Microsoft Defender For Endpoint Part 1

Installing Windows Defender and Examining Vulnerabilities
Overview : Defender for Endpoint, Microsoft’s enterprise security platform, integrates endpoint behavioral sensors within Windows, cloud security analytics, and threat intelligence to detect and respond to advanced threats by translating behavioral signals into actionable insights and alerts.
1.Sign up for a trial from the link provided:
https://signup.microsoft.com/create-account/signup?products=7f379fee-c4f9-4278-b0a1-e4c8c2fcdf7e&ru=https://aka.ms/MDEp2OpenTrial?ocid=docs-wdatp-enablesiem-abovefoldlink
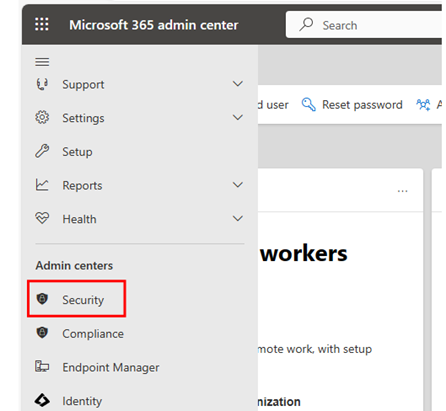
2. Click on “Security” from the Microsoft Admin Center.
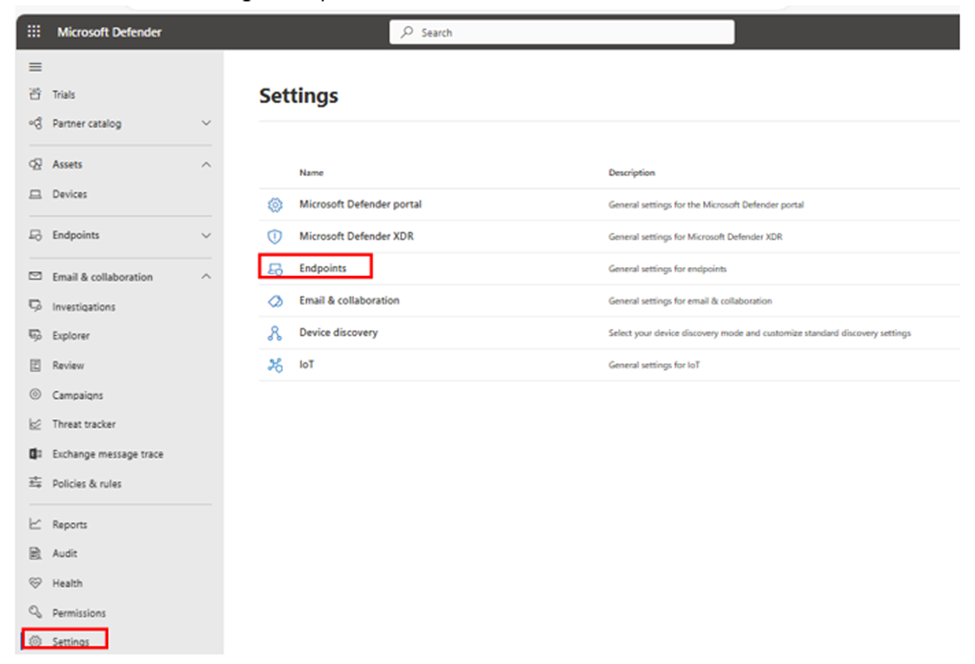
3. Add devices by navigating to Settings -> Endpoints.
4. Under Device Management -> Onboarding, select the deployment method; for simplicity, download the onboarding package.
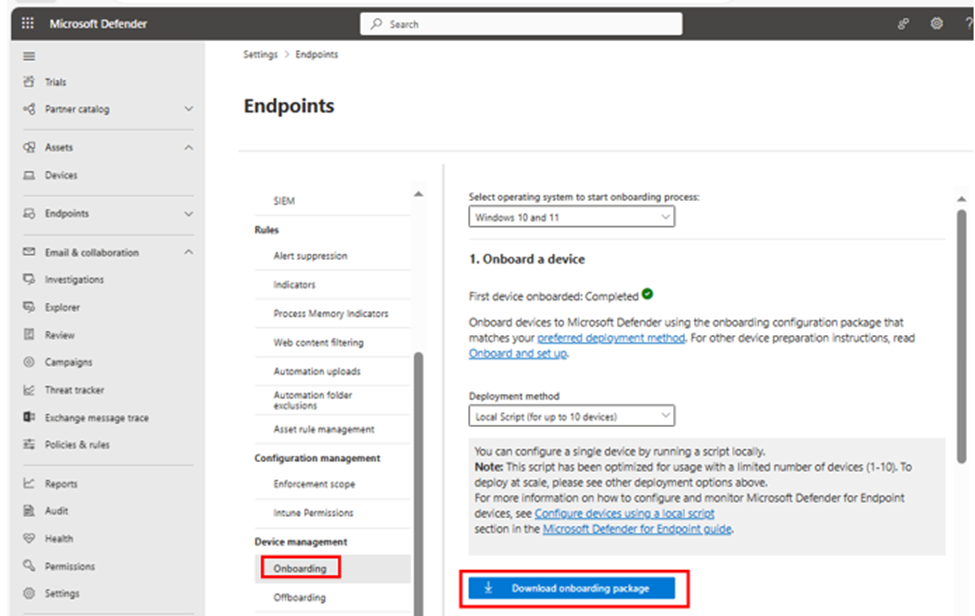
5. Execute the script on the target machine..
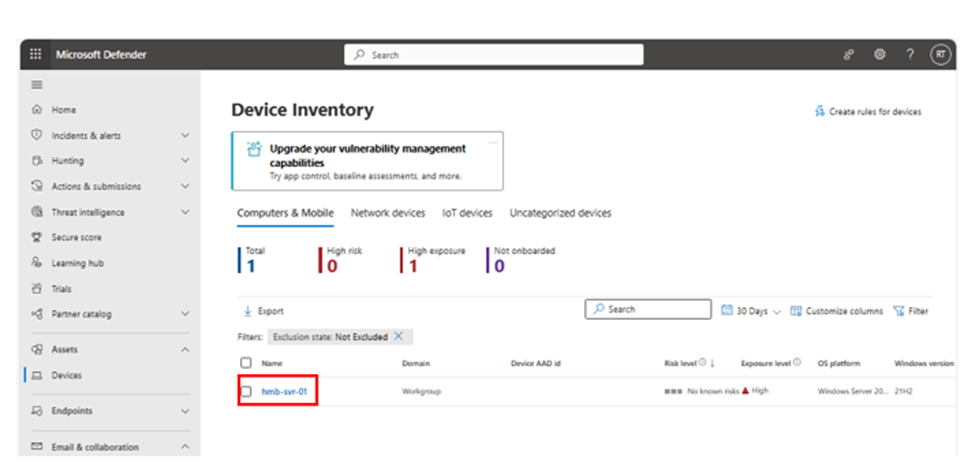
6. Once installed on the target machine, locate it under Devices; click on the device name to discover vulnerabilities.
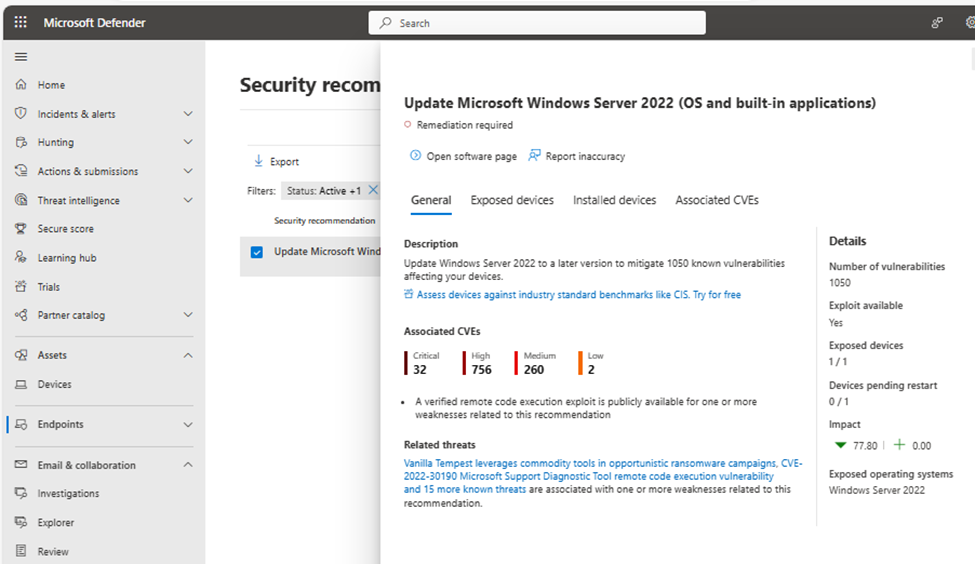
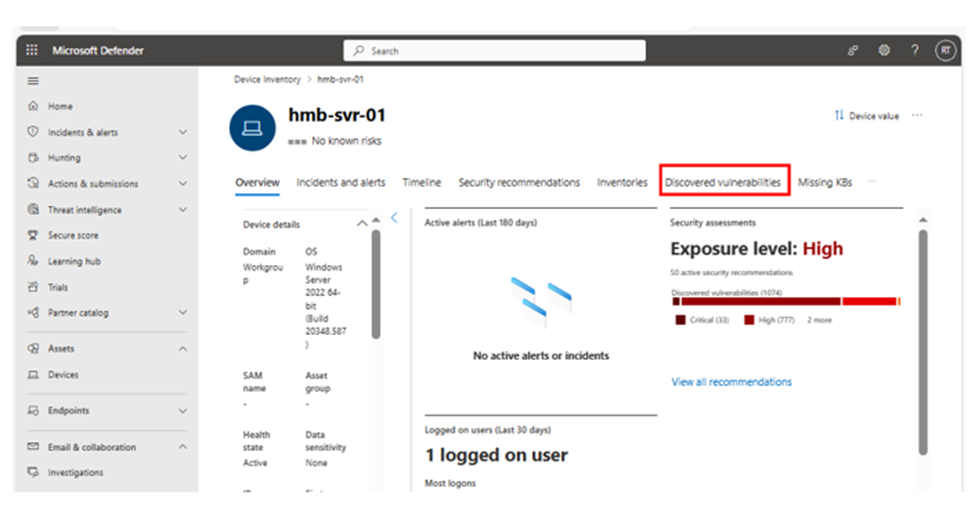
7. Click on “Discovered Vulnerabilities.”
8. Select the vulnerability you want to investigate.
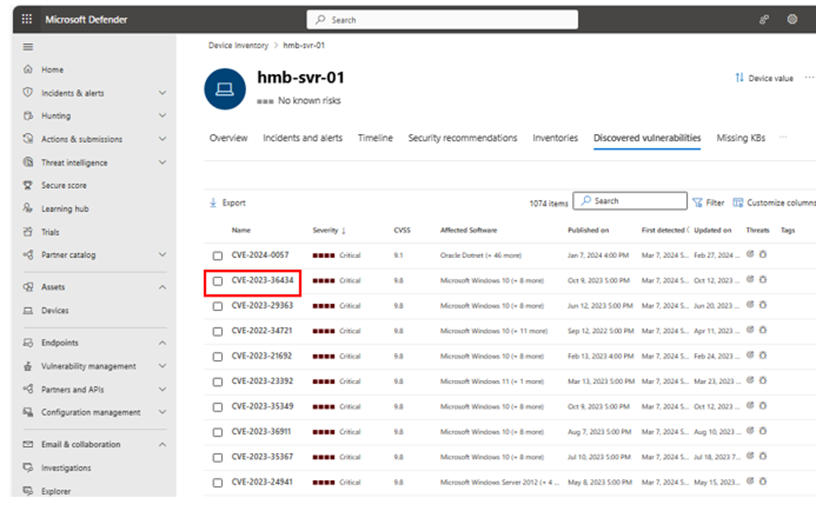
9. A flyout panel containing the CVE details will appear; click “Go to related security recommendation.”
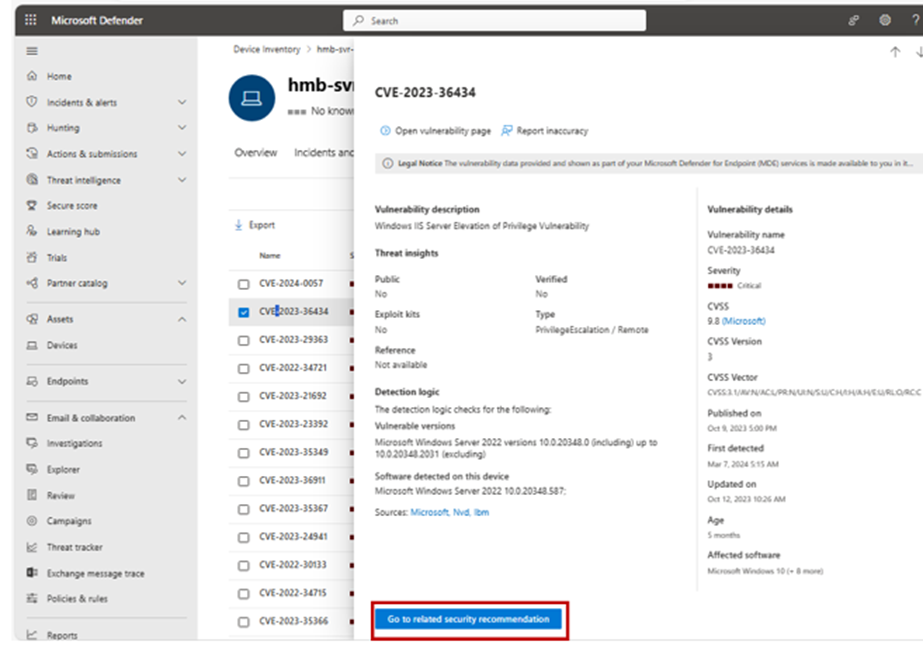
10.Check & perform recommended action.