Introduction to Digital Forensics

Part 1 - Introduction
Interpol defines digital forensics as a branch of forensic science focused on identifying, acquiring, processing, analyzing, and reporting electronically stored data. This data, from sources like computers and smartphones, is crucial for law enforcement and must be handled meticulously to be admissible in court. This key element of digital forensics is the Chain of Custody, which tracks evidence from collection through analysis by documenting each handler, transfer time, and purpose.
In this course, we will explore tools to understand key concepts, basics, and practical aspects of digital forensics.
Part 2 - Linux CLI
File Command
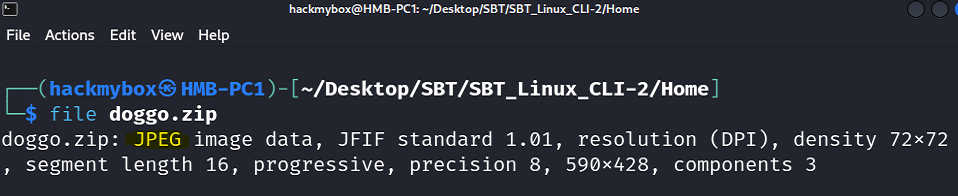
In the course challenge, we need to find files with modified extensions to conceal their content. The file command in Linux analyzes a file's content header to reveal its actual type. From the sample below, you can see that doggo.zip is actually a JPEG image. For more information about the file command, see the resources below.
Tree Command
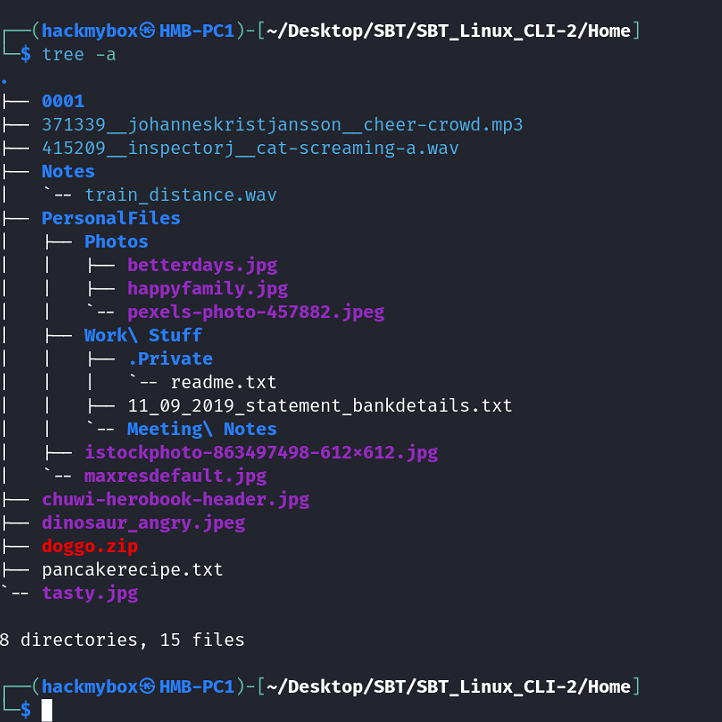
A simple yet useful command in Linux is the tree command. It displays the filesystem hierarchy in a visually structured format directly from the command line. -a show all files (Including Hidden).
Part 3 - Steganography
Steganography is a method that hides sensitive information within an ordinary, non-secret file or message, making it undetectable. Once the file or message reaches its destination, the sensitive data can be extracted, ensuring it remains securely hidden throughout the process.
From a cybersecurity perspective, threat actors can use steganography to embed malicious data within seemingly normal files.
From concealing malicious payloads, ransomware, malvertising, and similar tactics use the same concept to hide and plant malicious code.
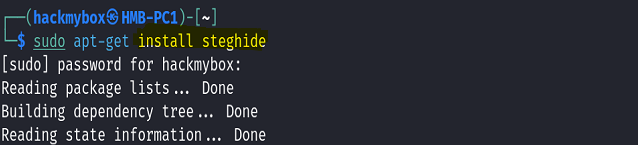
- Install Steghide
2. Then we create a ZIP file from the folder we want to embed, naming it Secret.zip.
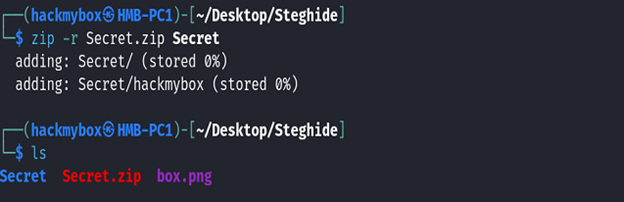
3. The next command takes Secret.zip, hides it within box.jpeg, and creates a new image called box2.jpeg, which will now contain the hidden file.
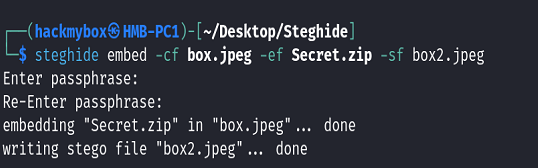
Here’s a breakdown of the command:
steghide: This is the command-line tool used for steganography, which is the practice of hiding files within other files, typically images or audio files.
embed: This is the operation you're performing, which is to hide a file inside another file.
-cf box.jpeg: This specifies the cover file (the image that will contain the hidden file). In this case, box.jpeg is the image that will have the hidden data.
-ef Secret.zip: This specifies the embedded file (the file you want to hide). Here, Secret.zip is the file that will be hidden inside the cover image.
-sf box2.jpeg: This specifies the output file (the new image that will contain the hidden file). box2.jpeg is the resulting image that will be created, which contains Secret.zip hidden within it.
4. Now we copy and save box2.jpeg. As you can see, the picture looks like a normal JPEG file.
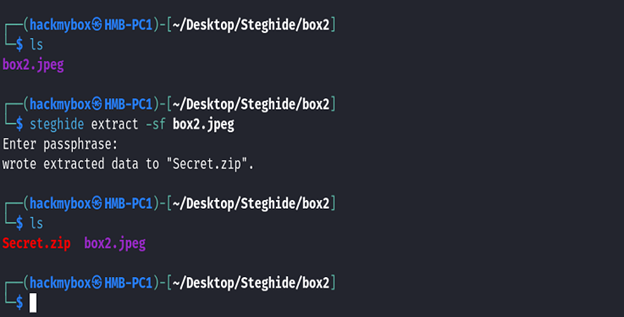
4. We can then use the command steghide extract -sf box2.jpeg is to extract hidden data from the image file box2.jpeg.
Part 4 - Cracking ZIP Files
fcrackzip is a password cracker for ZIP files that offers options for cracking passwords using brute force or dictionary attacks.
- To install type in command sudo apt install fcrackzip.
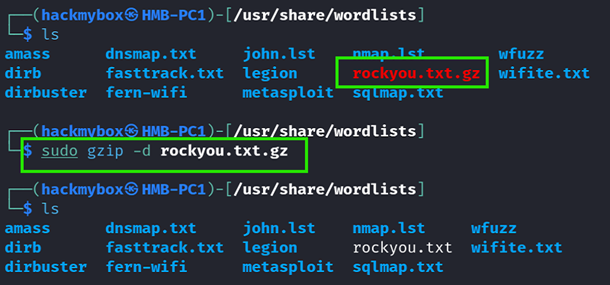
- Kali Linux often comes with the rockyou.txt wordlist pre-installed. It is typically located in the /usr/share/wordlists/directory. Follow the command below to decompress it.
- To run fcrackzip see command below.
Breakdown of the Command
-D : specifies a dictionary attack
-u : use the unzip format, for compatibility with different ZIP compression
-p /usr/share/wordlist/rockyou.txt : This specifies the path to the rockyou.txt file.
DictionaryAttack.zip : target ZIP file we want to crack.