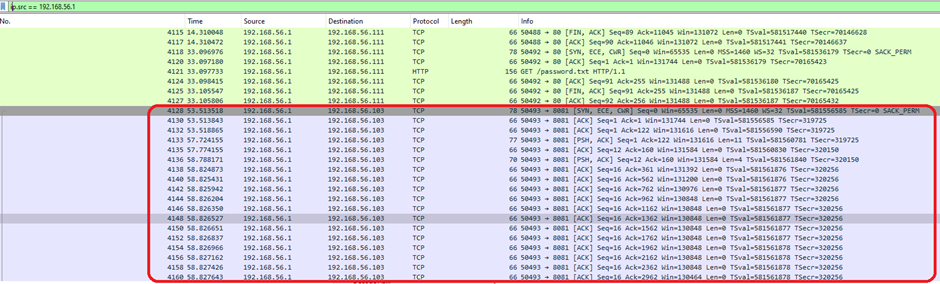
3.Which port was used to gain access to the victim Windows host?
A series of ACK (acknowledgment) packets confirm a connection established at port 8081, then it indicates that port 8081 was used for the connection to the victim Windows host.
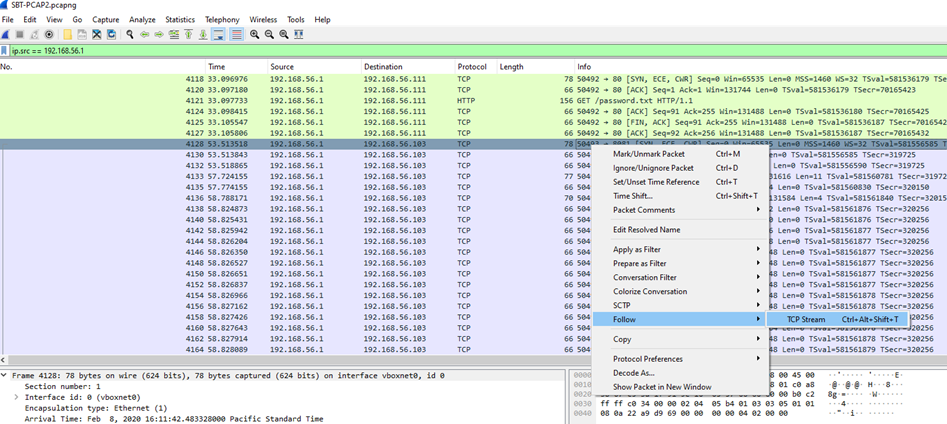
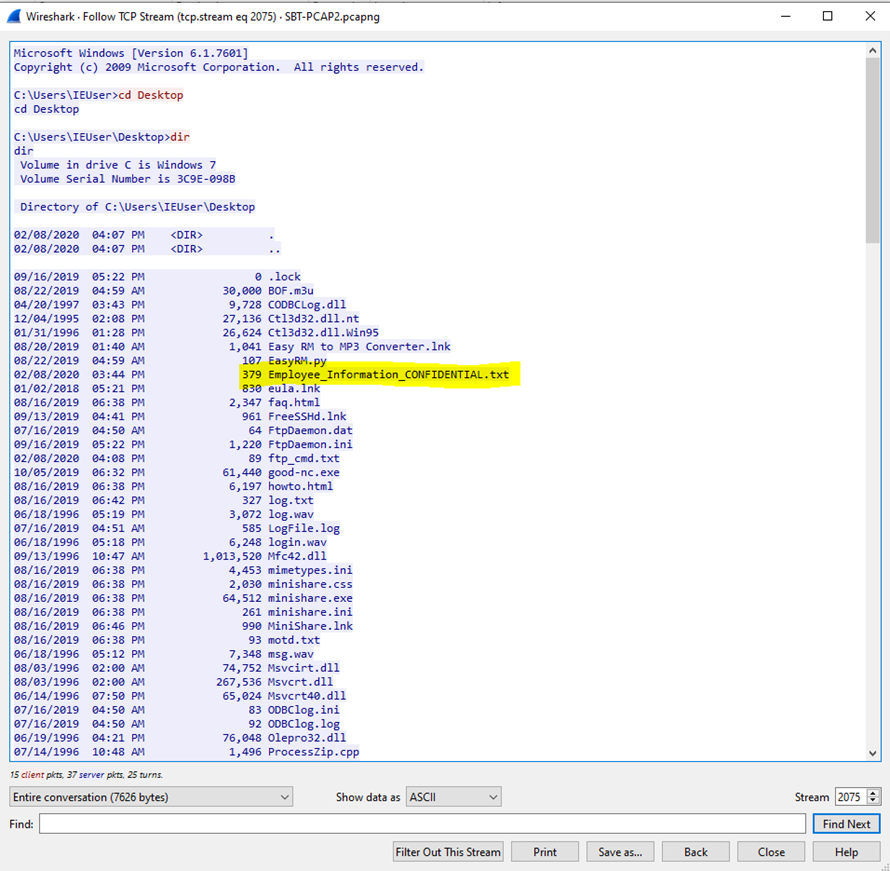
4.What is the name of a confidential file on the Windows host?
To find a confidential file’s name on a Windows host, analyze the traffic or logs. The TCP stream will show the file with “confidential” in its name.
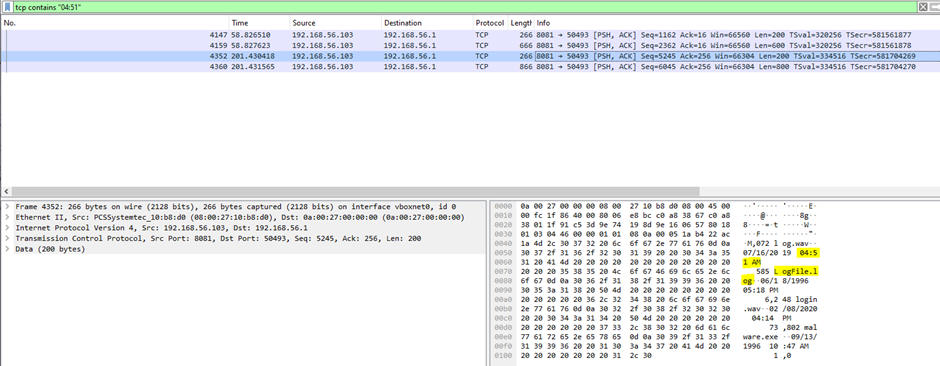
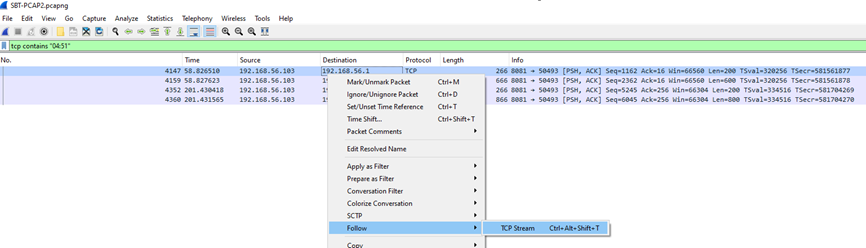
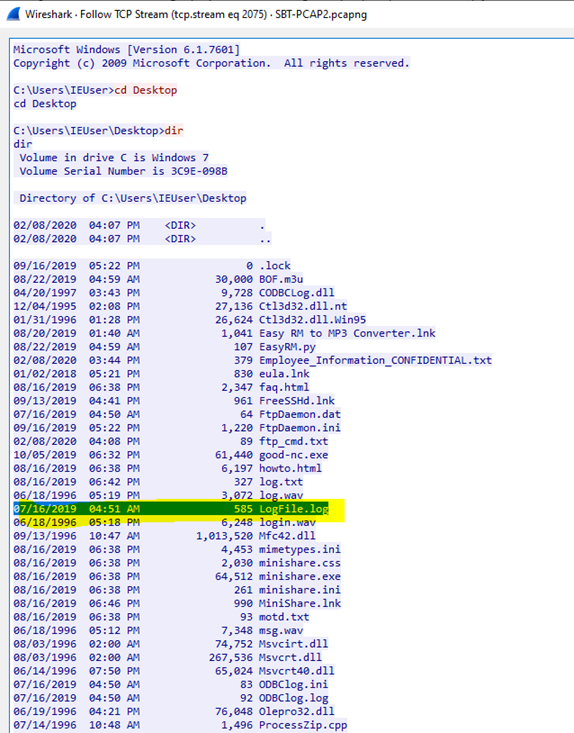
5. What is the name of the log file that was created at 4:51 AM on the Windows host?
Search for tcp contains “04:51” on filter toolbar then to analyze further, use the “Follow TCP Stream” feature.
Part 4: Additional Wireshark Filters
1. ip.addr == x.x.x.x
Filters packets to show only those where the IP address is either the source or destination address.
2. ip.src == x.x.x.x
Filters packets to show only those where the source IP address is x.x.x.x.
3. ip.dst == x.x.x.x
Filters packets to show only those where the destination IP address is x.x.x.x.
4. ip.src == xxxx && ip.dst == xxxx
Filters packets where the source IP address is xxxx and the destination IP address is xxxx.
5. tcp.port == xxx
Filters packets to show only those where the TCP port number is xxx, either source or destination.
6. tcp.flags.reset == 1
Filters packets to show only those where the TCP RST (reset) flag is set to 1.
This indicates that the connection was reset.
7. tcp contains xxx
Filters packets to show only those where the TCP payload contains the specified string
or pattern xxx.
8. !(arp or icmp or dns)
Filters packets to exclude ARP, ICMP, and DNS protocols.
9. udp contains xx:xx:xx
Filters packets to show only those where the UDP payload contains the specified byte
sequence xx:xx:xx.
10. dns.flags.rcode != 0
Filters DNS packets where the response code is not equal to 0. In DNS, a response code of 0
indicates no error (success).
Part 5: Recommended Free Wireshark Resources!
David Bombal : Wireshark Ethical Hacking course
Chris Greer : Wireshark Masterclass
Conclusion:
As I continue to explore and learn how to use Wireshark, I’m discovering several effective methods for finding and analyzing the information needed. Wireshark, as a powerful network protocol analyzer, offers a range of features that can be leveraged to understand network traffic in depth.
May we all embrace continuous learning and remain passionate about growth. Happy exploring, God bless everyone!