Vulnerability Management Labs Review

Contents:
Lab 1 : Setting up Metasploitable 2 & Scanning Using Nmap
Lab 2 : Vulnerability Scanning Using Nessus
Lab 3: WPScan Vulnerability Scanner
Lab 1 : Setting up Metasploitable 2 & Scanning Using Nmap
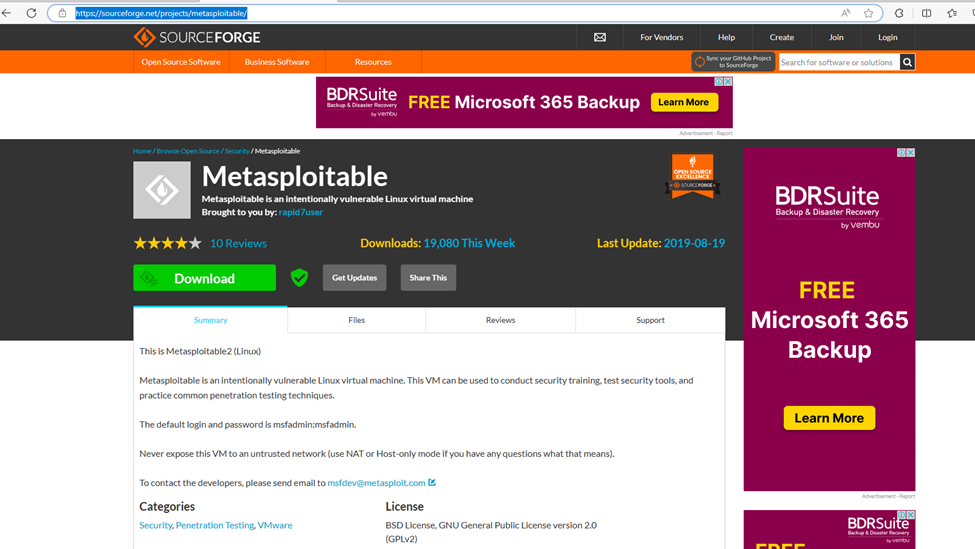
1. Download Metasploitable 2 Metasploitable download | SourceForge.net
Metasploitable 2 is an intentionally vulnerable virtual machine created by security company Rapid7. It is designed to be a test environment and playground for ethical hackers.
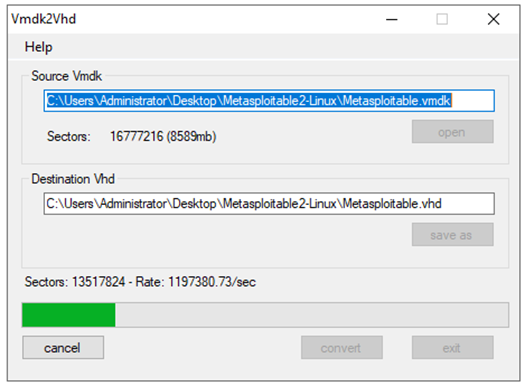
2. Download Vmdk2Vhd – I had some issues running the vm on Microsoft Hyper V so I used this to convert vmdk to Vhd
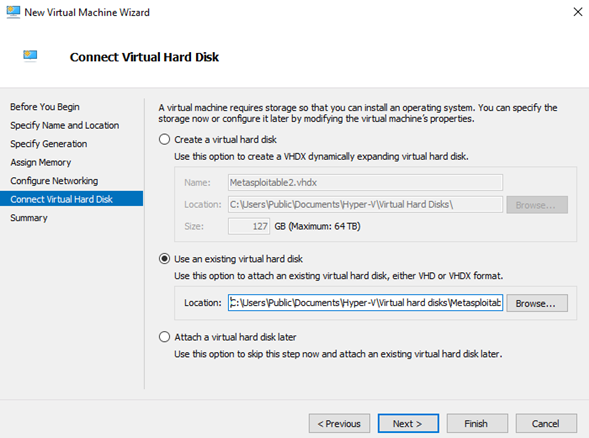
3. Create VM & connect VHD that we have recently converted
1.

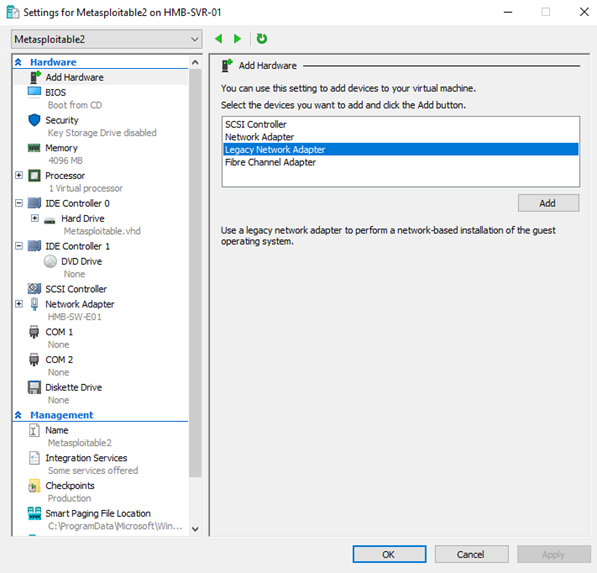
3. Add hardware – Legacy Network Adapter so it can be seen on the network.
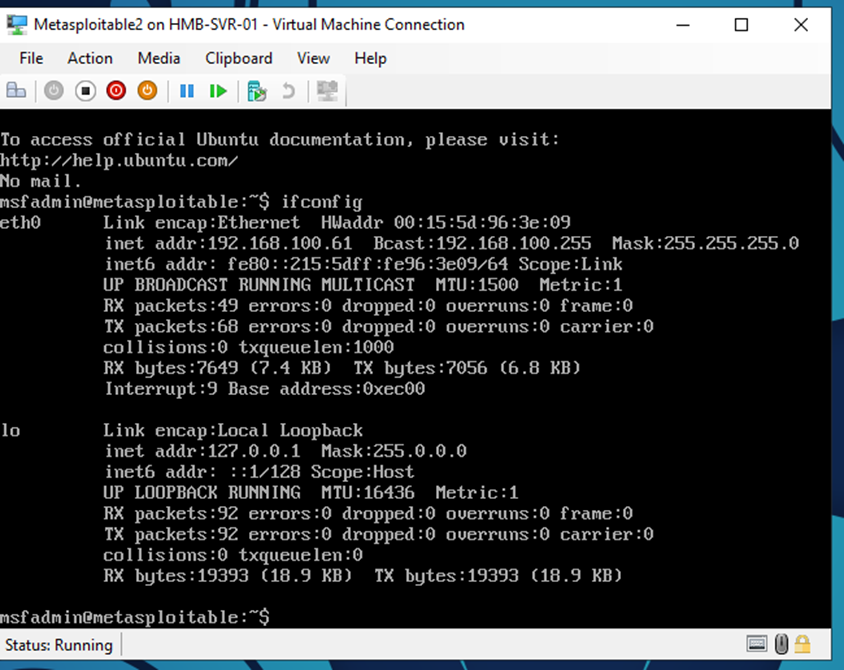
5. Run to the instruction on how to use Nmap to scan VM Metasploitable 2
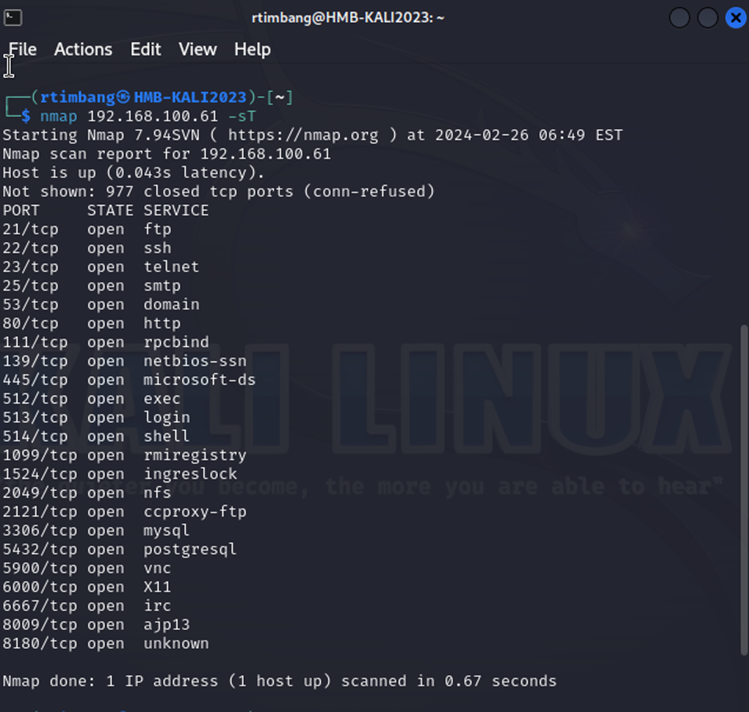
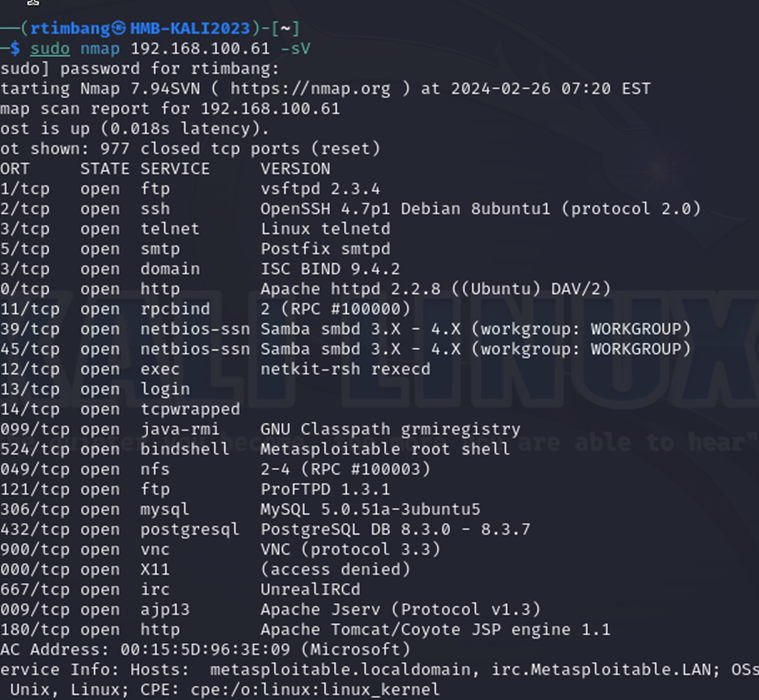
5.1 How many TCP ports are OPEN on MS2? (Use the -sT flag in Nmap).
5.2 How many UDP ports are OPEN on MS2? (Use the -sU flag in Nmap – this may take a while).
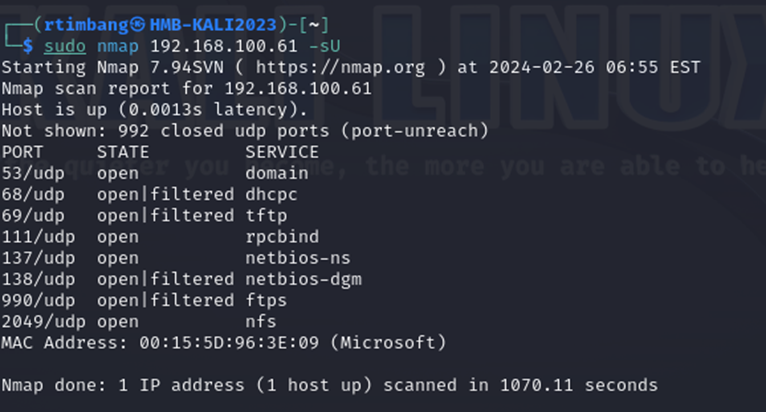
5.3 What port is running a Metasploitable Root Shell? (Use the -sV flag in Nmap).
Lab 2 : Vulnerability Scanning Using Nessus
1.Downlaod https://www.tenable.com/products/nessus/nessus-essentials and register for an activation code.
2. Proceed with install , I installed on Microsoft Server 2022 for simplicity.
3. Once completed access the Nessus at local port 8834 then register.
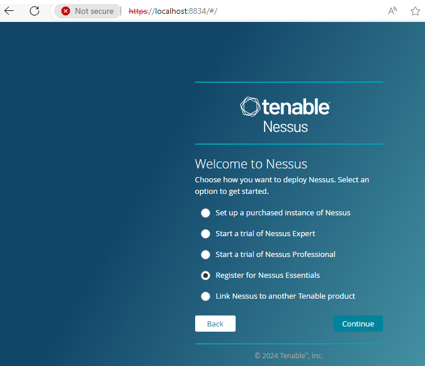
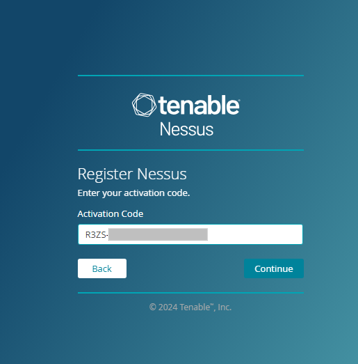
4. Activate with the provided code received in your email.
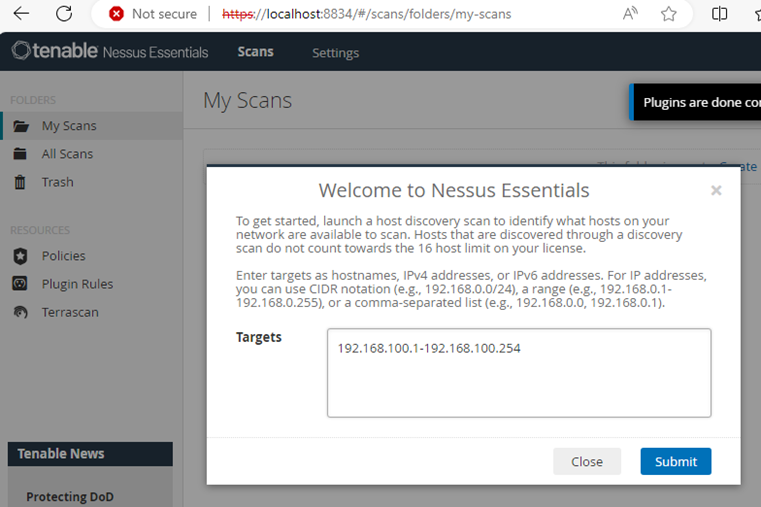
5. Once initialize, input the network to scan
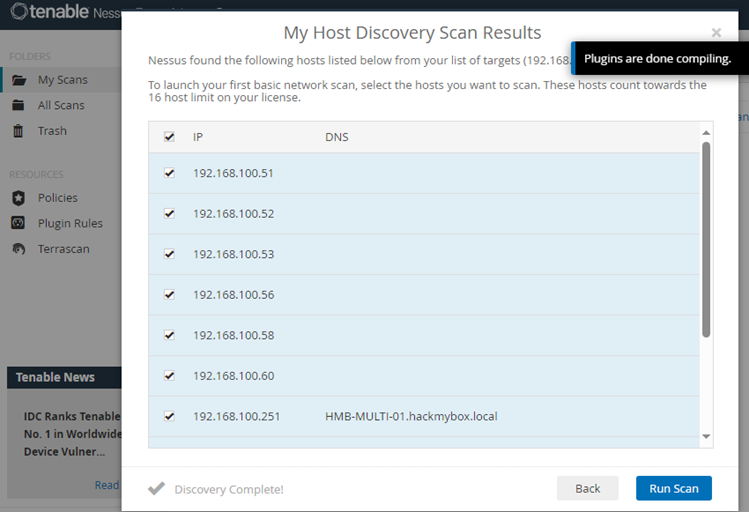
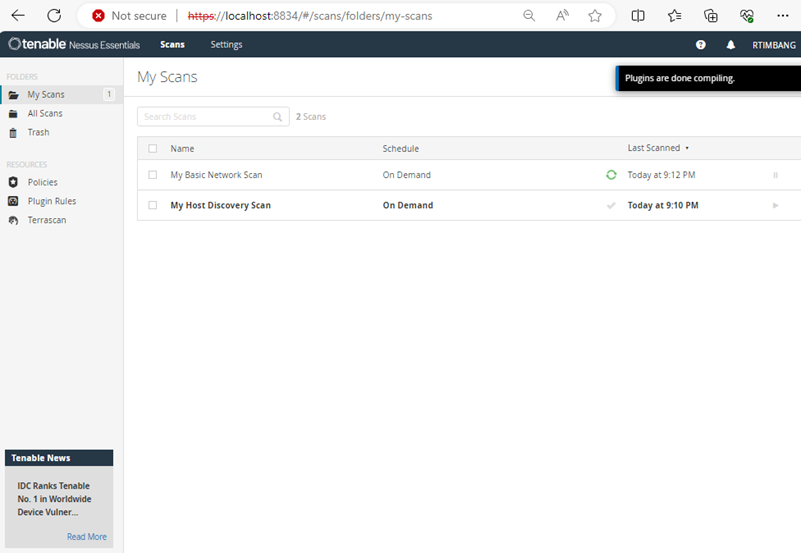
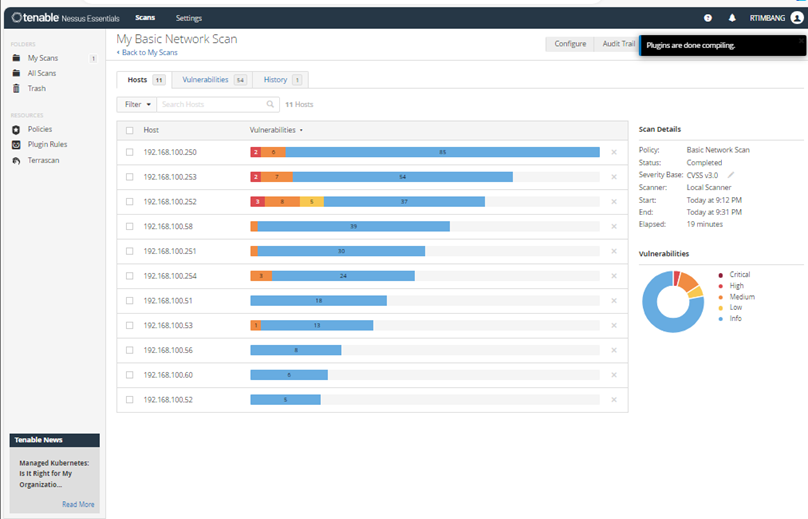
6. View scan results
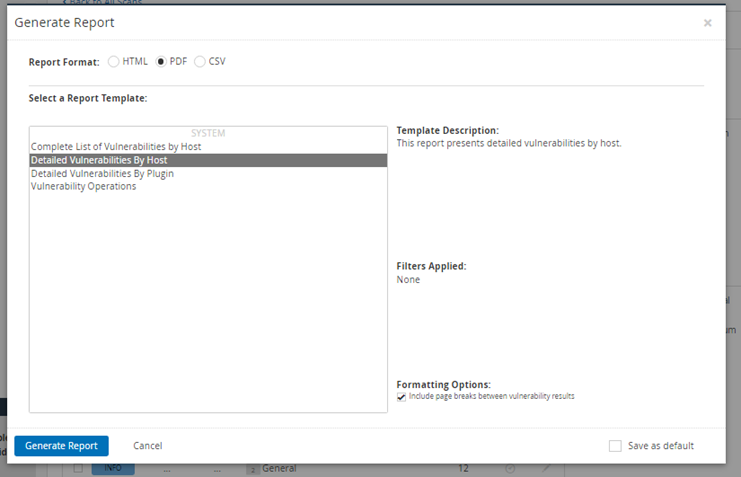
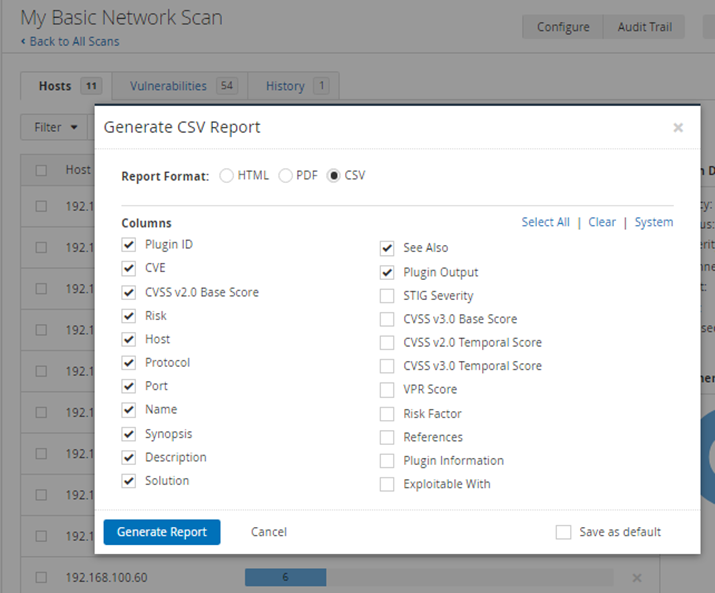
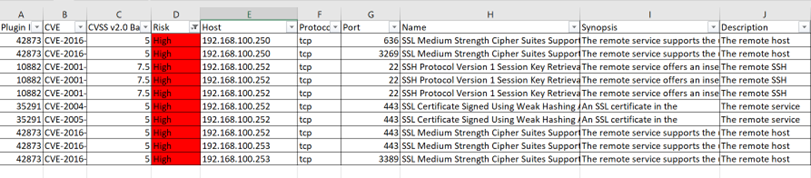
9. From the downloaded CSV, sort data by Risk (sample below with High Risk)
10. Additional features included on Nessus Essentials . Enjoy!

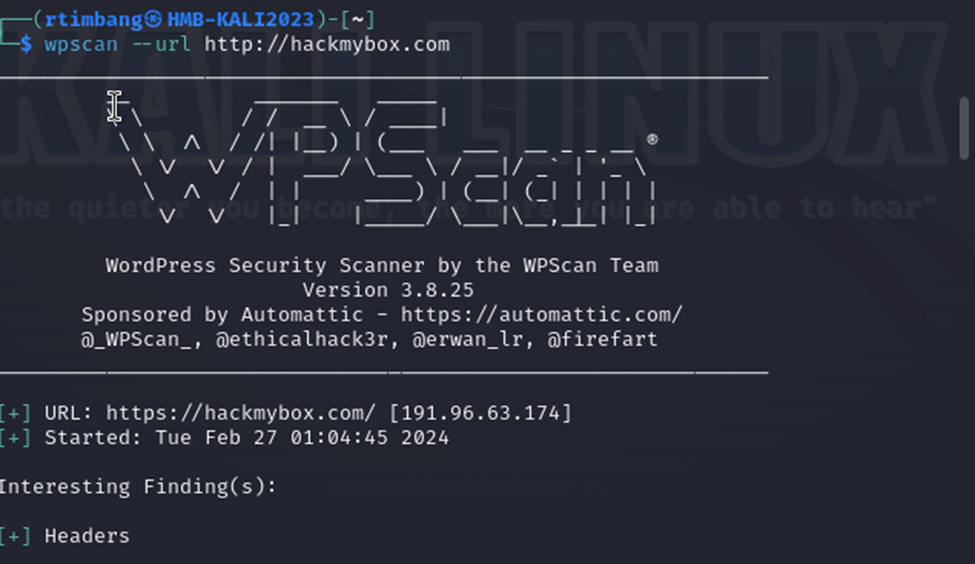
Lab 3: WPScan Vulnerability Scanner
1.WPScan is already installed on Kali Linux. Below is a sample of running a scan on my blog. Some add-ins need to be updated for the results.