Footprinting – SMTP / IMAP / POP3

(Insights from HTB Academy)
SMTP (Simple Mail Transfer Protocol) remains a key protocol for sending emails and continues to be widely used across the internet today. Despite advancements in email systems, security measures, and communication technologies, SMTP is still the backbone of email transmission.
SMTP, IMAP, and POP3 are key protocols in the email ecosystem, each serving a distinct role. SMTP is responsible for sending emails from the client to the server or between servers. IMAP and POP3, on the other hand, are used for retrieving emails.
As email threats evolve, it is crucial to understand the vulnerabilities of SMTP and related protocols like IMAP and POP3. Whether you're a cybersecurity professional, an email system administrator, or someone passionate about email technologies, grasping how SMTP works is essential.
For a simplified explanation of these protocols, check out the reading link below for an easy-to-understand overview.
https://mailtrap.io/blog/smtp/
I recently worked on an exercise from HTB (HackTheBox) where I explored footprinting SMTP servers. Here's a quick overview:
Ports :
SMTP: 25 (unencrypted), 587 (STARTTLS), 465 (SMTPS)
IMAP: 143 (unencrypted), 993 (SSL/TLS)
POP3: 110 (unencrypted), 995 (SSL/TLS)
In this lab, we are tasked with enumerating the SMTP service, capturing the banner, and identifying valid usernames on the system.
Task 1: Find the username that exists on the system
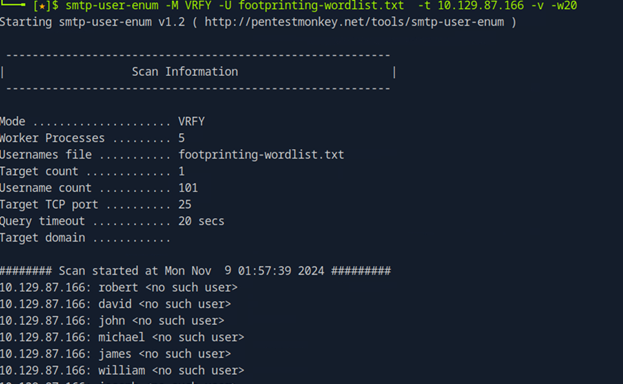
smtp-user-enum -M VRFY -U footprinting-wordlist.txt -t 10.129.87.166 -v -w20
- -M VRFY: Tells smtp-user-enum to use the VRFY command, which checks if a given email address or username exists on the server.
- -U footprinting-wordlist.txt: Specifies the wordlist file (footprinting-wordlist.txt), which contains potential usernames to check against the SMTP server.
- -t 10.129.87.166: Points to the target SMTP server (in this case, 10.129.87.166).
- -v: Enables verbose output, which shows detailed progress of the command.
- -w 20: Specifies the number of worker threads (20 in this case), which speeds up the enumeration process by running multiple checks simultaneously.
Task 2: Enumerate the SMTP service and submit the banner
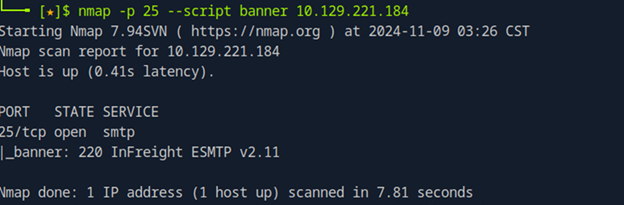
nmap -p 25 --script banner 10.129.221.184
- -p 25: This flag specifies that Nmap should scan port 25, which is the default port for SMTP (Simple Mail Transfer Protocol).
- --script banner: The banner script tells Nmap to attempt to retrieve a service banner from the target system. A banner typically includes information such as the version of the service running on the specified port (in this case, SMTP).
- 10.129.221.184: This is the target IP address you’re scanning. Replace it with the appropriate IP address of the system you are testing.
IMAP / POP3
Task 3: Try to enumerate & access the emails on the IMAP server.
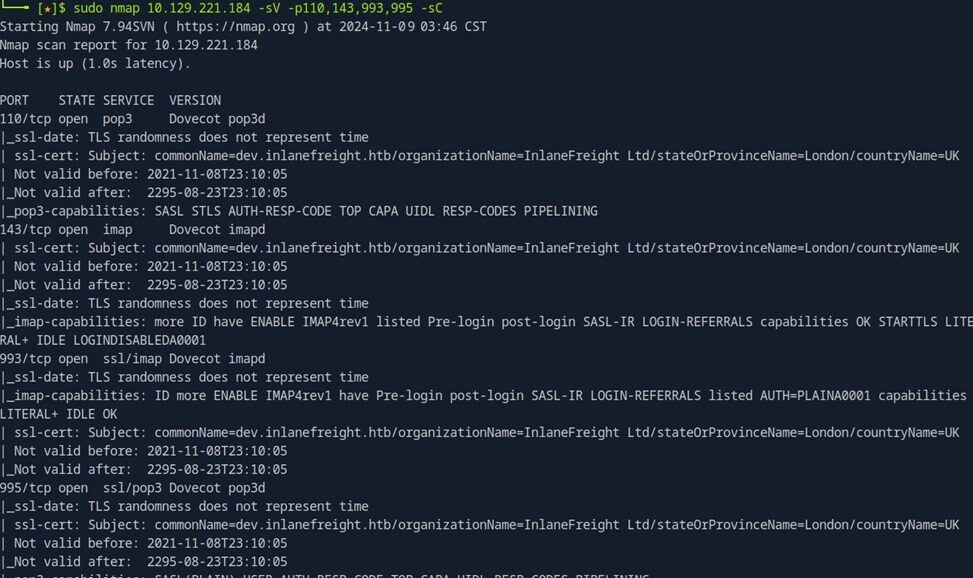
- Scan for Services using Nmap
sudo nmap 10.129.221.184 -sV -p110,143,993,995 -sC
2. Try to connect to the IMAP Server
openssl s_client -connect 10.129.221.184:993
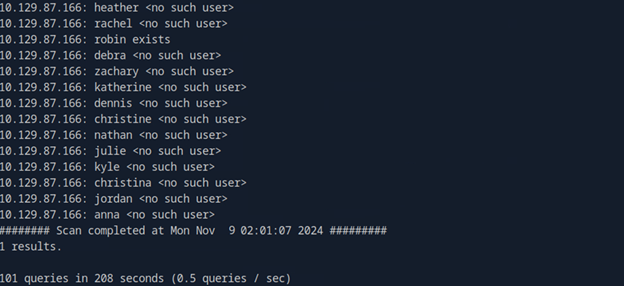
3. Log in to the server using the account found in the earlier smtp-user-enum scan: Username: robin, Password: robin.
a001 LOGIN robin robin
- a001: This is the tag for the request. It is used to identify the particular command in the response from the server.
- LOGIN: This is the IMAP command to authenticate the user.
- robin: The first occurrence of "robin" is the username.
- robin: The second occurrence is the password.
4. List Mailboxes:
a002 LIST "" "*"
- LIST: This is the IMAP command to list mailboxes. It tells the server to return a list of mailboxes available for the authenticated user.
- "": The first parameter is the "reference name." It is typically used for hierarchical mailbox structures. An empty string (
"") here means the command is not restricted to any specific hierarchy. - "*": The second parameter is the "mailbox pattern." The asterisk (
*) is a wildcard character, meaning "match all mailboxes."
5. Select the Mailbox
a004 SELECT "DEV.DEPARTMENT.INT"
- SELECT: The
SELECTcommand is used to select a mailbox (folder) for operations like fetching, searching, or modifying messages within that mailbox. Once a mailbox is selected, other IMAP operations are performed in the context of that mailbox. - "DEV.DEPARTMENT.INT": This is the name of the mailbox to be selected. The mailbox is specified using its full name. In this case, the mailbox is a nested folder structure, likely representing a hierarchy of folders under
DEV.DEPARTMENT.INT.
6. Search for Emails
a006 SEARCH ALL
- SEARCH: This command is used to search for messages that match certain criteria. In this case, there is no specific criterion, so it will search for all messages.
- ALL: This is the search criterion. When the
ALLkeyword is used, it instructs the server to return all messages in the selected mailbox.
7. a007 FETCH 1 (RFC822)
a007 FETCH 1 (RFC822)
- FETCH: This command is used to retrieve specific message data from the mail server.
- 1: This specifies the message ID or UID (in this case, message number 1). The message ID is used to select which message to retrieve.
- (RFC822): This indicates that the server should return the message in the format defined by the RFC 822 standard, which is the email message format used for headers and body content.
*Please refer to the image below, which illustrates the steps commands from 3 to 7
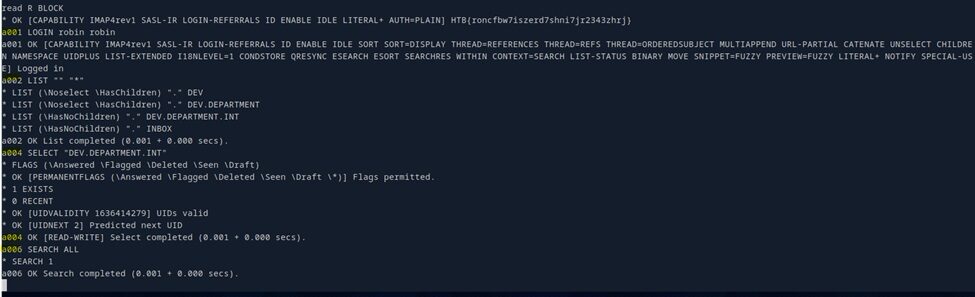
*** Email retrieve from the server ***

🗝️ Key lessons learned and concepts on SMTP, IMAP, and POP3:
First, we covered the basics and the ports used by the SMTP ,IMAP & POP3. Second, the importance of configuring strong passwords cannot be overstated as this lab demonstrated that the same username and password. Finally, we must consider how to protect systems against enumeration and scanning techniques. See the links below for guidance on securing Postfix."
https://security-24-7.com/hardening-guide-for-postfix-2-x
https://www.ninjaone.com/blog/email-server-security-best-practices
Want to learn more and gain hands-on experience? Sign up with HTB Academy by clicking the link below

